Wi-Fi Isn’t Dead: Advanced Wireless Attacks in 2025 (and How to Ethically Simulate Them)

So, you thought Wi-Fi hacking was a relic of the past?
Maybe something left behind with WEP and cheap pineapple toys?
Think again. 😈
In a world obsessed with cloud exploits and AI vulnerabilities, wireless attacks have quietly evolved — sharper, stealthier, and surprisingly relevant. Modern pentesters are rediscovering the power of the invisible battlefield: the air around us. 📡
This isn't a nostalgia trip into packet sniffing and rainbow tables.
This is next-gen wireless hacking — from PMKID manipulation to Evil Twin 2.0, from mesh network mischief to IoT side-channel espionage.
In this post, you won't just learn how to crack, but how to simulate, secure, and understand wireless attacks like a 2025 red teamer. 🧠💻
Ready to jam some signals (ethically)?
Let's break it down — one frequency at a time. ⚡
1. Introduction: Why Wi-Fi Hacking Still Matters in 2025
For years, the cybersecurity spotlight has shifted toward cloud platforms, supply chain attacks, and AI manipulation — and rightfully so. But in the shadows, Wi-Fi quietly persists as a critical (and often vulnerable) layer in both corporate and personal networks. And here's the kicker: most people still treat it like it's 2012. 🕰️
While WPA3 promised a new era of wireless security, adoption has been inconsistent, implementations are flawed, and users still fall for rogue access points like moths to flame. With the explosion of IoT devices, smart home tech, and mesh Wi-Fi systems, the attack surface has only widened — and traditional defenses haven't caught up.
Let's bust a few myths real quick:
-
Myth: WPA3 makes Wi-Fi hacking obsolete.
Reality: Downgrade attacks and flawed implementations still expose WPA3 networks. -
Myth: Wireless attacks are too noisy for real pentests.
Reality: Tools like hcxdumptool and targeted deauths allow surgical precision with minimal detection. -
Myth: Physical proximity limits wireless threats.
Reality: With high-gain antennas, drones, and directional jamming, range is a solvable problem.
In short, Wi-Fi remains one of the most overlooked vectors in offensive security today — not because it's outdated, but because too many assume it is.
Whether you're red teaming an office, auditing a client's smart building, or training for bug bounties, wireless needs to be back on your radar. This guide will show you exactly why — and how — to use it responsibly and effectively.
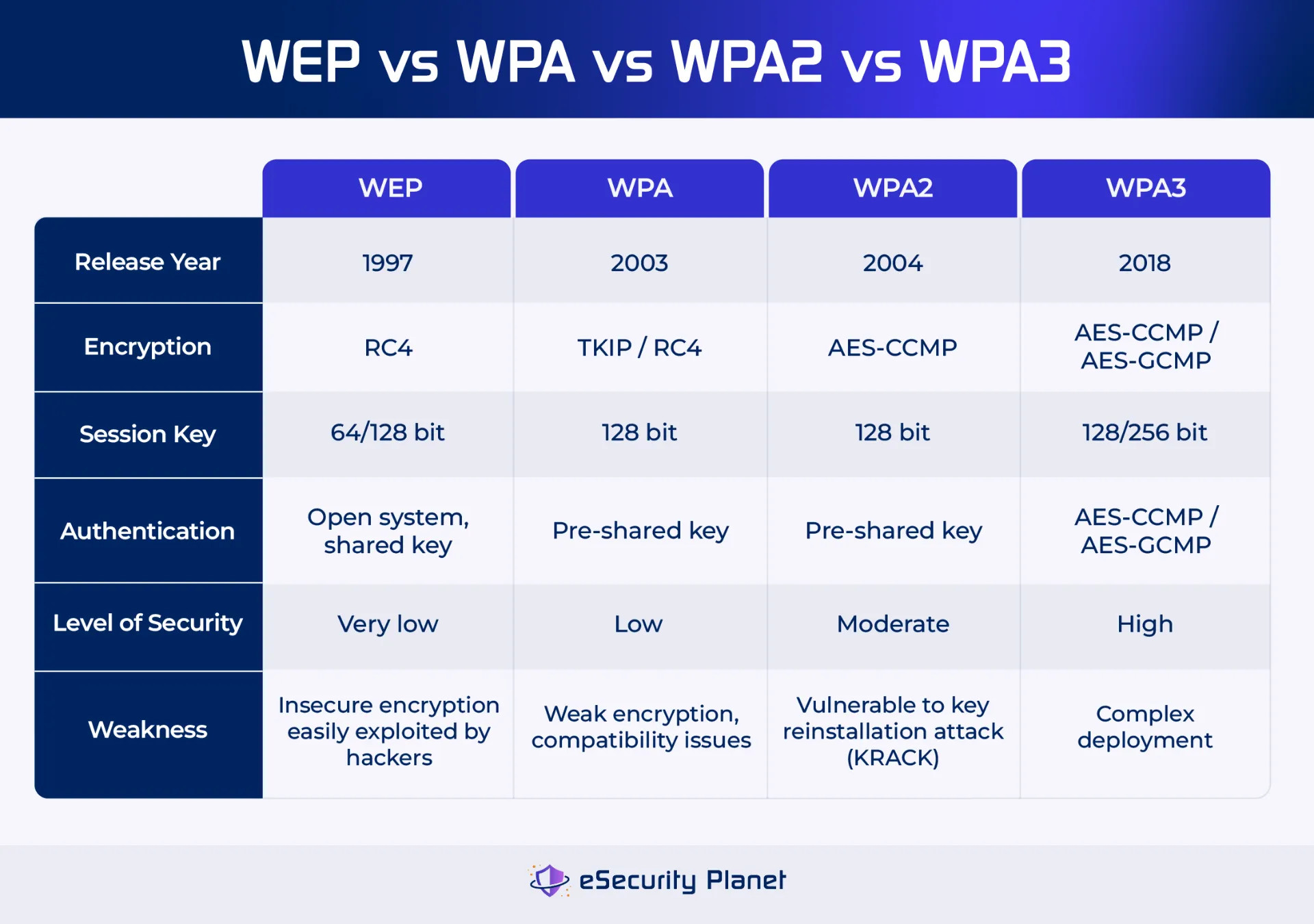
2. Understanding WPA3: Protections and Weak Spots
When WPA3 hit the scene, it was hyped as the long-awaited answer to decades of Wi-Fi insecurity. And to be fair, it did fix a lot — ditching pre-shared key vulnerabilities, using Simultaneous Authentication of Equals (SAE) instead of PSK handshakes, and offering forward secrecy out of the box.
