Securing Mobile Applications: Best Practices and Essential Tools for Ethical Hackers

Introduction
In today's digital age, mobile applications have become an integral part of our daily lives, offering convenience and connectivity at our fingertips. From banking and shopping to social networking and entertainment, mobile apps are ubiquitous. However, this proliferation of mobile applications also brings significant security challenges. Mobile apps often handle sensitive personal and financial information, making them prime targets for cybercriminals.
The importance of mobile application security cannot be overstated. A single vulnerability in a mobile app can lead to severe consequences, including data breaches, financial losses, and damage to an organization's reputation. Therefore, ensuring the security of mobile applications is paramount.
This is where ethical hackers play a crucial role. Ethical hackers, also known as white-hat hackers, use their skills to identify and fix security vulnerabilities before malicious hackers can exploit them. By employing ethical hacking techniques, security professionals can proactively protect mobile applications from potential threats.
In this article, we will explore common mobile security vulnerabilities, best practices for securing mobile applications, essential tools for ethical hackers, and a real-world case study to illustrate the application of mobile security testing. Our goal is to provide a comprehensive guide for ethical hackers and developers to enhance the security of mobile applications.
Common Mobile Security Vulnerabilities
Mobile applications are prone to various security vulnerabilities that can be exploited by malicious actors. Understanding these vulnerabilities is the first step in securing mobile applications. Here are some of the most common security issues:
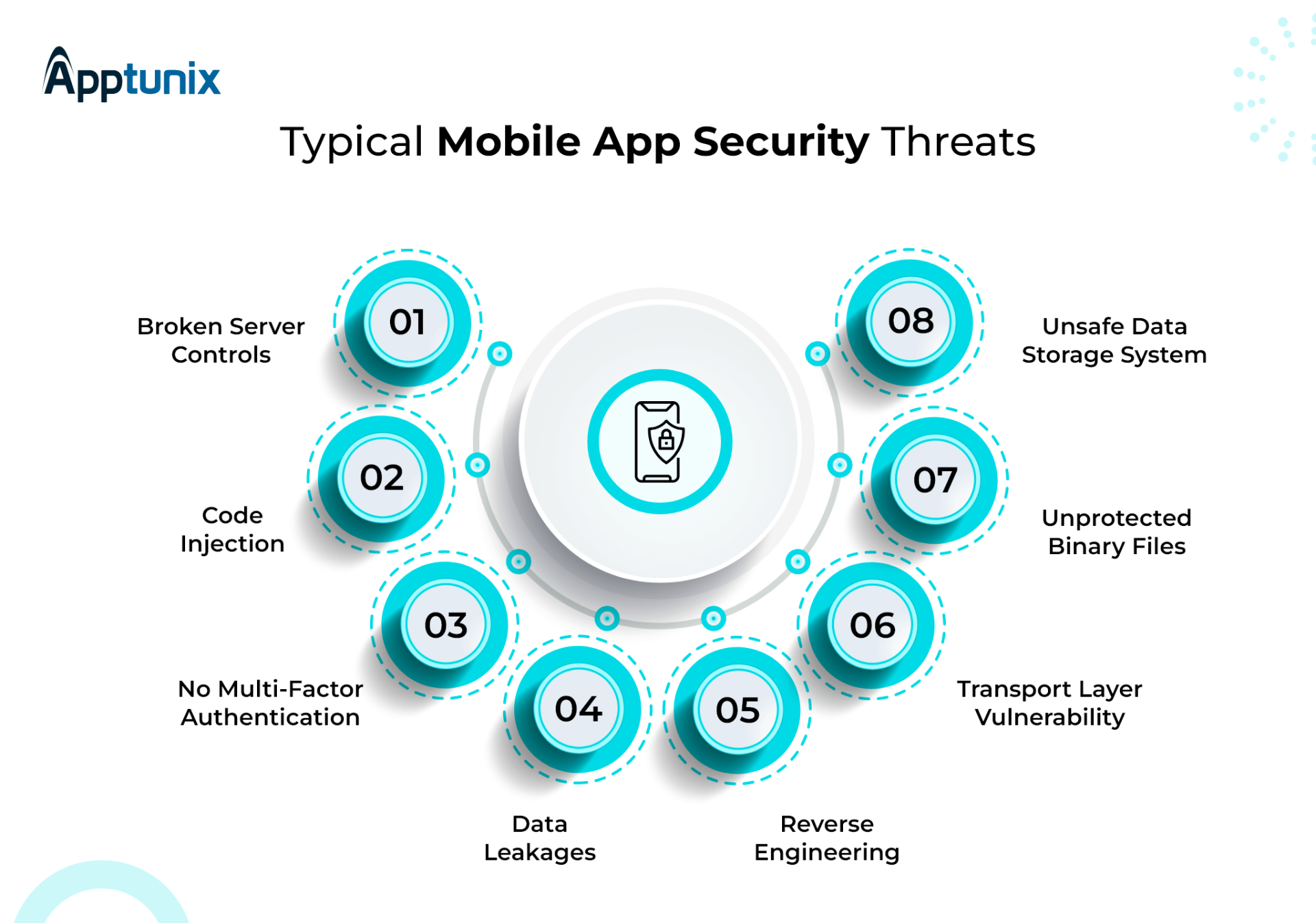
Insecure Data Storage
- Many mobile applications store sensitive data on the device itself. If this data is not encrypted or securely stored, it can be easily accessed by attackers through techniques like rooting or jailbreaking the device. Common data storage issues include storing passwords in plain text, unprotected databases, and insecure use of external storage.
