Rootkits & Bootkits Explained: The Hidden Dangers Inside Your System

🛡️ Rootkits and bootkits are some of the stealthiest and most persistent forms of malware ever developed. They don't just infect systems—they embed themselves so deeply that traditional security tools often can't even see them.
In this article, we're going to break down the fundamentals of these hidden threats. You'll learn:
-
What exactly rootkits and bootkits are
-
How they work and where they hide
-
The key differences between them
-
Why they're so hard to detect and remove
-
What tools and strategies ethical hackers can use to uncover them
Whether you're just getting started in ethical hacking or want to deepen your understanding of advanced malware, this guide will give you a solid foundation to identify, analyze, and protect against these stealthy threats.
🔍 Introduction: Invisible Threats in Plain Sight
In the world of cybersecurity, not all threats shout their presence. Some whisper.
Rootkits and bootkits are masters of stealth—malicious tools designed to stay hidden, bypass detection, and silently take control of a system from the inside out.
While ransomware and phishing attacks often make headlines, rootkits and bootkits operate in the shadows, often unnoticed for weeks, months, or even years. Their primary objective? Persistence and invisibility. Once installed, they can alter system behavior, hide malicious processes, intercept data, or open backdoors, all while staying under the radar of antivirus and endpoint security tools.
For ethical hackers and security researchers, understanding how these threats work is essential. Detecting a rootkit or a bootkit is not just a matter of scanning—it requires deep system knowledge, awareness of low-level architecture, and the use of specialized tools.
In this article, we'll take you on a journey through:
-
How rootkits and bootkits differ
-
How attackers use them in real-world scenarios
-