But here's the uncomfortable truth:
WPA3 is only as strong as its implementation — and most are weak. 🧱🧠
Let's break down what WPA3 gets right, and where it still bleeds:
✅ WPA3 Improvements Worth Noting
-
SAE (Dragonfly handshake): Resists offline dictionary attacks and doesn't leak handshake material like WPA2.
-
Forward Secrecy: Even if credentials are later compromised, past sessions remain secure.
-
192-bit security mode: Optional enterprise-grade protection using Suite-B algorithms.
-
Individualized Data Encryption: Even on open/public Wi-Fi, traffic can be uniquely encrypted per client (OWE / Enhanced Open).
❌ But Then, the Cracks Appear...
-
Downgrade Attacks:
Many devices fall back to WPA2 if WPA3 isn't available — and attackers can force that fallback. This defeats the entire point of upgrading. -
Dragonblood Vulnerabilities:
In 2019, researchers showed that SAE was vulnerable to side-channel and downgrade attacks, using flaws in how it was implemented — not in the standard itself. -
Poor Vendor Support:
Router manufacturers often ship firmware with outdated libraries, weak random number generators, or default misconfigurations. -
Enterprise Misconfigurations:
WPA3-Enterprise mode is powerful, but often misused — combining outdated RADIUS settings, insecure EAP types, or skipping certificate validation.
⚠️ The Pentester's Takeaway

Just because a target advertises "WPA3" doesn't mean it's safe. As an ethical hacker, your role is to:
-
Identify fallback behavior (does it drop to WPA2 under pressure?).
-
Detect poor SAE implementations (are timing differences exploitable?).
-
Exploit hybrid deployments (mixed WPA2/WPA3 clients = wider surface).
-
Log and report insecure enterprise EAP setups.
WPA3 is not unbreakable — it just changed the rules of the game.
Up next, we'll look at modern attack vectors built for this new era. 🧨
3. Modern Attack Vectors: Beyond the Old School
Forget the WEP crackathons and lazy WPA2 dictionary attacks — those days are gone. The wireless threat landscape in 2025 is sharper, sneakier, and tailored to modern infrastructure. This section dives into the most effective and current Wi-Fi attack vectors that ethical hackers use today — all of them relevant in real-world pentests.
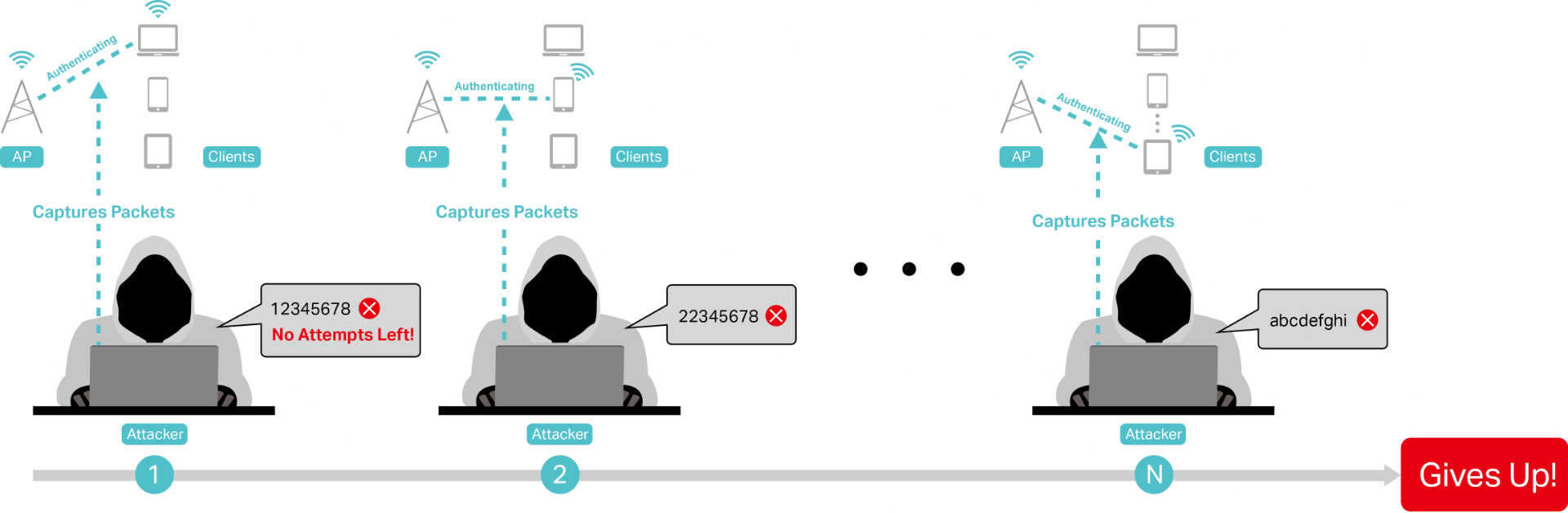
🔓 1. PMKID Attacks – Reborn for WPA3-Transition Networks
The classic PMKID-based hash capture still works — especially in networks that use WPA2 or have a mixed WPA2/WPA3 deployment.
