Understanding Advanced Persistent Threats (APTs): Techniques and Countermeasures

Advanced Persistent Threats (APTs) represent one of the most sophisticated and dangerous challenges in modern cybersecurity. These highly organized, stealthy attacks are often carried out by well-funded adversaries, such as nation-states or criminal organizations, targeting critical sectors like government agencies, financial institutions, and large enterprises. What sets APTs apart is their persistence: attackers infiltrate systems and remain undetected for months, or even years, exfiltrating sensitive data or waiting to strike.
In this article, we'll delve deep into the world of APTs, uncovering what makes them unique and why they're so difficult to defend against. We'll break down their lifecycle, analyze real-world examples, and explore effective countermeasures that organizations can adopt to mitigate their risks. Additionally, we'll examine how ethical hackers play a crucial role in identifying and neutralizing APT threats. Finally, we'll look ahead to understand how emerging technologies might influence the evolution of APTs in the future.
Let's begin by understanding the defining characteristics of APTs and what makes them a serious cybersecurity threat.
1. Characteristics of APTs
Advanced Persistent Threats (APTs) are not your typical cyberattacks. They are meticulously planned, highly targeted operations designed to infiltrate systems, remain undetected, and cause maximum damage. Below are the defining characteristics that set APTs apart:
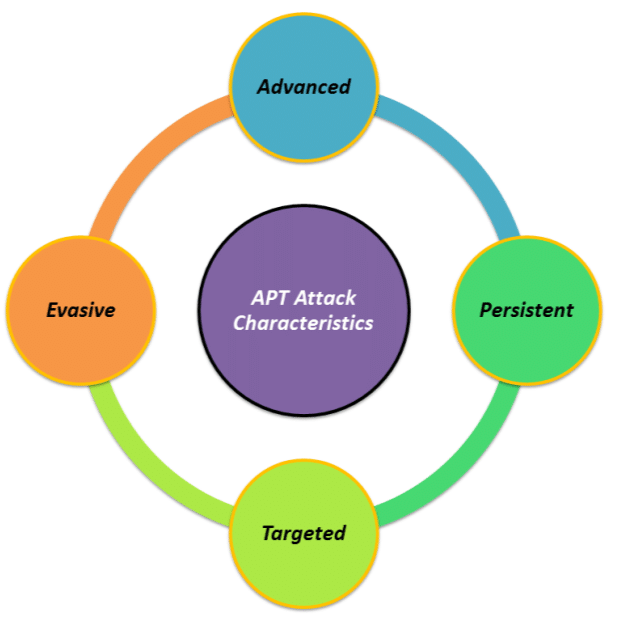
1.1. Persistence
The hallmark of an APT is its ability to persist within a network for extended periods, often months or even years. Unlike opportunistic cyberattacks, APTs are patient, taking their time to collect data, monitor activities, or wait for the perfect moment to act.
1.2. Sophistication
APTs employ cutting-edge techniques and tools, such as:
- Zero-day vulnerabilities, which exploit unknown software flaws.
- Custom malware, crafted specifically for the target.
- AI-driven tactics, enabling adaptive and unpredictable behaviors.
This level of sophistication often points to well-funded groups, such as nation-states or organized cybercriminal networks.
1.3. Targeted Nature
Unlike broad-spectrum attacks, APTs are laser-focused on high-value targets. These include:
- Government agencies, to steal classified intelligence.
- Corporations, to gain a competitive edge or steal intellectual property.
- Critical infrastructure, like energy grids or healthcare systems, for maximum disruption.
The attackers select their victims based on strategic objectives, ensuring that their efforts yield high rewards.
1.4. Multi-Vector Strategy
APTs use a blend of attack vectors to infiltrate systems and maintain access. Common methods include:
- Phishing emails to exploit human vulnerabilities.
- Supply chain attacks to infiltrate through trusted third parties.
- Exploitation of known vulnerabilities in outdated systems.
This multi-pronged approach ensures their success, even if one vector fails.
1.5. Stealth and Evasion
APTs excel at hiding in plain sight. They often:
- Use encryption to mask communication.
- Deploy fileless malware that resides in system memory.
- Abuse legitimate tools like PowerShell to blend with normal network activity.
This stealthy behavior makes detection extraordinarily difficult, allowing attackers to operate undisturbed.
With a clear understanding of what makes APTs unique, let's examine how these attacks unfold through their distinct lifecycle.
