Zero-Day Vulnerabilities Demystified: Understanding the Threat and How to Stay Protected

Welcome to our exploration of Zero-Day Vulnerabilities in the realm of cybersecurity. In an era where digital threats evolve at an unprecedented pace, understanding these elusive vulnerabilities is paramount for safeguarding our digital infrastructure and personal data.
In this article, we'll delve into the enigmatic world of Zero-Day Vulnerabilities, shedding light on what they are, how they're discovered and exploited, and the profound impact they can have on our online security. Furthermore, we'll explore strategies to mitigate the risks associated with Zero-Day Vulnerabilities, equipping you with the knowledge and tools necessary to bolster your defenses in an ever-changing threat landscape.
So, join us on this journey as we unravel the mysteries surrounding Zero-Day Vulnerabilities and empower ourselves with the insights needed to navigate the complex terrain of modern cybersecurity.
Let's dive in!
Part 1: Understanding Zero-Day Vulnerabilities
Definition of Zero-Day Vulnerabilities
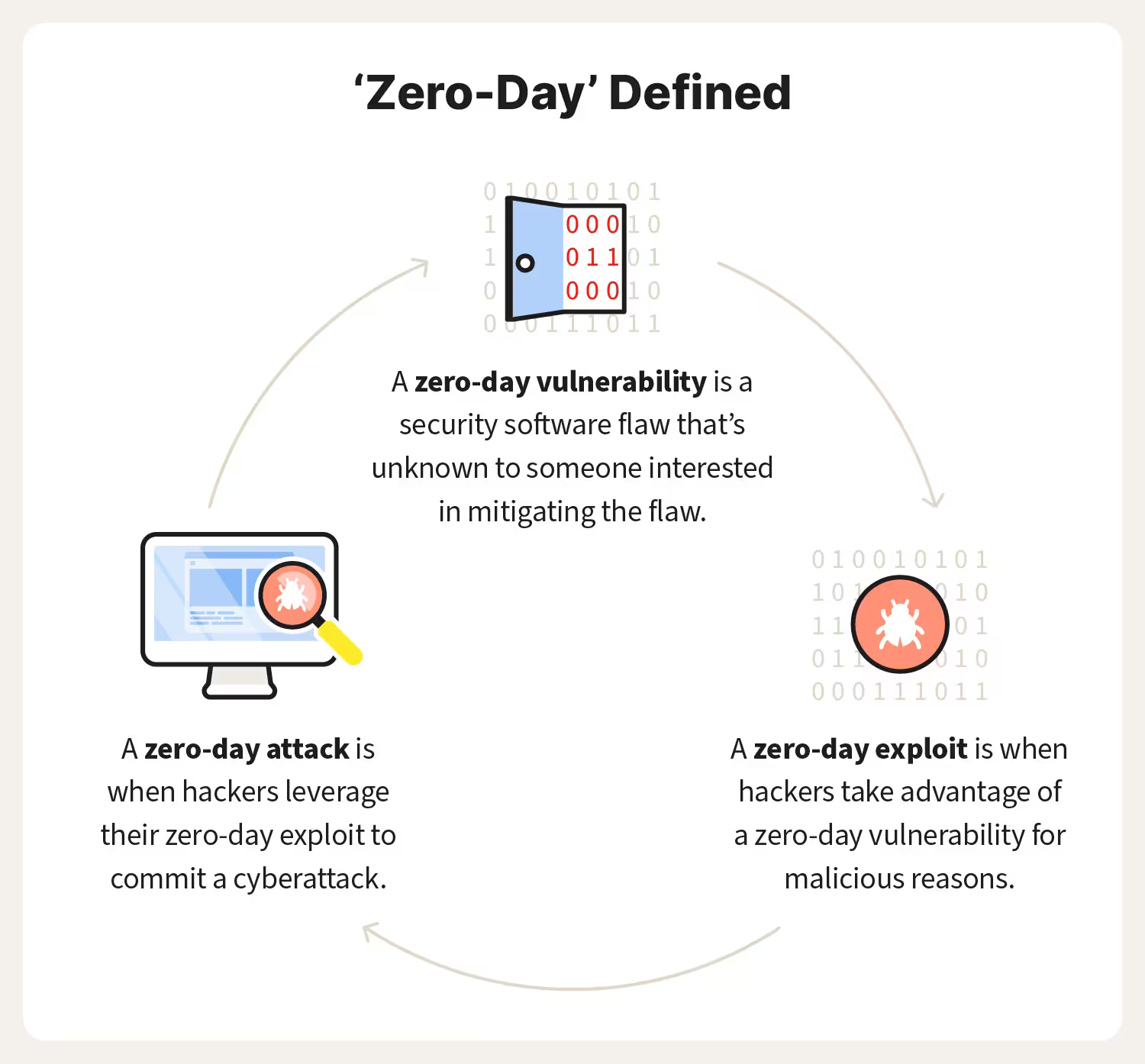
Zero-Day Vulnerabilities refer to software vulnerabilities that are unknown to the vendor or developer, leaving users susceptible to exploitation by malicious actors. The term "Zero-Day" signifies that there are zero days of protection against these vulnerabilities since they are exploited before the vendor can release a patch or update to fix them. These vulnerabilities often lurk undetected in software code, providing attackers with a window of opportunity to launch targeted cyber attacks, such as malware infections, data breaches, or system compromises.