Insufficient Cryptography
- Cryptographic algorithms are essential for protecting data. However, improper implementation or weak cryptography can lead to significant security breaches. This includes using outdated encryption standards, poor key management practices, and failing to encrypt sensitive data during transmission and storage.
Insecure Communication
- Mobile applications often communicate with servers over the internet. If this communication is not secured, it can be intercepted by attackers through techniques like Man-in-the-Middle (MitM) attacks. Vulnerabilities in this category include lack of SSL/TLS encryption, improper certificate validation, and using insecure communication protocols.
Poor Authorization and Authentication
- Weak authentication mechanisms make it easier for attackers to gain unauthorized access to mobile applications. Common issues include relying on device identifiers, not enforcing strong password policies, and not implementing multi-factor authentication. Additionally, improper session management can allow attackers to hijack user sessions.
Client-Side Injection
- Mobile applications that do not properly validate input can be vulnerable to client-side injection attacks, such as SQL injection and code injection. These attacks can allow attackers to execute arbitrary code or manipulate the app's behavior. Input validation and sanitization are critical to prevent these types of vulnerabilities.
By understanding and addressing these common mobile security vulnerabilities, developers and ethical hackers can significantly enhance the security posture of mobile applications. In the next section, we will discuss best practices for securing mobile applications to mitigate these risks.
Best Practices for Securing Mobile Applications
To mitigate the risks associated with common mobile security vulnerabilities, developers and ethical hackers should adhere to a set of best practices. These practices help ensure that mobile applications are robust and resilient against various security threats.