2. The Lifecycle of an APT Attack
Advanced Persistent Threats (APTs) follow a structured lifecycle designed to maximize their impact while remaining undetected. This lifecycle consists of distinct stages, each with specific objectives and techniques. Here's how APTs operate from start to finish:
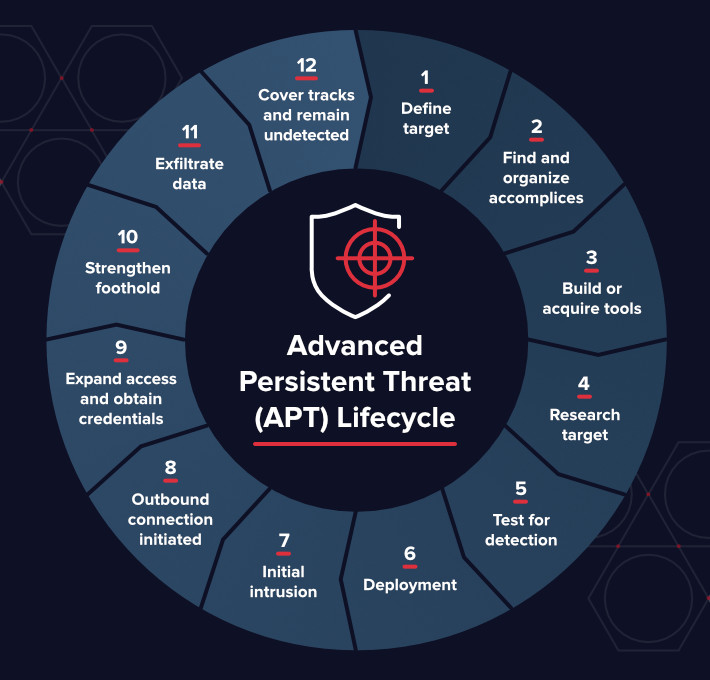
2.1. Initial Reconnaissance
Before launching an attack, APT actors conduct extensive research on their target.
- Objective: Gather detailed information to identify vulnerabilities.
- Techniques Used:
- Open-Source Intelligence (OSINT) to analyze publicly available data, such as employee LinkedIn profiles, emails, or company infrastructure.
- Scanning tools to identify network weaknesses or exposed assets.
This phase ensures that the attackers have a solid understanding of the target environment.
2.2. Initial Compromise
The attackers gain their first foothold in the system.
- Objective: Penetrate the target network.
- Techniques Used:
- Spear-phishing emails with malicious attachments or links.
- Exploiting zero-day vulnerabilities in software or hardware.
- Using compromised third parties in supply chain attacks.
Once inside, the attackers typically install backdoors for continued access.
2.3. Establishing a Foothold
After the initial breach, APT actors strengthen their position within the system.
- Objective: Maintain persistent access while avoiding detection.
- Techniques Used:
- Deploying custom malware designed to evade antivirus tools.
- Creating backdoors or modifying legitimate system processes.
- Using tools like Mimikatz to steal credentials and gain lateral movement.
Attackers often prioritize securing administrative privileges during this stage.
2.4. Privilege Escalation and Lateral Movement
The attackers expand their control over the network.
- Objective: Gain higher-level permissions and access sensitive areas.
- Techniques Used:
- Exploiting privilege escalation vulnerabilities.
- Moving laterally through the network by exploiting trust relationships between devices.
- Using compromised credentials to access critical systems or databases.
This stage allows attackers to move closer to their ultimate goal.
2.5. Data Exfiltration or Impact
The final objective of the APT becomes clear.
- Objective: Steal valuable data or cause disruption.
- Techniques Used:
- Data Exfiltration: Encrypting sensitive information and transferring it to external servers.
- System Impact: Planting ransomware, altering critical systems, or sabotaging operations.
Some APTs remain dormant for extended periods before acting, especially if their goal is strategic espionage.
2.6. Covering Tracks
To maintain their stealth and prevent future detection, attackers clean up their activities.
- Objective: Remove evidence of the attack.
- Techniques Used:
- Deleting logs or altering timestamps to obscure activities.
- Deactivating backdoors if the operation is complete.
- Using self-destruct mechanisms in malware to eliminate traces.
This step ensures that even if the attack is discovered later, its origins remain difficult to trace.
Understanding this lifecycle is critical for cybersecurity professionals to recognize and disrupt APTs at any stage. In the next section, we'll analyze real-world examples of APT groups and their tactics.