Importance and Associated Risks
The significance of Zero-Day Vulnerabilities stems from their potential to inflict widespread damage across digital ecosystems. Unlike known vulnerabilities, which can be patched through security updates, Zero-Day Vulnerabilities offer no immediate recourse for defense, leaving organizations and individuals vulnerable to exploitation. The risks associated with Zero-Day Vulnerabilities are multifaceted. They can be leveraged by cybercriminals to infiltrate networks, steal sensitive information, disrupt critical infrastructure, and undermine the integrity of systems and data. Moreover, the covert nature of Zero-Day Vulnerabilities often allows attackers to evade traditional security measures, making them particularly insidious threats in today's cyber landscape.
Understanding the characteristics and implications of Zero-Day Vulnerabilities is essential for devising effective cybersecurity strategies and mitigating the risks they pose to individuals, businesses, and society as a whole.
Part 2: Exploring Zero-Day Vulnerabilities
Discovering and Exploiting Zero-Day Vulnerabilities
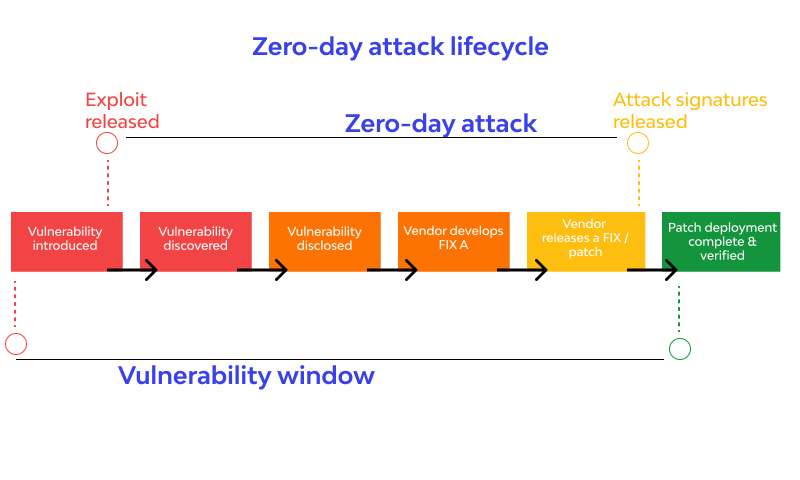
Zero-Day vulnerabilities are often discovered by security researchers or hackers who identify weaknesses in software code that can be exploited for malicious purposes. These vulnerabilities can remain undisclosed for extended periods, allowing attackers to capitalize on them before developers have a chance to implement patches or fixes. The exploitation of Zero-Day vulnerabilities can lead to devastating consequences, including data breaches, financial losses, and reputational damage.
