Understanding Social Engineering in Cybersecurity

In today's digital age, cybersecurity threats are evolving at a rapid pace. While sophisticated technologies like firewalls, antivirus software, and encryption provide layers of protection, one critical vulnerability remains: human error. This is where social engineering comes into play, a method that manipulates human psychology to bypass security systems. Rather than attacking software or networks directly, social engineering preys on human emotions, behaviors, and decision-making processes. In this article, we'll explore the concept of social engineering, the most common types of attacks, and how to protect against them.
Psychological Manipulation in Social Engineering
At its core, social engineering is about psychological manipulation. Attackers use a variety of emotional triggers to deceive their targets, such as:
- Trust: People tend to trust authority figures or familiar organizations. Social engineers often pose as someone the victim knows or respects, like an IT technician, a co-worker, or even a family member.
- Curiosity: Humans are naturally curious, which attackers exploit by creating scenarios that provoke interest or urgency, such as fake offers, contests, or messages marked as "urgent."
- Fear or Urgency: A common tactic is to create a sense of urgency or fear (e.g., "Your account has been hacked! Act now to recover your data!"), pushing the victim to act without thinking.
- Greed or Incentive: Tempting people with offers of money, free services, or valuable items (such as "Click here to claim your prize!") can trick them into providing sensitive information.
By using these triggers, attackers can bypass the technological defenses of even the most secure systems by simply targeting the human element.
Types of Social Engineering Attacks
Social engineering comes in various forms, each designed to exploit different aspects of human behavior. Below, we dive deeper into some of the most common types of social engineering attacks.
1. Phishing
Phishing is the most well-known and widespread form of social engineering. In a phishing attack, an attacker impersonates a trusted entity (such as a bank, a government agency, or an online service provider) and sends fraudulent emails or messages to the victim. These emails usually contain malicious links, attachments, or requests for sensitive information like passwords, credit card numbers, or social security numbers.

For example, a typical phishing email might appear to come from your bank, warning you of "suspicious activity" on your account. The email prompts you to click a link to "verify your account," but the link leads to a fake website designed to steal your login credentials.
There are several subtypes of phishing:
- Spear Phishing: A more targeted form of phishing, spear phishing aims at specific individuals or organizations. Attackers often gather personal information (such as names, job titles, and email addresses) to make the email appear more legitimate.
- Whaling: This form of phishing targets high-profile individuals, such as CEOs or senior executives, with the goal of gaining access to highly sensitive corporate data.
- Clone Phishing: Attackers take a legitimate email that the victim has received before, clone it, and then replace any attachments or links with malicious ones, tricking the victim into clicking or downloading malware.
2. Baiting
Baiting attacks rely on the curiosity or greed of the victim. Attackers offer something enticing—like free music downloads, software, or movie streaming—to lure the target into taking action. The "bait" is typically infected with malware or designed to collect personal information.

A classic form of baiting involves leaving infected USB drives in public places like parking lots or coffee shops. An unsuspecting person may find the USB drive and, out of curiosity, plug it into their computer, unknowingly infecting their device with malware.
Online, baiting often takes the form of fake advertisements, downloadable software, or pop-ups that promise something valuable in exchange for clicking a link or completing a survey. Once the victim engages with the bait, they are either infected with malware or redirected to phishing websites.
3. Pretexting
In a pretexting attack, the attacker creates a fictional scenario, or "pretext," to deceive the target. The goal is to build enough trust with the victim to obtain sensitive information, such as login credentials or personal data. Unlike phishing, which typically relies on urgency or fear, pretexting is often more elaborate and may involve lengthy conversations or interactions.
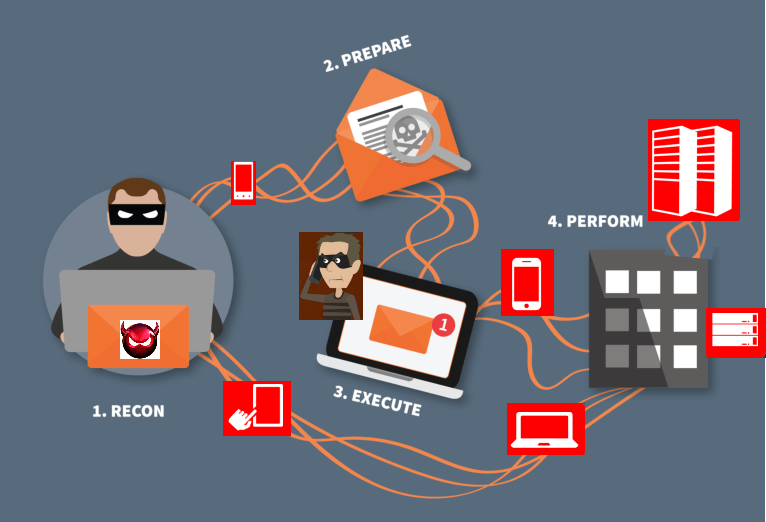
For example, an attacker might pose as a new employee in the company's IT department, asking existing employees for their passwords "for security purposes." Alternatively, they might pretend to be law enforcement or a financial institution representative, claiming that they need the victim's details to "verify their identity."