3. Notable Examples of APT Groups
Advanced Persistent Threats are often carried out by highly skilled groups with distinct motives and methods. Many of these groups are linked to nation-states or organized crime, and their activities have had global repercussions. Below are some of the most infamous APT groups and their tactics:
3.1. APT29 (Cozy Bear)
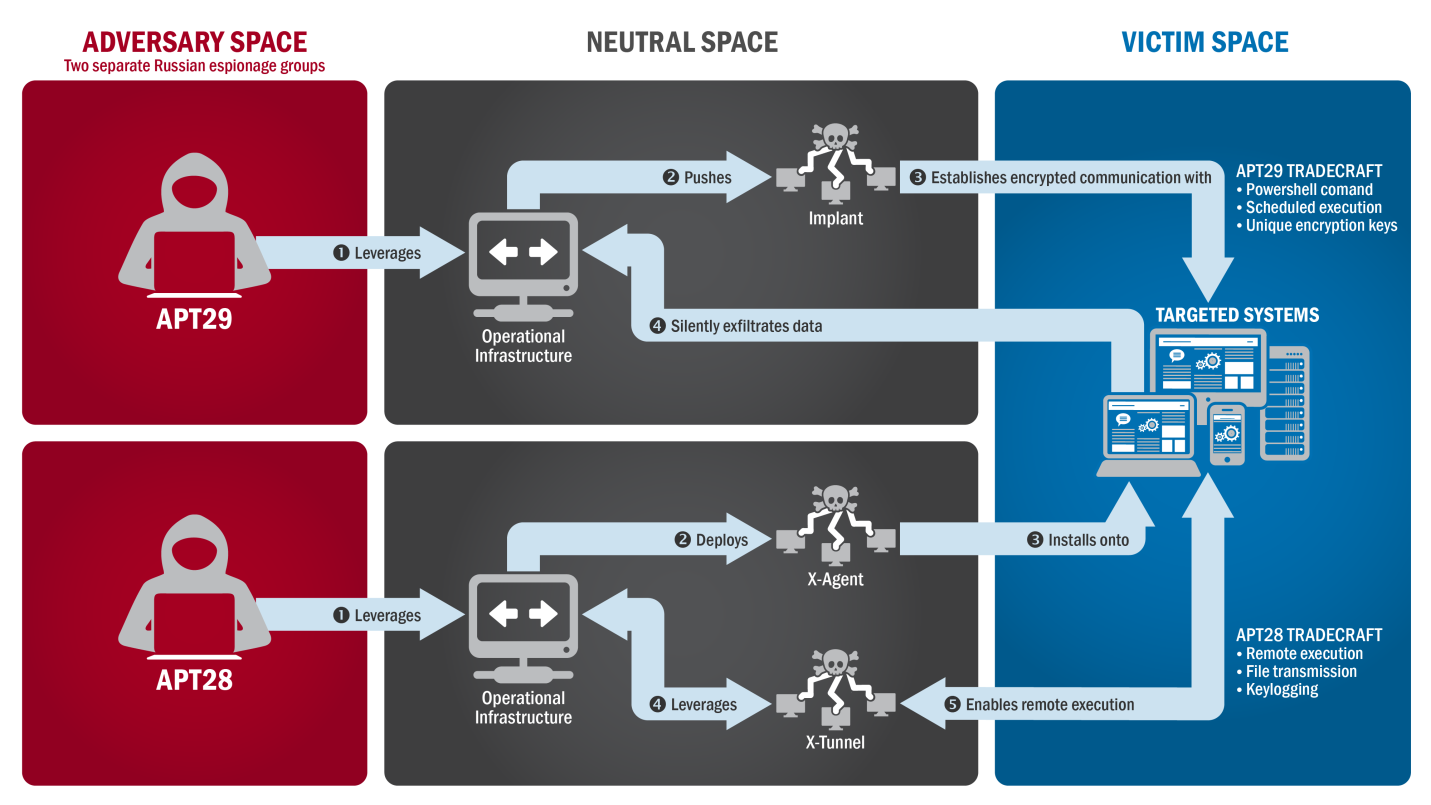
- Affiliation: Believed to be linked to Russian intelligence.
- Notable Activities:
- Responsible for the 2020 SolarWinds attack, which compromised U.S. government agencies and corporations.
- Known for targeting diplomatic, healthcare, and energy sectors.