Attackers capture a single frame without requiring a 4-way handshake, using tools like hcxdumptool or bettercap.
Then, offline cracking begins.
⚠️ Many networks "support" WPA3, but clients still connect using WPA2 — a goldmine for PMKID extraction.
🧯 2. WPA3 Downgrade Attacks (Forced Fallback)

When a network supports both WPA2 and WPA3, a malicious actor can jam WPA3 traffic and force the client to reconnect using WPA2.
This allows for standard WPA2 attacks (like handshake capture or Evil Twin).
Tools like Dragonblood include downgrade scripts, or you can script your own deauth loop + MITM combo.
🐉 3. Dragonblood Reloaded: Exploiting SAE Implementations
While SAE (Simultaneous Authentication of Equals) is strong by design, its implementation is the weak point.
Dragonblood exploits:
-
Side-channel leaks during password processing
-
Timing attacks during curve selection
-
Misuse of crypto primitives in embedded devices
✅ Use timing fuzzers or side-channel testing tools to check for flawed handshake handling in routers or APs.
🧪 4. Misconfigured Enterprise Networks (EAP Failures)
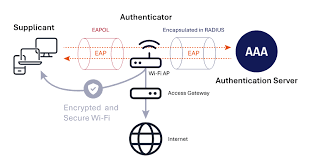
WPA2/3-Enterprise networks often rely on EAP (Extensible Authentication Protocol), which is notoriously misconfigured:
-
No server certificate validation: easy to spoof RADIUS and capture creds
-
PEAP/MSCHAPv2: susceptible to offline NTLM hash cracking
-
Weak inner authentication: open to downgrade and brute-force
Attack tools:
-
eaphammer
-
hostapd-wpe
-
Responder (in rogue AP scenarios)
🧿 5. Mesh Networks & Open Roaming Abuse
With mesh Wi-Fi gaining popularity (especially in corporate spaces), roaming behavior can be manipulated:
-
Forceful client reassociation
-
Fake mesh node injection
-
Credential leakage on failed roam attempts
Some vendors still don't enforce mutual authentication between nodes. That's exploitable.
📡 6. Targeted Deauthentication: Precision over Noise
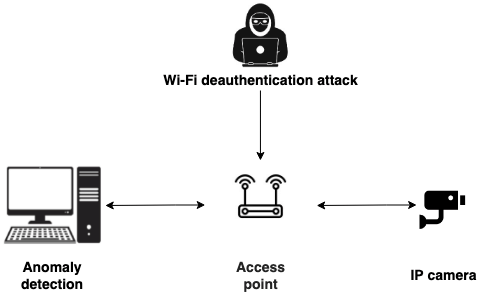
Instead of blasting the airwaves with deauth floods (noisy and illegal in most places), attackers now use:
-
Targeted deauths on specific MACs
-
Beacon stuffing to confuse client state
-
Channel switch attacks to stealthily disconnect or reroute clients
These cause disruption or force reconnection — where handshake captures and Evil Twins come into play.
🛠️ The Pentester's Role
As an ethical hacker, your mission isn't just to exploit — it's to simulate. These techniques:
-
Help blue teams validate real-world exposure
-
Let orgs test fallback behavior and implementation flaws
-
Educate teams on why "just enabling WPA3" isn't enough
In the next section, we'll break down the exact tools you need to perform these modern attacks ethically and safely. 👨💻🧰
4. Tools of the Trade: What Still Works, What's New
You can't wage war on the airwaves without the right arsenal.
Here's your updated, field-tested 2025 toolkit for ethical wireless hacking — a mix of classics, upgraded utilities, and cutting-edge tools tailored to modern networks.
🧨 1. hcxdumptool + hcxpcapngtool
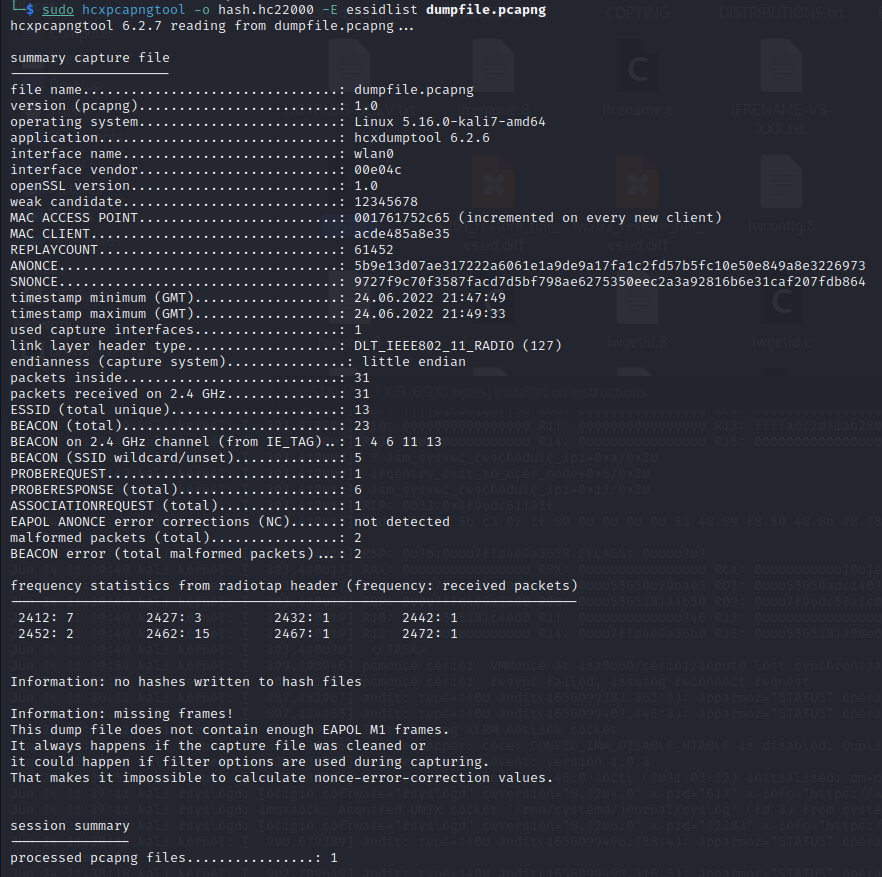
The go-to combo for capturing PMKIDs, handshakes, and probing advanced clients.