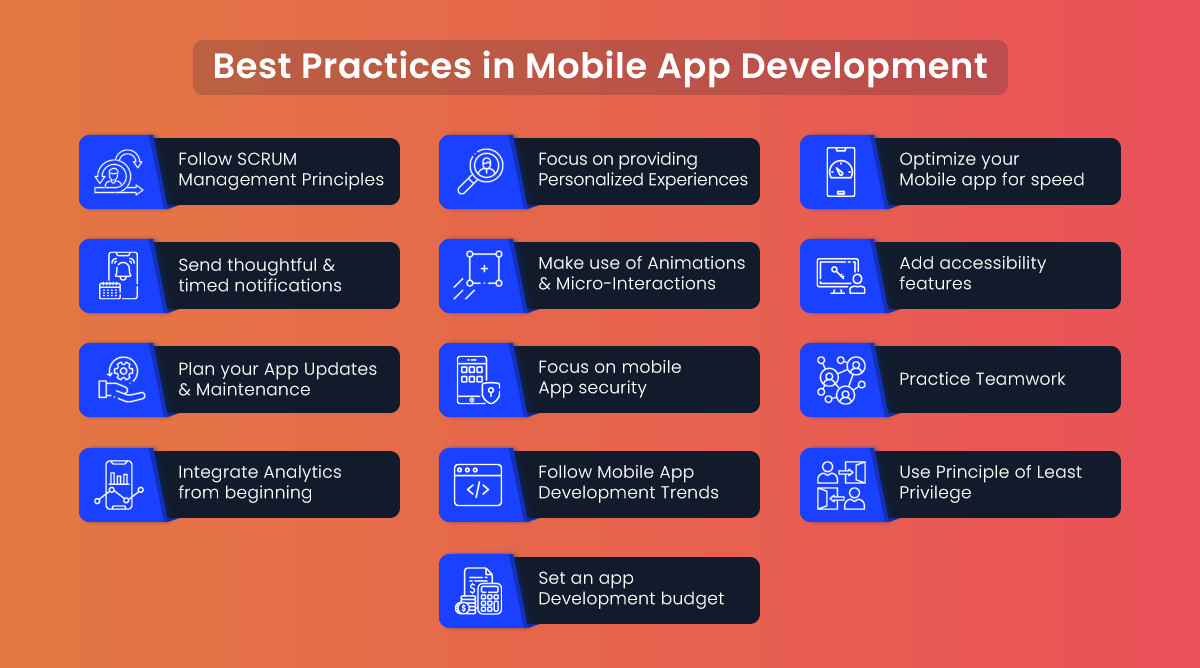
Secure Coding Practices
- Implementing secure coding practices is fundamental to building secure mobile applications. This includes validating and sanitizing all user inputs, using parameterized queries to prevent SQL injection, avoiding hardcoding sensitive information like API keys and passwords, and following the principle of least privilege for all code and data access.
Implementing Strong Authentication and Authorization
- Enforcing strong authentication mechanisms, such as multi-factor authentication (MFA), can significantly enhance security. Use strong, unique passwords and ensure secure session management. Implement robust authorization checks to ensure that users can only access resources and perform actions for which they are explicitly authorized.
Encrypting Sensitive Data
- Data encryption is crucial for protecting sensitive information both at rest and in transit. Use strong encryption algorithms (such as AES-256) to encrypt data stored on the device and data transmitted between the mobile app and servers. Ensure proper key management practices are in place to safeguard encryption keys.
Ensuring Secure Communication Channels
- Secure communication channels are vital for protecting data transmitted over the internet. Use HTTPS to encrypt data in transit and enforce the use of SSL/TLS. Implement proper certificate validation to prevent MitM attacks and ensure that certificates are up-to-date and correctly configured.
Regular Security Audits and Penetration Testing
- Conduct regular security audits and penetration tests to identify and fix vulnerabilities. Use automated tools and manual testing techniques to thoroughly assess the security of the mobile application. Keep up-to-date with the latest security threats and ensure that your security practices evolve accordingly.
By adhering to these best practices, developers can build more secure mobile applications and ethical hackers can effectively identify and address potential vulnerabilities. In the next section, we will explore essential tools that ethical hackers can use to test and secure mobile applications.
Essential Tools for Ethical Hackers
To effectively secure mobile applications, ethical hackers rely on a variety of tools designed to identify and exploit vulnerabilities. Here are some essential tools that can aid in mobile security testing:

OWASP Mobile Security Testing Guide (MSTG)
- The OWASP Mobile Security Testing Guide is a comprehensive resource that provides guidelines, test cases, and best practices for mobile security testing. It covers a wide range of topics, including mobile app architecture, security testing methodologies, and common vulnerabilities. The MSTG is a valuable reference for both beginners and experienced security testers.
MobSF (Mobile Security Framework)
- MobSF is an automated, all-in-one mobile application security testing framework. It supports both Android and iOS platforms and provides features for static analysis, dynamic analysis, and malware analysis. MobSF can identify a variety of vulnerabilities, including insecure data storage, insecure communication, and code injection flaws.
Drozer
- Drozer is a comprehensive security testing framework for Android applications. It allows testers to interact with the application and its components, identify security vulnerabilities, and exploit them. Drozer can be used to test for issues such as insecure IPC mechanisms, misconfigured components, and weaknesses in the app's architecture.