Impact on System and Data Security
The exploitation of Zero-Day vulnerabilities can have far-reaching implications for system and data security. Attackers can use these vulnerabilities to gain unauthorized access to networks, compromise sensitive information, and disrupt critical operations. Moreover, the covert nature of Zero-Day attacks makes them difficult to detect and mitigate, leaving organizations vulnerable to prolonged periods of exploitation and damage.
Historical Examples

Throughout history, there have been numerous high-profile incidents involving Zero-Day vulnerabilities. For example, the Stuxnet worm, discovered in 2010, exploited multiple Zero-Day vulnerabilities to target and sabotage Iran's nuclear facilities. Similarly, the WannaCry ransomware attack in 2017 exploited a Zero-Day vulnerability in the Windows operating system to infect hundreds of thousands of computers worldwide. These incidents underscore the significant impact that Zero-Day vulnerabilities can have on global cybersecurity and highlight the ongoing challenge of defending against them.
Exploring the discovery, exploitation, and impact of Zero-Day vulnerabilities provides valuable insights into the evolving threat landscape and the importance of proactive cybersecurity measures. By understanding the nature of these vulnerabilities and their potential consequences, organizations can better prepare themselves to defend against emerging threats and safeguard their digital assets.
Part 3: Mitigating Zero-Day Vulnerabilities
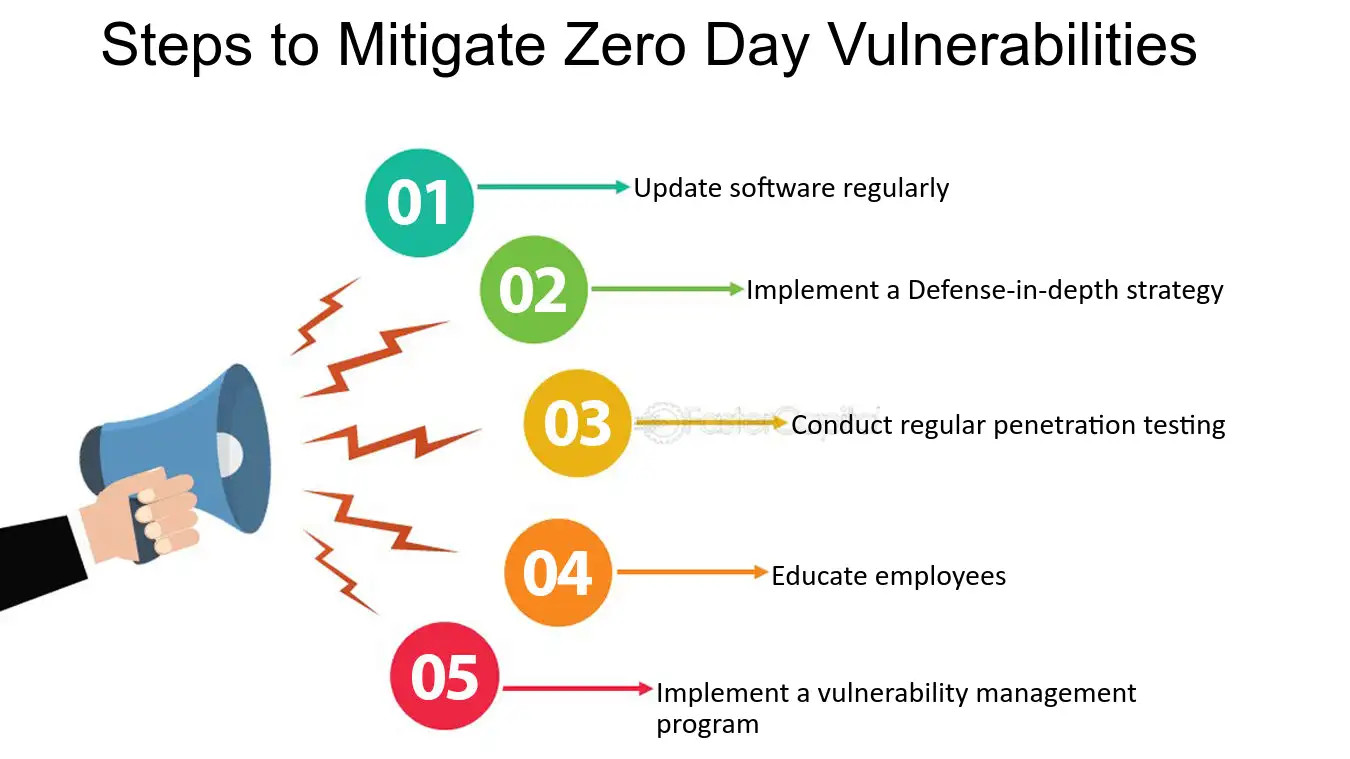
Keeping Systems and Software Updated
One of the most effective ways to mitigate the risk of Zero-Day vulnerabilities is to ensure that systems and software are regularly updated with the latest security patches and fixes. Developers often release patches in response to newly discovered vulnerabilities, so keeping software up to date can help prevent attackers from exploiting known weaknesses.
Using Proactive Security Solutions
Proactive security solutions, such as intrusion detection systems (IDS), endpoint protection platforms (EPP), and threat intelligence services, can help organizations identify and respond to Zero-Day attacks in real-time. These solutions use advanced algorithms and machine learning techniques to detect anomalous behavior and potential security threats, enabling organizations to take proactive measures to mitigate risks.
Recommended Security Practices for Users and Businesses