-
hcxdumptool actively attacks clients and APs to extract useful data (PMKID, EAPOL frames).
-
hcxpcapngtool converts captures into hashcat-compatible formats.
✅ Works great against mixed WPA2/WPA3 environments.
🛠️ Best used with: --enable_status=15 --filterlist_ap=yourlist.txt
🧠 2. Bettercap (WiFi Module)
This Swiss Army knife has matured massively. The Wi-Fi module supports:
-
Active deauth attacks
-
Rogue AP creation
-
Beacon flooding
-
Live packet manipulation
Great for scripted Evil Twin setups and injecting phishing portals.
🔧 Bonus: Integrates well with caplets and is extensible via scripts.
🐉 3. Dragonblood Toolkit
Specifically designed to exploit vulnerabilities in WPA3-SAE:
-
Timing attacks
-
Side-channel probes
-
SAE group negotiation exploits
Originally developed by Mathy Vanhoef (of KRACK fame).
Test how "secure" WPA3 implementations actually are.
🎭 4. WiFi-Pumpkin3
An advanced rogue AP framework for:
-
Captive portal attacks
-
Credential harvesting
-
DNS spoofing
-
Session hijacking (via iframe injection or JavaScript payloads)
🚨 Use in controlled lab environments — can easily become illegal outside.
📡 5. airgeddon
Still alive and evolving! A multi-attack framework that:
-
Captures WPA/WPA2 handshakes
-
Launches Evil Twin attacks with captive portals
-
Integrates with hashcat and bettercap
-
Supports DoS, karma attacks, and more
💡 Ideal for orchestrating full-scale Wi-Fi assessments quickly.
📡 6. eaphammer
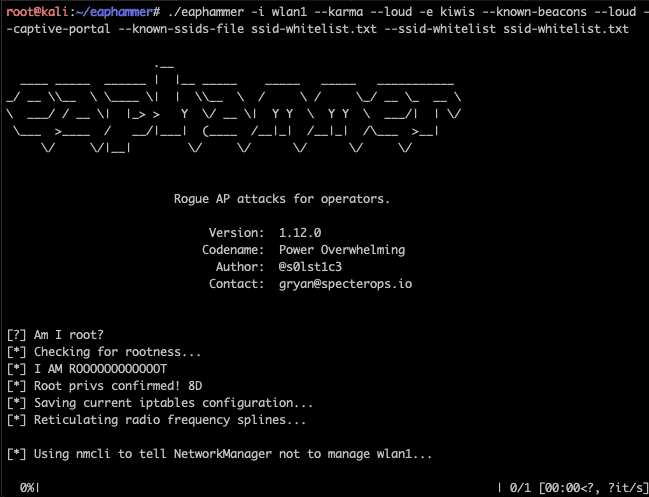
Targeted at WPA2/3-Enterprise networks.
Capabilities:
-
Fake RADIUS + rogue AP combos
-
Harvest domain credentials (MSCHAPv2 downgrade)
-
Simulate full Evil Twin against corp-level setups
🔐 If your target uses 802.1X or RADIUS, this is mandatory gear.
👁️ 7. Kismet (for recon & passive mapping)
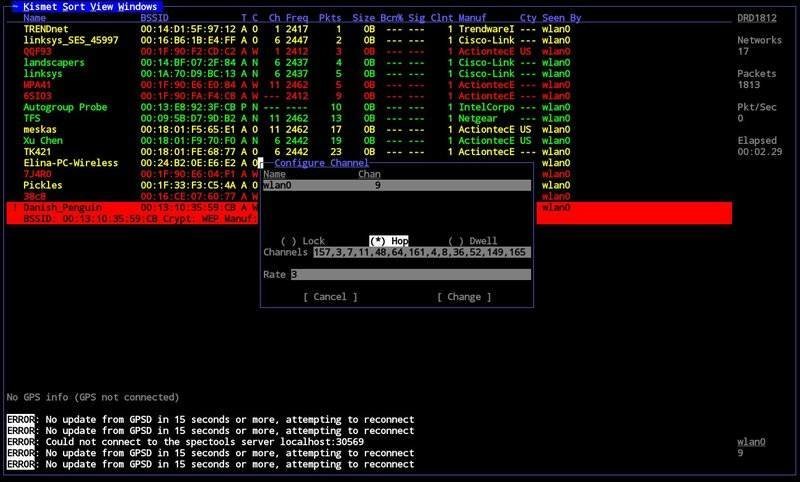
While not an attack tool per se, Kismet is your aerial radar:
-
Passive network mapping
-
Channel hopping
-
Client/AP relationship tracking
-
GPS logging for war driving or audits
✈️ Pair with a directional antenna for serious reconnaissance.
⚙️ Hardware Recommendations
You'll want:
-
Alfa AWUS036ACH or similar for dual-band injection
-
Raspberry Pi 4 or laptop with Kali/Parrot
-
High-gain antenna or Yagi for distance attacks
-
Optional: Wi-Fi dev boards (ESP32) for rogue AP emulation or scripting
🛑 Legal Reminder:
Always test on networks you own or have explicit permission to audit. These tools can cause real disruption or legal consequences if misused.