- Tactics Used:
- Supply chain attacks to infiltrate trusted software systems.
- Spear-phishing emails and credential harvesting.
APT29 is renowned for its stealth and ability to remain undetected for prolonged periods.
3.2. Lazarus Group
- Affiliation: Tied to North Korea.
- Notable Activities:
- The 2014 Sony Pictures hack, which exposed sensitive corporate data.
- Large-scale cryptocurrency thefts, including the Axie Infinity Ronin bridge attack in 2022.
- Tactics Used:
- Financially motivated cyberattacks to fund national programs.
- Malware-laden phishing campaigns targeting banks and fintech companies.
Lazarus Group demonstrates how APTs can blend geopolitical and financial motives.
3.3. APT10 (Stone Panda)
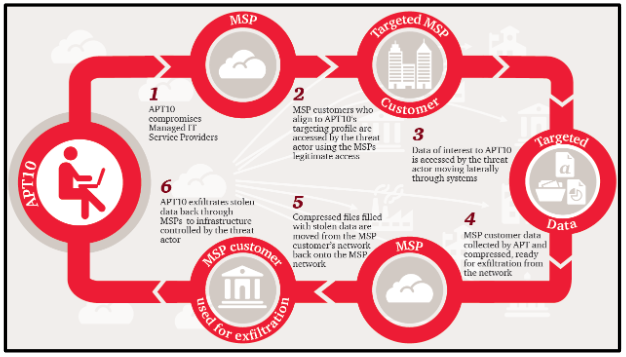
- Affiliation: Associated with Chinese intelligence.
- Notable Activities:
- The "Cloud Hopper" campaign, targeting managed IT service providers (MSPs) worldwide.
- Focus on intellectual property theft from aerospace, technology, and pharmaceutical industries.
- Tactics Used:
- Exploiting vulnerabilities in cloud platforms and remote desktop protocols.