Key pretexting tactics include:
- Impersonating authority figures: Attackers might pretend to be a CEO or CFO, using a sense of hierarchy to pressure the victim into compliance.
- Using social knowledge: Some attackers research their victims on social media or through public records, using personal details (like birthdays, family names, or hobbies) to make the pretext more believable.
4. Quid Pro Quo
A quid pro quo attack involves an exchange of services. The attacker promises something in return for sensitive information or access to a system. For example, an attacker might pretend to be a technical support agent offering to help fix a computer problem in exchange for the victim's login credentials.
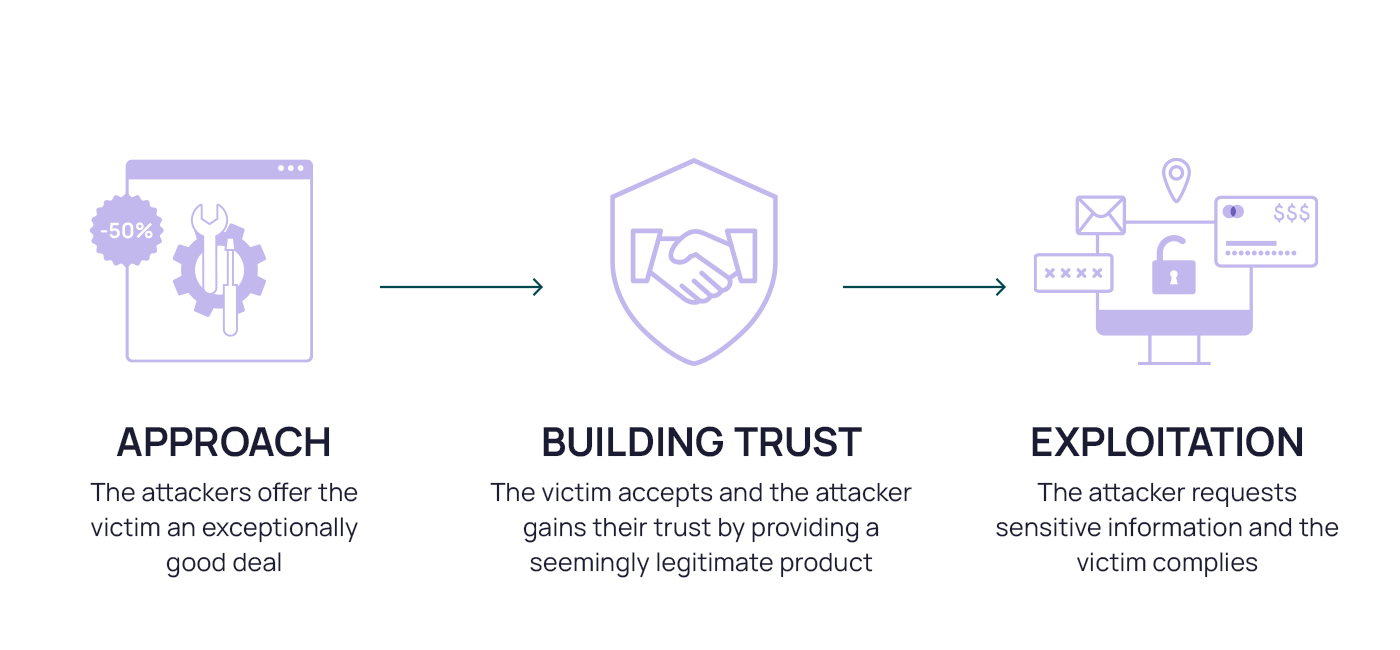
One real-world example of this type of attack occurred when attackers posed as IT professionals offering to help people restore lost internet connections. In exchange, they asked the victims to disable their antivirus software, which allowed the attackers to install malware.
In other cases, attackers might offer something like a software upgrade, a job opportunity, or even financial compensation in return for compromising the company's security.
5. Vishing and Smishing
Both vishing (voice phishing) and smishing (SMS phishing) are phone-based social engineering attacks. While the methods may differ, both rely on the same principles of manipulation and deception to gain sensitive information.