Next up, we'll deep-dive into Evil Twin 2.0, where rogue access points become surgical tools for modern red teams. 🕵️♂️📶
5. Evil Twin 2.0: Rogue APs in 2025
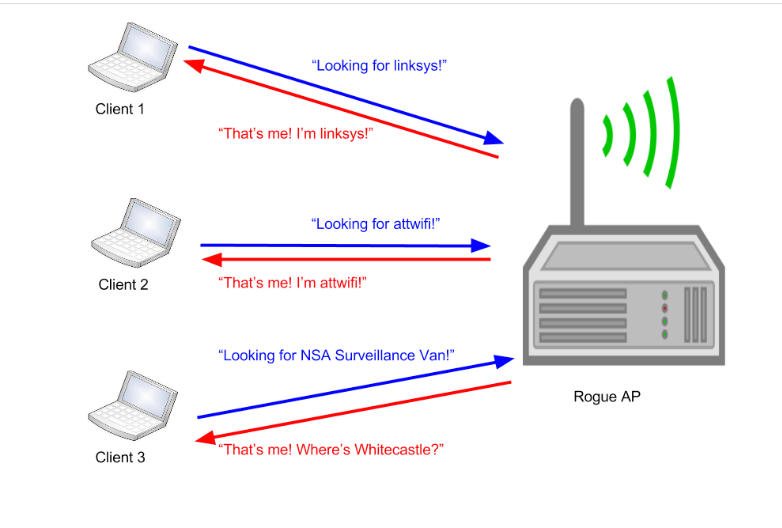
The classic Evil Twin attack — setting up a fake access point to trick users into connecting — is far from obsolete. In fact, in 2025, it's more powerful and flexible than ever… if you do it right.
Forget the noisy "create AP and hope someone bites" method. The modern Evil Twin is stealthy, tailored, and deeply integrated with social engineering and phishing frameworks.
🧠 Why It Still Works (and Works Better)
-
Auto-reconnect behavior in devices makes them switch to a stronger signal instantly.
-
Captive portal fatigue means users click "Accept" without thinking.
-
Users rarely verify SSIDs, and mobile devices often auto-join open or remembered networks.
⚔️ Modern Evil Twin Techniques
🔹 Captive Portal Phishing
Deploy fake login portals that mimic real services (e.g., Starbucks, Cisco, Office 365).
Tool combos:

-
WiFi-Pumpkin3 + BeEF (browser hooking)
-
Bettercap + custom HTML phishing page
-
Airgeddon + captive portal template
🧪 Pro tip: Use DNS spoofing to hijack all domains and force portal interaction.
🔹 MAC Cloning + SSID Mirroring
Spoof the real AP's:
-
MAC address (BSSID)
-
SSID
-
Channel
Then slowly deauth clients until they latch onto your stronger fake.
This can be done using:
-
airbase-ng
-
hostapd
-
bettercap
🧠 Bonus: Use Kismet or airodump-ng first to fingerprint the real AP and clients.
🔹 Evil Twin with Enterprise Targets
Using tools like eaphammer, you can:
-
Spoof enterprise SSIDs (e.g., CorpNet-WPA3-Ent)
-
Clone RADIUS responses
-
Capture domain creds when users log in via PEAP/MSCHAPv2
🎯 Especially effective in environments where users don't validate server certs.
🛡️ Bypassing Client Protections
Modern OSes are smarter. You now need to:
-
Match SSID, channel, and encryption type
-
Provide internet access or a fake captive portal to avoid suspicion
-
Bypass HSTS via iframe injection or DNS spoofing
⚙️ Ethical Lab Setup
You can build your Evil Twin test lab using:
-
A Raspberry Pi 4 or laptop with dual Wi-Fi cards
-
hostapd-wpe or WiFi-Pumpkin3 as rogue AP
-
Fake DNS/DHCP using dnsmasq or ettercap
-
Controlled test devices (VMs or old phones)
🚨 Never test in open air unless inside a Faraday cage or isolated RF lab. Accidental connections are still a legal and ethical risk.
🔐 Defender's Tip
Blue teams should:
-
Enforce SSID whitelisting
-
Require cert validation on enterprise networks
-
Monitor for multiple APs broadcasting same SSID
-
Use WIDS/WIPS (Wireless Intrusion Detection/Prevention Systems)
The Evil Twin attack isn't dead — it's just evolved into a smarter predator.
Next, we'll show how IoT and smart devices create fresh opportunities for side-channel wireless attacks. 🕹️📶
6. Hacking IoT Over Wi-Fi: Side-Channel Attacks in the Smart Home 🧠📲
Smart TVs. Security cameras. Robot vacuums. Even the fridge.
All connected. All talking — mostly unencrypted — over Wi-Fi.