- Using advanced credential theft to access sensitive corporate data.
APT10 underscores the economic espionage potential of APTs.

3.4. Sandworm Team
- Affiliation: Attributed to Russian military intelligence (GRU).
- Notable Activities:
- The 2015 and 2016 attacks on Ukraine's power grid, leading to widespread blackouts.
- Deployment of the NotPetya malware, which caused billions in damages globally.
- Tactics Used:
- Targeting critical infrastructure to cause disruption.
- Leveraging destructive malware to sabotage systems.
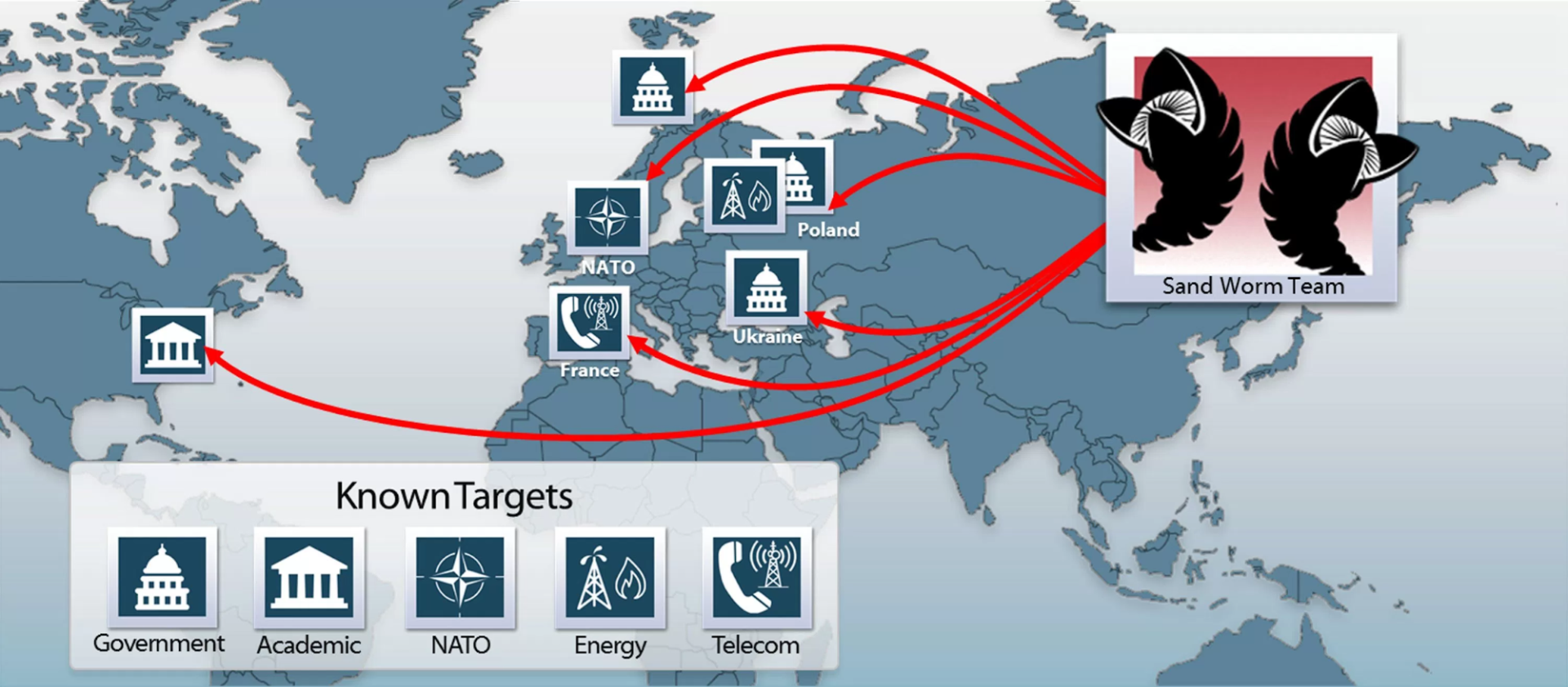
Sandworm's attacks highlight the destructive potential of APTs when targeting national infrastructure.
3.5. Equation Group
- Affiliation: Believed to be connected to the U.S. National Security Agency (NSA).
- Notable Activities:
- Development of sophisticated malware like Stuxnet, which disrupted Iran's nuclear program in 2010.
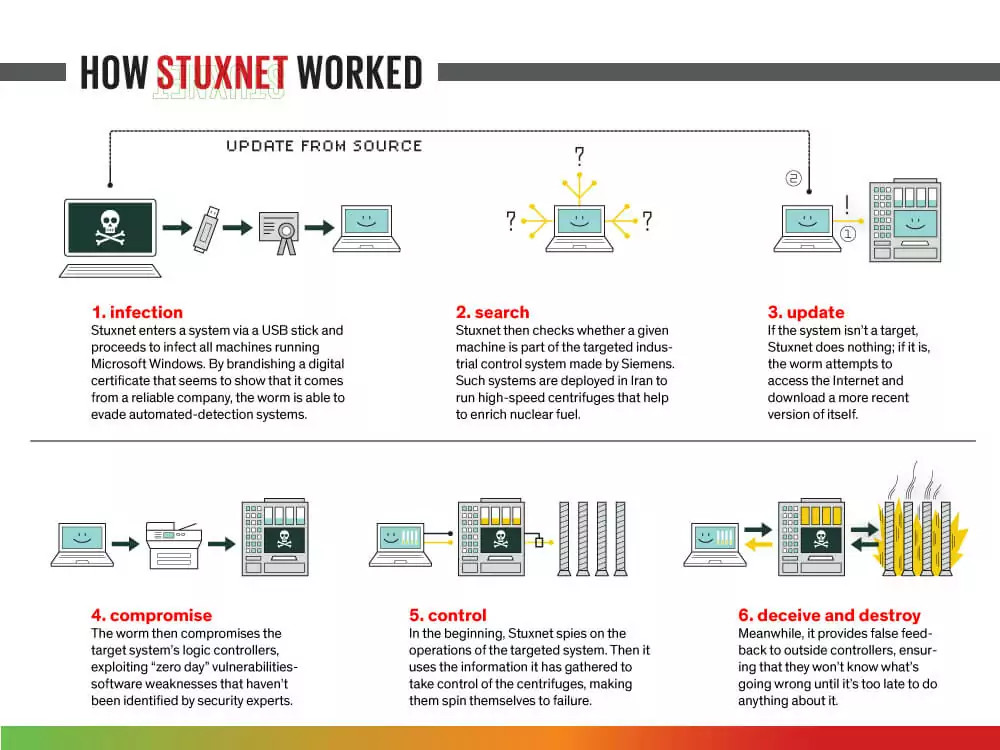
- Tactics Used:
- Exploiting zero-day vulnerabilities with unparalleled precision.
- Using hardware implants and encryption for stealth.