Frida
- Frida is a dynamic instrumentation toolkit that allows ethical hackers to inject custom scripts into running applications. This tool is useful for reverse engineering, debugging, and exploring the internals of mobile apps. Frida supports both Android and iOS platforms and can be used to bypass security controls, monitor API calls, and manipulate app behavior in real-time.
Burp Suite Mobile Assistant
- Burp Suite is a popular web vulnerability scanner, and its Mobile Assistant extension enhances its capabilities for mobile app testing. The Mobile Assistant helps in capturing and analyzing HTTP/HTTPS traffic from mobile devices. This tool is essential for identifying insecure communication issues, performing MitM attacks, and testing backend APIs used by mobile applications.
These tools, when used effectively, can help ethical hackers uncover and address security weaknesses in mobile applications. In the following section, we will look at a real-world case study to illustrate the practical application of mobile security testing techniques.
Case Study: Real-World Application of Mobile Security Testing
To illustrate the practical application of mobile security testing techniques, let's examine a real-world case study where ethical hackers conducted a comprehensive security audit on a mobile banking application.
Overview of the Mobile Security Audit
A leading financial institution developed a mobile banking application that allows customers to perform various transactions, such as checking account balances, transferring funds, and paying bills. Given the sensitive nature of financial data, the institution engaged a team of ethical hackers to conduct a thorough security audit of the application.
Steps Taken to Identify and Mitigate Vulnerabilities
Reconnaissance and Information Gathering
- The ethical hackers began by gathering information about the application, its architecture, and the underlying infrastructure. This included understanding the app's functionalities, backend APIs, and third-party services integrated into the app.
Static Analysis
- Using MobSF, the team performed static analysis on the application's APK file (for Android) and IPA file (for iOS). This process involved decompiling the app to review the source code and identify potential security issues such as hardcoded credentials, insecure data storage, and improper use of cryptographic functions.
Dynamic Analysis
- The ethical hackers utilized Frida and Burp Suite Mobile Assistant to perform dynamic analysis. They instrumented the running application to monitor its behavior, capture network traffic, and identify vulnerabilities in real-time. During this phase, the team discovered several insecure communication channels and weak authentication mechanisms.
Manual Penetration Testing
- In addition to automated tools, the team conducted manual penetration testing to explore complex vulnerabilities that might not be detected by automated scans. They tested for issues like SQL injection, broken authentication, and authorization flaws by manually interacting with the application's components and backend APIs.
Reporting and Remediation
- After identifying and confirming the vulnerabilities, the ethical hackers compiled a detailed report outlining each issue, its potential impact, and recommendations for remediation. The report was shared with the development team, who then worked to fix the identified vulnerabilities following the provided recommendations.
Lessons Learned and Best Practices Reinforced
Importance of Regular Security Testing
- The case study underscored the need for regular security testing throughout the application's development lifecycle. Continuous testing helps in early detection and remediation of vulnerabilities, reducing the risk of exploitation.
Implementing Strong Authentication and Encryption
- Weak authentication mechanisms and inadequate encryption were identified as significant vulnerabilities. Strengthening these aspects is crucial for protecting sensitive user data and preventing unauthorized access.
Comprehensive Security Measures
- A combination of automated tools and manual testing is essential for a thorough security assessment. While automated tools can quickly identify common vulnerabilities, manual testing is necessary to uncover more complex issues.
Collaboration between Security and Development Teams
- Effective collaboration between ethical hackers and development teams is vital for successful vulnerability remediation. Clear communication and understanding of security issues enable development teams to implement appropriate fixes.
By following these steps and lessons learned, the financial institution significantly improved the security posture of its mobile banking application, ensuring better protection for its users' sensitive financial data.
Conclusion
Mobile application security is a critical aspect of modern software development, particularly for applications handling sensitive information. By understanding common vulnerabilities, adhering to best practices, utilizing essential tools, and learning from real-world case studies, ethical hackers and developers can work together to create secure and resilient mobile applications.
As the threat landscape continues to evolve, staying informed about the latest security trends and continuously improving security practices will remain essential. Ethical hackers play a pivotal role in this ongoing effort, ensuring that mobile applications are robust against emerging threats and providing users with safe and secure digital experiences.