Vishing: In vishing attacks, attackers call the victim, pretending to be a trusted institution like a bank or government agency. They may claim that the victim's account has been compromised and urge them to provide personal details, like credit card numbers, PINs, or social security numbers, over the phone.
For example, a scammer might call posing as the IRS, claiming the victim owes back taxes and threatening legal action unless immediate payment is made.
Smishing: In smishing attacks, attackers send fraudulent SMS messages designed to trick the recipient into clicking a malicious link or providing personal information. These messages often look like they come from reputable sources, such as delivery services, banks, or even friends.
For instance, a smishing text might claim that the victim's bank account has been suspended and ask them to click a link to restore access. Once the link is clicked, the victim is directed to a fake website where their login credentials are stolen.
6. Tailgating and Piggybacking
While many social engineering attacks focus on digital methods, some target physical security weaknesses. Tailgating and piggybacking are two forms of physical social engineering used to gain unauthorized access to secure buildings or restricted areas.
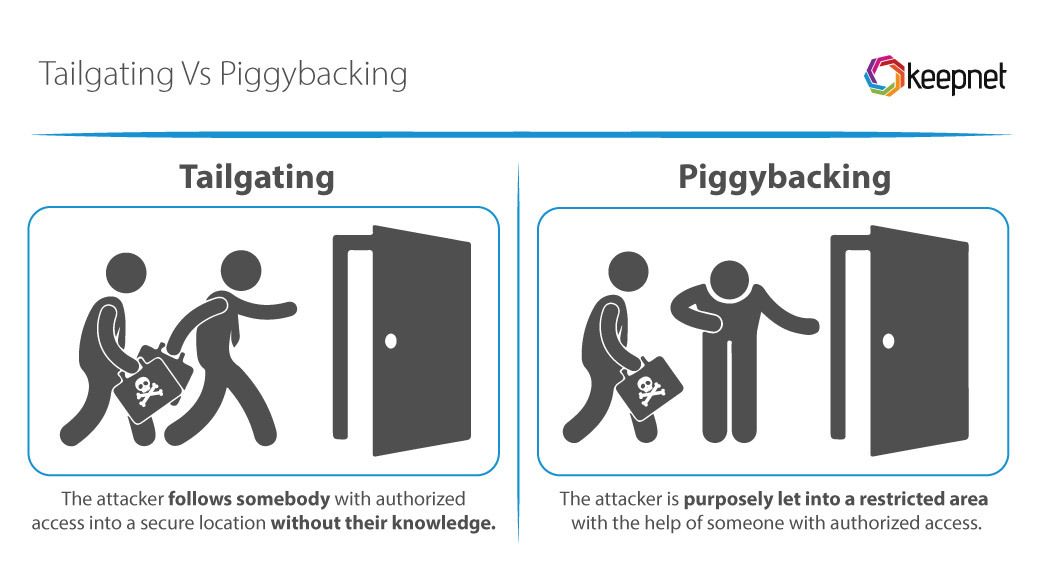
Tailgating: In tailgating, an unauthorized person follows an authorized individual into a secure area, often without the authorized person's knowledge. This might occur when an attacker slips in through a door before it closes after someone else enters a building.
For example, an attacker might wait outside a corporate building until an employee enters. They then follow the employee closely, passing through the door without using a keycard.
Piggybacking: Similar to tailgating, piggybacking involves gaining access to a secure area, but in this case, the authorized person is aware of the attacker's presence and allows them entry—often out of politeness or trust.
A common scenario might involve an attacker carrying heavy boxes or appearing to be in distress. Out of kindness, an employee might hold the door open for them, unknowingly granting access to a restricted area.