Equation Group exemplifies the complexity of state-sponsored APTs.
Each of these groups has left a lasting impact on the cybersecurity landscape. Their tactics provide valuable insights into the evolving nature of APTs. In the next section, we'll discuss effective countermeasures to defend against these advanced threats.
4. Countermeasures Against APTs
Defending against Advanced Persistent Threats (APTs) requires a multi-layered approach. Organizations must be proactive, combining cutting-edge technology, robust policies, and human expertise. Here are the most effective strategies to counter APTs:
4.1. Proactive Monitoring and Detection
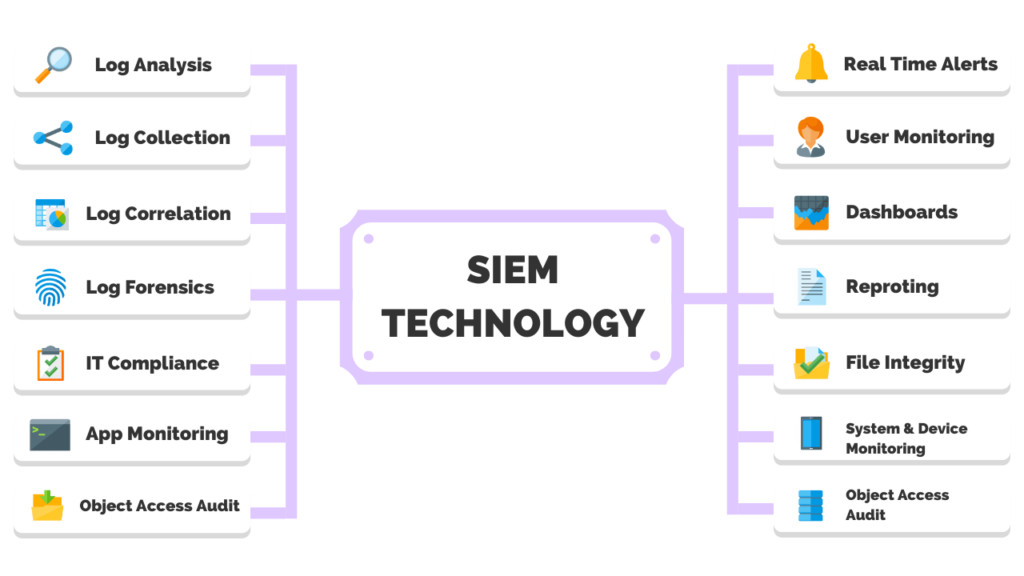
- Implement Security Information and Event Management (SIEM) tools to analyze logs and identify anomalies in real-time.
- Use Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to detect malicious activity.
- Incorporate behavioral analytics to flag deviations from normal user patterns.
4.2. Zero Trust Architecture
- Adopt a Zero Trust model where no user or device is trusted by default.
- Use strict identity verification protocols like multi-factor authentication (MFA).
- Limit user access to resources based on the principle of least privilege.
4.3. Regular Patching and Vulnerability Management

- Keep all software and hardware up to date to mitigate known vulnerabilities.
- Conduct regular vulnerability scans and penetration tests to identify weaknesses.
- Use patch management tools to automate updates and minimize human oversight.
4.4. Threat Intelligence Integration
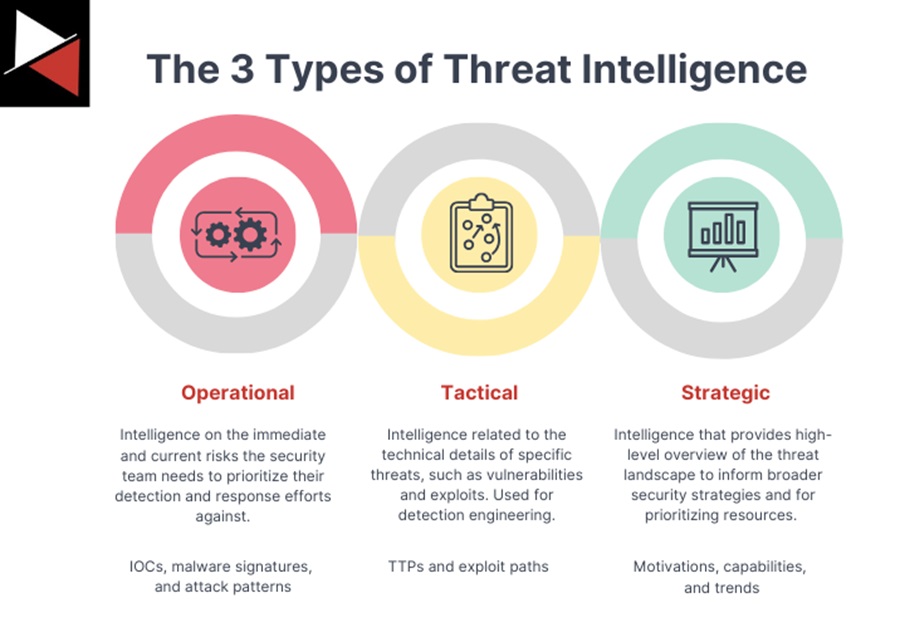
- Leverage threat intelligence feeds to stay informed about emerging APT tactics and indicators of compromise (IOCs).