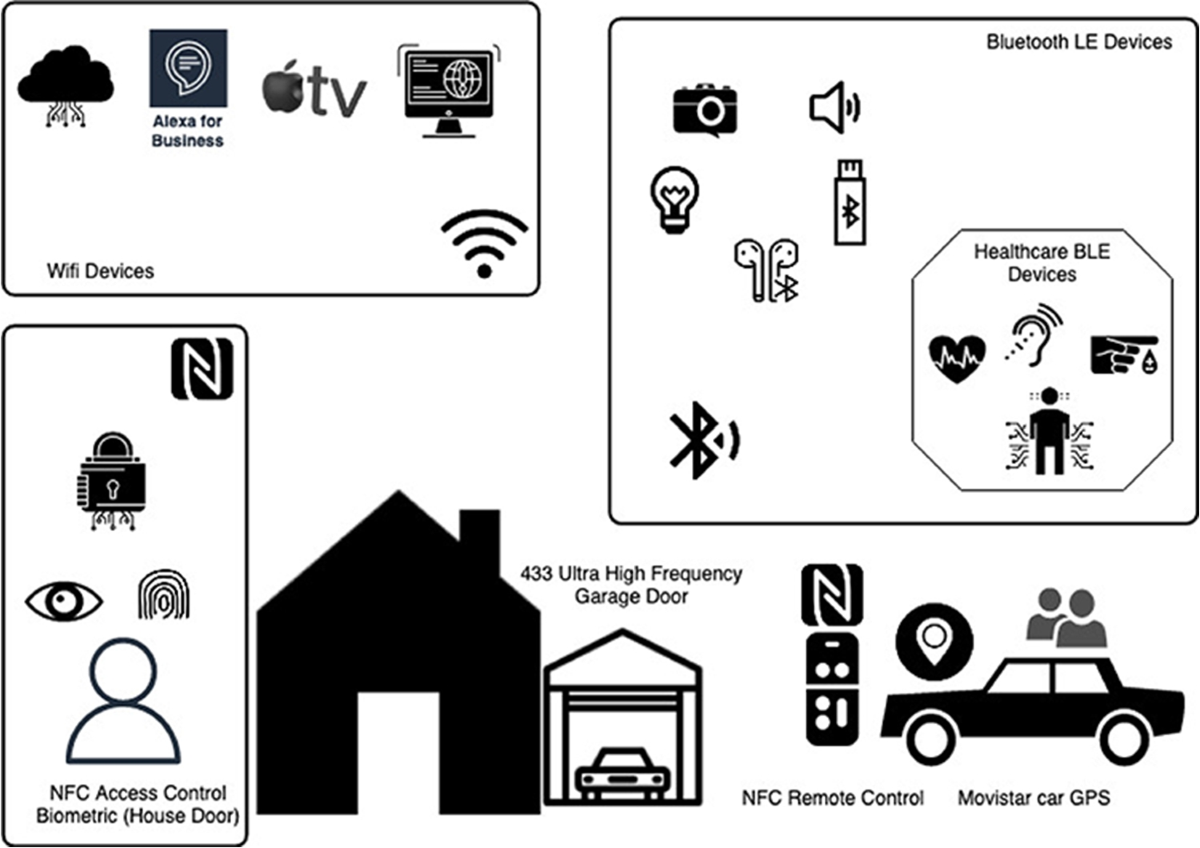
And most importantly:
Very few people are watching them. 👀
While traditional Wi-Fi hacking focuses on access points and clients, IoT introduces a new layer of wireless exposure — one that's often ignored during audits and assessments.
🔍 Why IoT = Easy Prey
-
Weak encryption or none at all
Many IoT devices still rely on outdated protocols (e.g., plain HTTP, Telnet, or UPnP). -
No segmentation
IoT and internal networks are often on the same VLAN — so popping a camera means pivoting to corporate assets. -
Poor update cycles
Some IoT firmware hasn't been patched in years — even if the router is up to date.
⚔️ Tactics for Ethical Wireless IoT Attacks
🔹 1. Passive Fingerprinting
Use airodump-ng or Kismet to identify:
-
Device vendors via MAC OUI (e.g., Espressif = ESP32/IoT)
-
Hidden SSIDs used in provisioning
-
Signal patterns unique to devices (e.g., consistent beacons every 500ms)
✅ Passive = zero disruption, ideal for recon.
🔹 2. Side-Channel Analysis (Timing & RF Patterns)
Even if the data is encrypted, patterns leak info:
-
Camera streams spike upload at regular intervals
-
Smart bulbs respond instantly to app commands = track control attempts
-
Voice assistants (e.g., Alexa) spike in specific bursts = detect usage
📡 Tools:
-
Wireshark + filtering by MAC
-
RTL-SDR for deeper radio fingerprinting
-
Wifiphisher for captive injection into unprotected IoT UIs
🔹 3. Rogue Provisioning Attacks
Some smart devices expose open Wi-Fi hotspots during setup (e.g., SmartPlug_Setup).
Attack vector:
-
Wait for a user to reset the device
-
Hijack the provisioning process by imitating the config app
-
Inject fake network settings or DNS
⚠️ Often works even if the final network is secured — initial setup is the weak spot.
🔹 4. Firmware Over-the-Air (FOTA) Abuse
Many devices fetch firmware updates over unvalidated HTTP.
Intercept traffic with:
-
Evil Twin + DNS spoofing
-
SSL stripping (on poorly designed firmware)
-
MITM tools like mitmproxy or Bettercap
🎯 Replace firmware links or inject payloads (for PoC only!).
🧪 Lab Simulation: "IoT Side-Channel Recon"
Try this ethical lab setup:
-
Smart bulb or plug (e.g., TP-Link, Tuya-based)
-
Packet sniffer (Kismet or Wireshark)
-
Simulated control actions from app
-
Analyze traffic spikes, unencrypted API calls, DNS queries
Can you detect when the light was turned on just from Wi-Fi traffic volume?
🛡️ Blue Team Takeaways
-
Isolate IoT on separate VLANs or SSIDs
-
Monitor for open or hidden provisioning networks
-
Enforce TLS and firmware signature validation
-
Disable unnecessary broadcast services (e.g., SSDP, mDNS)
IoT doesn't just expand the attack surface — it broadcasts it.
In the next section, we'll show how to build your own Wi-Fi pentest lab to ethically explore all these techniques — with zero legal risk. 🧪🔐
7. Building Your Ethical Wi-Fi Pentesting Lab: Zero Risk, Maximum Practice 🛠️🏠
Before diving into the wild world of Wi-Fi hacking on production networks, it's crucial to have a secure, controlled lab environment. This ensures you can test, experiment, and sharpen your skills without causing harm. Setting up an ethical pentesting lab for wireless attacks is simpler than you might think and provides a safe space to practice techniques like PMKID capture, Evil Twin attacks, and IoT fingerprinting.

🧰 Required Hardware
You don't need a huge investment in hardware. Here's what you'll need to set up your Wi-Fi pentest lab:
1. Wi-Fi Adapters
You'll need dual-band adapters that support monitor mode and packet injection. Some solid choices:
-
Alfa AWUS036ACH (Wi-Fi 5, strong signal strength, good for range testing).
-
TP-Link TL-WN722N (Affordable and widely compatible with Kali Linux).