In addition to technical solutions, implementing robust security practices can help mitigate the risk of Zero-Day vulnerabilities. This includes practices such as regularly backing up data, implementing strong access controls, educating users about potential security risks, and conducting regular security audits and assessments. By adopting a multi-layered approach to security, organizations can reduce their exposure to Zero-Day attacks and minimize the potential impact of security breaches.
Mitigating Zero-Day vulnerabilities requires a combination of technical solutions, proactive security measures, and user awareness. By implementing these strategies, organizations can strengthen their security posture and better protect themselves against emerging threats in the ever-evolving landscape of cybersecurity.
Conclusion
In conclusion, Zero-Day vulnerabilities represent a formidable challenge in the field of cybersecurity, posing significant risks to individuals, businesses, and society as a whole. These vulnerabilities, by their very nature, exploit weaknesses in software code before developers have a chance to address them, making them particularly insidious threats in today's digital landscape.
Throughout this article, we've explored the definition and implications of Zero-Day vulnerabilities, delved into their discovery and exploitation, and discussed strategies for mitigating their impact. We've seen how Zero-Day vulnerabilities can lead to data breaches, financial losses, and reputational damage, highlighting the critical importance of proactive cybersecurity measures.
While the discovery and exploitation of Zero-Day vulnerabilities are inevitable in today's interconnected world, organizations can take steps to mitigate their impact. By keeping systems and software updated, using proactive security solutions, and implementing recommended security practices, organizations can strengthen their defenses against Zero-Day attacks and reduce their exposure to potential risks.
Ultimately, combating Zero-Day vulnerabilities requires a collaborative effort from all stakeholders, including developers, security researchers, and end-users. By working together to identify, address, and mitigate Zero-Day vulnerabilities, we can build a safer and more secure digital environment for everyone.
Thank you for joining us on this journey to understand Zero-Day vulnerabilities and their implications for cybersecurity. Together, let's continue to stay vigilant and proactive in the ongoing battle against cyber threats.