- Collaborate with external entities like ISACs (Information Sharing and Analysis Centers) to share and receive insights.
- Use Machine Learning (ML) algorithms to analyze threat data and predict potential attacks.
4.5. Employee Training
- Conduct regular phishing simulation exercises to educate employees about email-based threats.
- Train staff to recognize signs of social engineering attempts.
- Establish clear procedures for reporting suspicious activities.
4.6. Incident Response Planning
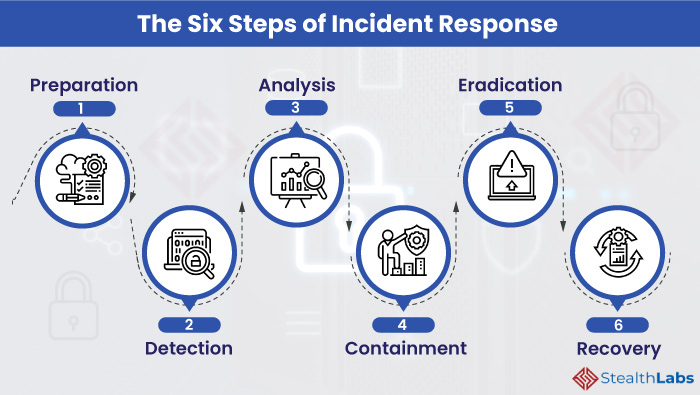
- Develop a robust Incident Response Plan (IRP) to ensure quick containment and recovery.
- Conduct regular tabletop exercises to simulate APT scenarios.
- Ensure backups are secure, encrypted, and regularly tested for restoration.
5. The Role of Ethical Hackers in Mitigating APTs
Ethical hackers are invaluable in the fight against APTs. By thinking like attackers, they can uncover vulnerabilities and simulate real-world threats to bolster defenses.
- Penetration Testing: Ethical hackers mimic APT tactics to test the resilience of networks. This includes exploiting vulnerabilities and testing privilege escalation paths.
- Red Teaming: Simulating adversarial attacks in coordination with Blue Teams (defenders) to refine response protocols.
- Threat Hunting: Identifying signs of APT presence through proactive analysis, even when attackers are in stealth mode.
- Improving Security Posture: Ethical hackers contribute to implementing best practices and reducing the attack surface.
By leveraging the skills of ethical hackers, organizations can identify weaknesses before malicious actors exploit them.
6. Future Trends in APTs
As technology evolves, APT tactics are expected to grow more sophisticated. Here are emerging trends that could redefine how APTs operate:
6.1. AI and Machine Learning

- Attackers are increasingly using AI to automate reconnaissance, evade detection, and adapt to defenses.
- Machine learning algorithms are also being employed to bypass traditional security measures.
6.2. Quantum Computing
- Quantum computers could potentially break modern encryption, posing a significant risk to current cryptographic standards.
- Organizations must begin transitioning to quantum-resistant encryption to stay ahead of the curve.
6.3. IoT Exploitation

- The proliferation of Internet of Things (IoT) devices increases the attack surface.
- Weakly secured IoT networks could serve as entry points for APTs to access critical systems.