-
Panda PAU09 (Compact, USB-powered, and supports 5 GHz).
2. Raspberry Pi (or Old Laptop)
A Raspberry Pi 4 makes an excellent pentesting machine when paired with a USB Wi-Fi dongle.
For a more powerful setup, use a laptop running Kali Linux, Parrot OS, or a custom pentesting distro.
3. Router with Custom Firmware (e.g., OpenWRT or DD-WRT)
Setting up your own Wi-Fi access point (AP) will allow you to configure your network exactly how you want it, whether simulating WPA2, WPA3, or an insecure open network for testing.
-
Install OpenWRT or DD-WRT for full control over your router's settings, including the ability to downgrade WPA3 to WPA2, change channels, or even spoof SSIDs.
4. IoT Devices
To simulate real-world attacks, pick up a few cheap smart devices:
-
Smart plugs
-
Security cameras (e.g., WyzeCam, TP-Link Kasa)
-
Smart bulbs or light switches
-
IoT thermostats (e.g., Nest or Ecobee)
These will help you test the side-channel attacks we discussed earlier.
🖥️ Software Setup
A combination of these tools will make your Wi-Fi pentest lab effective and realistic.
1. Kali Linux/Parrot OS
Install either Kali Linux or Parrot OS (both are pentesting-focused). Both distributions have pre-installed tools for Wi-Fi pentesting, such as aircrack-ng, bettercap, hcxdumptool, Kismet, and many others.
2. Wi-Fi Pentesting Tools
Make sure you have these tools installed:
-
aircrack-ng (for WPA2 cracking and handshake captures)
-
hcxdumptool + hcxpcapngtool (PMKID capture and offline cracking)
-
Bettercap (for Man-in-the-Middle, Evil Twin, and DNS spoofing)
-
Wireshark (for packet analysis)
-
Kismet (for passive scanning and map building)
-
eaphammer (for WPA2/3-Enterprise attacks)
-
airgeddon (multi-attack framework for WPA/WPA2 cracking)
-
hostapd (for rogue AP creation)
🏡 Lab Setup Example:
Step 1: Create a Virtual Network (Optional)
If you're using a laptop, you can create virtual machines (VMs) for different devices (e.g., Android, Windows, or macOS clients) using software like VirtualBox or VMware.
This simulates a heterogeneous environment, allowing you to test attacks against different OS types without needing physical hardware for each device.
Step 2: Configure Your Rogue AP
With hostapd, you can set up a rogue AP with a fake SSID that mimics your target's network. You can also simulate WPA3 by enabling the sae option in the configuration file and configure captive portals to simulate Evil Twin attacks.
Here's a simple hostapd config line for WPA2:
- interface=wlan0
- ssid=FakeNetwork
- driver=nl80211
- hw_mode=g
- channel=6
- auth_algs=1
- wpa=2
- wpa_key_mgmt=WPA-PSK
- wpa_passphrase=supersecurepassword
Step 3: Capture Traffic and Analyze with Wireshark
Once your rogue AP is running, use tools like airodump-ng to capture WPA2 handshakes, and Wireshark to analyze packet flows and detect any unencrypted data that IoT devices might leak.
Step 4: Simulate IoT Attacks
Set up devices like a smart plug or lightbulb and connect them to your rogue AP. Use Kismet to passively monitor their communications. You can track connection attempts, control commands, or even sniff unencrypted API calls.
Step 5: Automate Attacks with Bettercap
Bettercap allows you to inject malicious content into your network. With the following script, you can automate your Evil Twin and DNS spoofing attacks:
bashCopiarEditarbettercap -iface wlan0 -caplet /usr/local/lib/python3.7/dist-packages/bettercap/caplets/wifi.evil_twin
📊 Test Scenarios
-
Scenario 1: Man-in-the-Middle (MITM) IoT Devices:
Capture traffic between a phone and an IoT device (e.g., smart plug) and manipulate device behavior by injecting fake commands. -
Scenario 2: Cracking WPA2 with a Handshake Capture:
Capture a handshake and use aircrack-ng or hashcat to test your cracking abilities against real-world devices. -
Scenario 3: Rogue AP + Evil Twin Attack:
Set up a fake AP and a captive portal that mimics a popular service (like Starbucks Wi-Fi) to see how clients interact with your fake network.
🔐 Important Ethical Considerations
-
Isolate your test network from any real production networks.
-
Never conduct these attacks on any network you don't own or have explicit permission to test.
-
Always follow local laws and ethical guidelines.
With this lab setup, you can replicate and test many of the techniques we've covered in this article, all within a safe and controlled environment.
Feel free to experiment and improve your skills as an ethical pentester! 💻
8. Defending Against Modern Wi-Fi Attacks: Best Practices for 2025 🔐🛡️
As much as pentesters enjoy finding weaknesses in wireless networks, it's equally important for blue teams to understand how to secure their networks against these evolving threats. In 2025, attacks like Evil Twin, PMKID capture, and IoT exploitation are still highly effective, but we can mitigate them with proactive security measures. Below, we'll break down strategies to prevent common Wi-Fi attacks and harden devices against exploitation.
🔑 1. Strong Encryption Standards
WPA3: The New Standard
While WPA2 is still common, WPA3 provides a significantly stronger security foundation for Wi-Fi networks by using SAE (Simultaneous Authentication of Equals) for better key exchange protection. If your devices support WPA3, you must enable it. It prevents offline dictionary attacks that WPA2 is vulnerable to.
Why it works: WPA3 mitigates many of the risks that WPA2 faced, such as PMKID and brute-force cracking.
How to implement WPA3:
-
Ensure your router and access points support WPA3.
-
Switch your network to WPA3 if possible.
-
If you need backward compatibility, enable WPA2/WPA3 mixed mode.
🔐 2. Protecting Against Evil Twin Attacks
Network Segmentation
To thwart Evil Twin and rogue AP attacks, it's essential to segment your network, especially separating IoT devices from the rest of your personal or business devices.