Defending Against Social Engineering
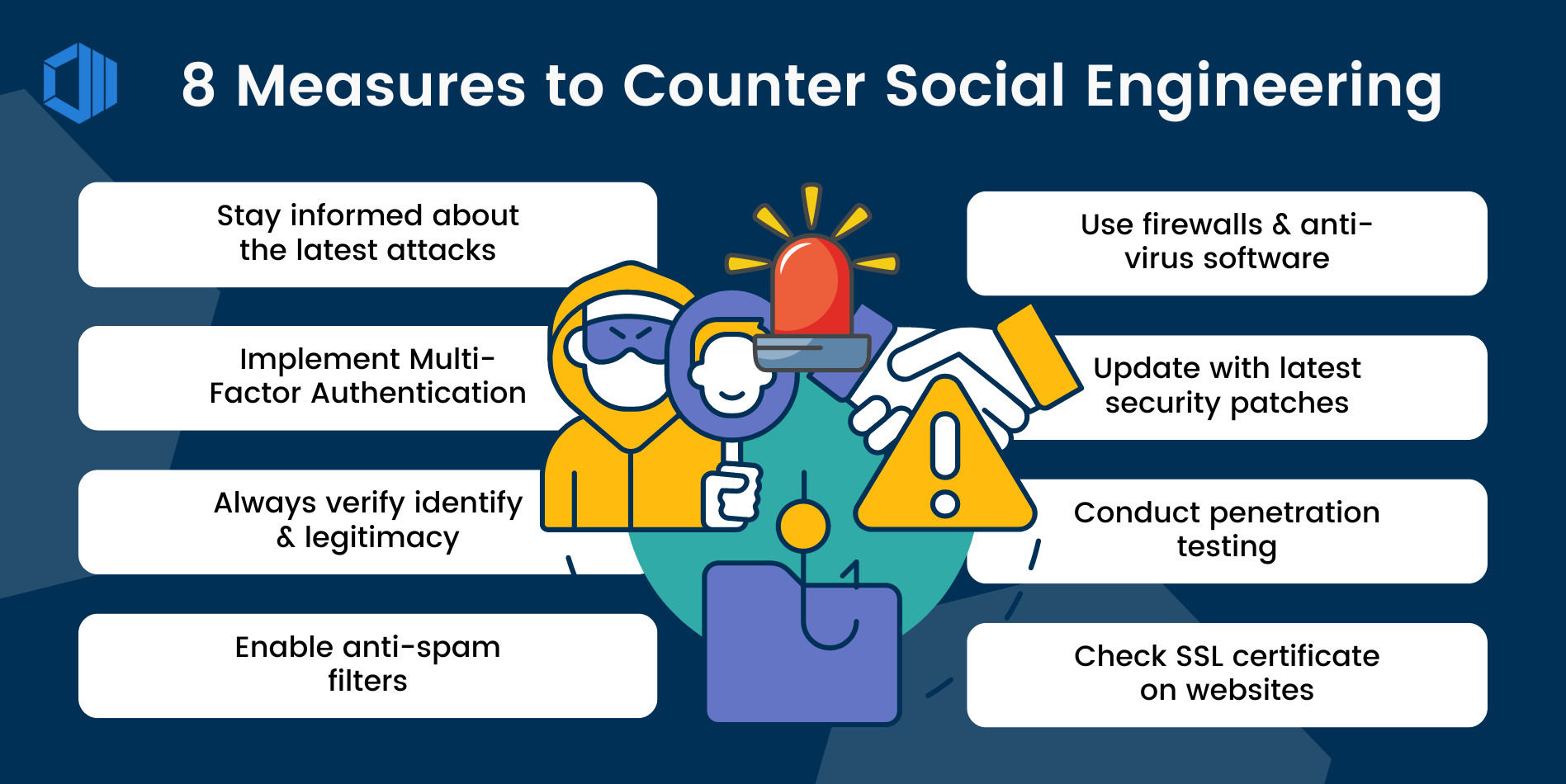
Defending against social engineering attacks requires a multi-layered approach that addresses both technological and human factors. Some key strategies include:
Employee Training and Awareness: One of the most effective defenses is employee training. Regularly educate employees on the dangers of social engineering, how to spot phishing attempts, and what to do if they suspect an attack. Awareness of these tactics can reduce the likelihood of falling for them.
Strong Verification Procedures: Implement strict verification processes for sensitive transactions or requests for personal information. For instance, if an employee receives a suspicious email asking for login credentials, they should verify the request with the supposed sender through a different communication channel.
Multi-Factor Authentication (MFA): MFA adds an additional layer of security beyond just passwords, making it harder for attackers to gain unauthorized access even if they obtain login credentials.
Regular Security Audits: Regularly audit your organization's security practices to identify weaknesses that could be exploited by social engineers. This includes both digital and physical security measures.
Physical Security Measures: In addition to digital protections, ensure that physical security is a priority. Install keycard systems, security cameras, and procedures for verifying visitors to prevent tailgating or piggybacking.
Conclusion
Social engineering attacks are among the most dangerous and effective techniques used by cybercriminals today. These attacks exploit human nature—trust, fear, curiosity, and the desire for convenience—making them difficult to defend against. However, by understanding the various types of social engineering (such as phishing, baiting, pretexting, vishing, and physical attacks like tailgating), and implementing robust security measures, individuals and organizations can significantly reduce their risk.
The key to combatting social engineering lies in awareness. Educating employees and individuals about the tactics used by attackers, fostering a security-conscious culture, and maintaining strong verification procedures are essential in staying one step ahead of cybercriminals. In the end, technology alone cannot protect against social engineering—humans must be the first line of defense.