6.4. Supply Chain Vulnerabilities
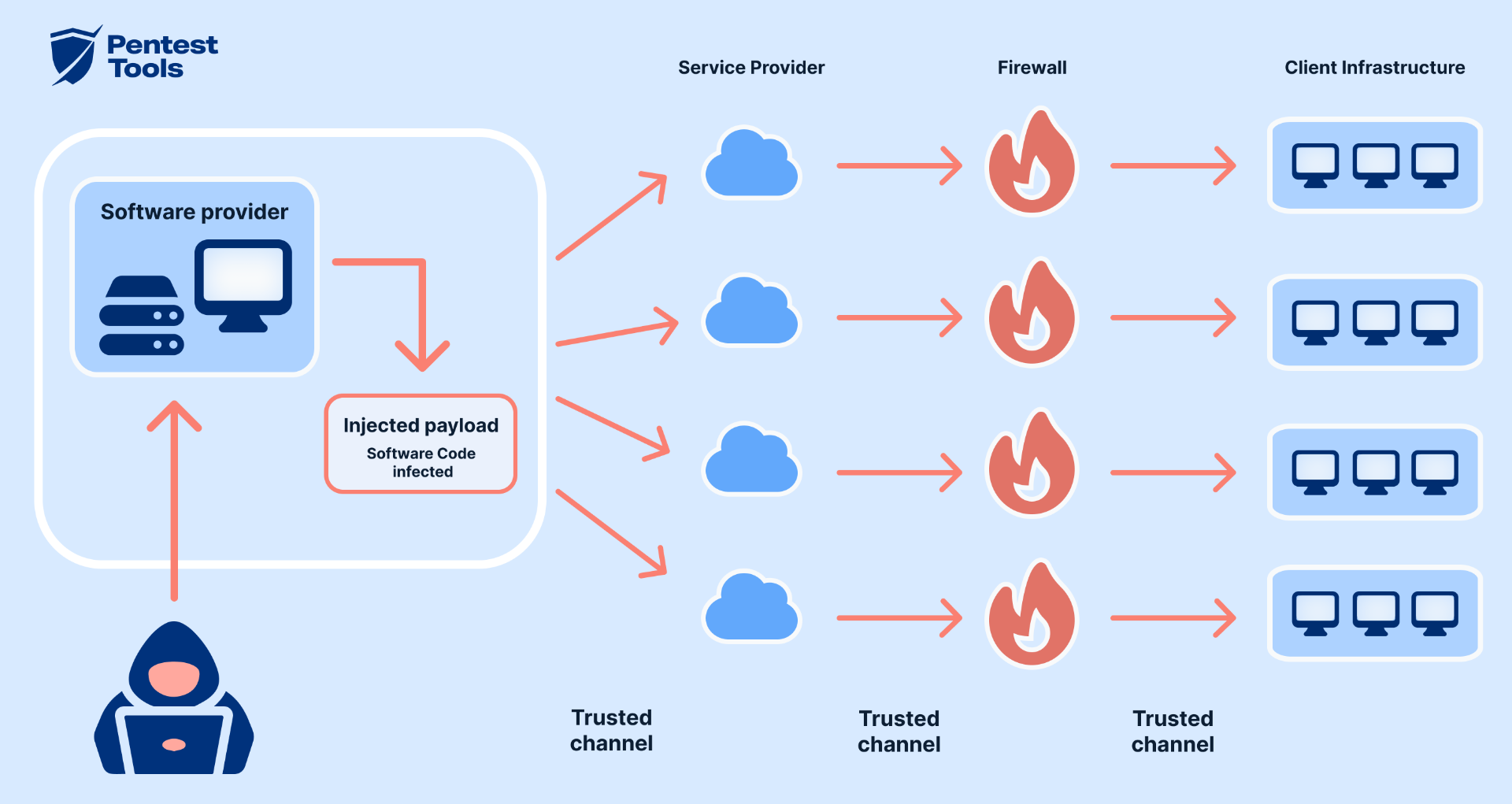
- APTs will continue to exploit third-party vendors and software providers to infiltrate high-value targets.
- Strengthening supply chain security will be crucial in mitigating this risk.
7. Conclusion
Advanced Persistent Threats (APTs) pose a relentless and evolving challenge to cybersecurity. Their unique characteristics—persistence, sophistication, and stealth—make them formidable adversaries, capable of causing widespread damage and disruption.
To counter these threats, organizations must adopt a proactive and multi-faceted defense strategy, combining technology, policy, and human expertise. Ethical hackers play a pivotal role in this effort, helping to uncover vulnerabilities and strengthen defenses before attackers strike.
As we move into a future shaped by AI, quantum computing, and an ever-expanding digital landscape, staying vigilant and adaptive will be essential. By understanding APTs and their tactics, we can take the necessary steps to protect critical systems and safeguard sensitive information.