-
IoT devices should reside on a separate VLAN or isolated SSID.
-
Guest networks should be isolated from your internal network and should not allow access to sensitive resources.
SSID Hiding & Monitoring
While not foolproof, SSID hiding can help deter casual attackers from easily spotting your network. However, advanced attackers can still sniff your network, so you must combine this with other defenses.
How to protect against Evil Twin:
-
Use WIDS/WIPS (Wireless Intrusion Detection/Prevention Systems) to detect unusual AP behavior or duplicate SSIDs.
-
Monitor rogue APs on your network using tools like Kismet or WiFi Explorer to alert when a duplicate SSID is broadcasting.
-
Enable 802.1X authentication to ensure that only authorized devices can connect to your network.
🔒 3. Secure Your IoT Devices
IoT devices are a goldmine for attackers due to their weak security. In 2025, most IoT devices still lack proper encryption and authentication. Here's how to protect your devices:
1. Change Default Passwords
Most IoT devices come with default passwords that are easy to guess. Change these to strong, unique passwords immediately.
2. Regular Updates
Ensure your IoT devices get firmware updates regularly. Check for security patches from manufacturers and apply them as soon as they're available. If your device doesn't have updates, consider replacing it.
3. Disable Unnecessary Services
Turn off any services or ports that are not needed (e.g., Telnet, UPnP, HTTP). This reduces the number of attack vectors.
4. Separate IoT Network
Place all IoT devices on a segmented network, separate from your primary computers and mobile devices. If one of them is compromised, the attacker will have a harder time reaching sensitive data.
💥 4. Use VPNs and Proxy Servers for Device Privacy
Encrypted Tunnels for Data
If your devices (especially IoT) are constantly communicating over the internet, ensure all traffic is routed through a VPN or proxy server. This prevents MITM attacks and data snooping by encrypting the traffic.
-
Set up a VPN for all internal devices or configure a secure proxy for your IoT devices.
-
Use HTTPS for web-based IoT interfaces (never HTTP), and ensure devices don't default to unencrypted communication.
🔍 5. Regularly Monitor Wi-Fi Traffic
Passive Monitoring
Constant monitoring of your wireless network can help you detect malicious activity early. By using Wi-Fi scanners or sniffers like Wireshark or Kismet, you can see rogue APs, unusual traffic patterns, and suspicious connections in real-time.
-
Set up alerts for unexpected devices joining your network.
-
Check for unauthorized access points that might be attempting to spoof your network.
Active Monitoring with WIDS/WIPS
Implement Wireless Intrusion Detection Systems (WIDS) or Wireless Intrusion Prevention Systems (WIPS) that continuously analyze your network for unusual activity, unauthorized APs, or clients.
⚠️ 6. Secure DNS and DHCP Settings
DNS Spoofing Mitigation
Many wireless attacks rely on DNS spoofing to redirect victims to malicious websites. Protect your network by:
-
Using DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT) to prevent DNS hijacking.
-
Deploying a DNS filtering service (e.g., Pi-hole) to block malicious websites and content.
DHCP Snooping
Enable DHCP snooping on your router to prevent unauthorized devices from assigning IP addresses on your network. This helps avoid rogue DHCP servers from hijacking your traffic.
🔓 7. Use Strong Authentication (RADIUS + 802.1X)
For enterprise networks or advanced users:
-
802.1X authentication ensures devices authenticate before they connect to the network. It's a much stronger defense than just relying on a simple WPA2 key.
-
Integrate RADIUS servers to handle centralized authentication and enforce stricter access controls.
🚨 8. Keep the Router Firmware Updated
Routers are a prime target for attackers, especially if they're running outdated firmware. Vulnerabilities in router software can lead to remote code execution or give hackers access to your entire network. Always keep your router's firmware up-to-date and make sure any security patches are applied immediately.
-
Check for firmware updates regularly, and consider using a router from a well-known vendor with good security practices.
-
Disable any unused administrative ports (e.g., HTTP, Telnet, SSH) on the router.
🧠 9. Educate Users and Create Awareness
A key aspect of defending against wireless attacks is human awareness. Users in your network must understand the risks and be trained to:
-
Avoid connecting to unknown Wi-Fi networks (e.g., coffee shop Wi-Fi).
-
Use VPNs when connecting to public networks.
-
Be cautious about captive portals and avoid entering sensitive information in unsecured environments.
🛡️ Final Thoughts
Securing your wireless network in 2025 is not just about using strong encryption and passwords — it requires multiple layers of defense, including network segmentation, secure IoT management, real-time monitoring, and user education.
By combining these best practices, you can minimize your risk and safeguard against the increasingly sophisticated attacks targeting Wi-Fi networks.
Conclusion: Mastering Wi-Fi Security with Ethical Hacking 🔐

As we've explored throughout this guide, Wi-Fi security is a dynamic and ever-evolving field, with attackers constantly refining their techniques. From capturing WPA2 handshakes to exploiting IoT vulnerabilities, the risks are real—but so are the solutions. Whether you're an aspiring pentester or a network administrator, understanding both the offensive and defensive aspects of Wi-Fi security is crucial for staying ahead of the curve.
By adopting the best practices for encryption, network segmentation, IoT security, and continuous monitoring, you can build strong defenses against a wide range of attacks. Moreover, creating a safe and controlled pentesting lab allows you to sharpen your skills without risk, preparing you for real-world scenarios.
Remember, ethical hacking isn't just about identifying vulnerabilities—it's about improving systems, hardening defenses, and ensuring the integrity of digital spaces. The ultimate goal is a more secure digital environment for everyone.
As you continue to experiment, learn, and implement these strategies, keep in mind that security is a journey, not a destination. By staying updated with the latest tools, techniques, and threats, you'll be better equipped to protect your networks and defend against potential attacks.