And most importantly, how you—as an ethical hacker—can spot and stop them before they cause damage.
🧬 Time to dive into the world of stealth malware. Let's expose what's meant to stay hidden.q
🐚 What Is a Rootkit? Anatomy of a System Intruder
A rootkit is a type of malware designed to gain and maintain unauthorized access to a computer system—while remaining undetected. The name comes from the Unix/Linux term "root", which refers to the highest level of system privileges. A rootkit, once installed, can grant an attacker root-level (admin) control, allowing them to execute commands, hide files, steal data, or install additional malware.
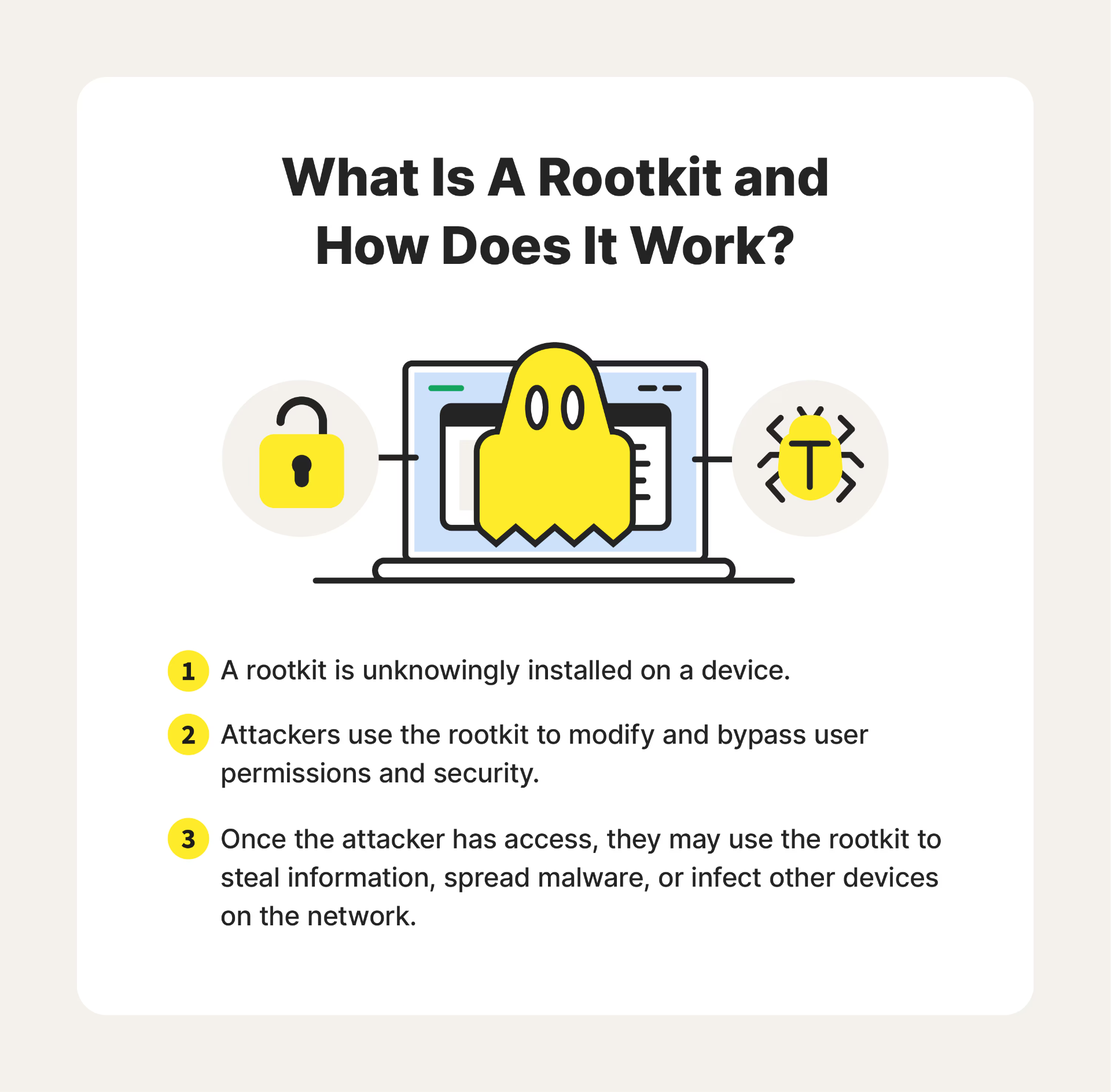
🛠️ But what makes rootkits especially dangerous isn't just what they do—it's how they do it. Their real power lies in their ability to stay invisible to the user and even to most antivirus solutions.
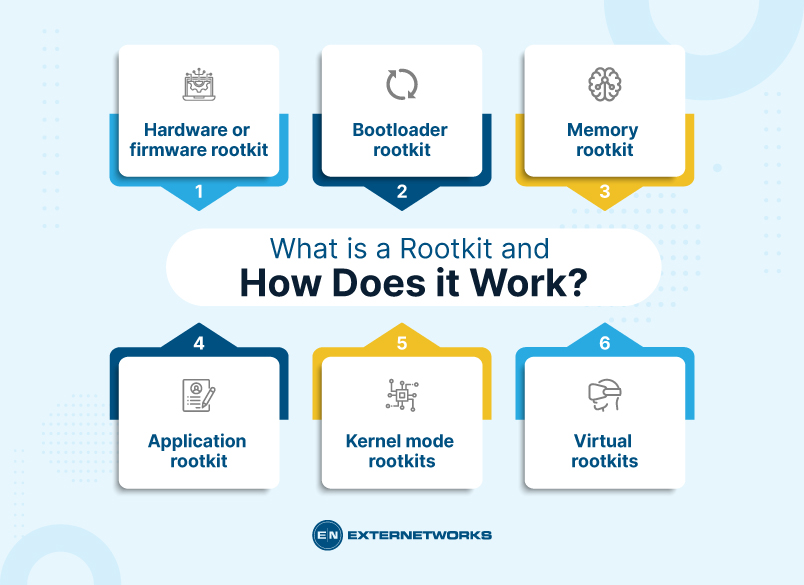
⚙️ Types of Rootkits
Rootkits come in various forms depending on where they reside and how deeply they integrate into the system:
-
User-Mode Rootkits
These operate at the application level, replacing standard system binaries or injecting malicious code into user-space processes. Easier to detect, but still a threat. -
Kernel-Mode Rootkits
These run in the core of the operating system. They can hook system calls, manipulate the kernel directly, and are extremely hard to detect. -
Firmware Rootkits
Installed in firmware (e.g., BIOS, UEFI, network cards), surviving OS reinstalls and even hard drive formatting. Very advanced and rare. -
Hypervisor (Virtualized) Rootkits
These operate below the OS, tricking the operating system into thinking it's running on real hardware. Very stealthy and sophisticated.
🕵️♂️ What Can a Rootkit Do?
Once active, a rootkit can:
-
Hide files, directories, registry keys, and processes
-
Intercept system calls and tamper with logs
-
Create backdoors and remote access channels
-
Disable security tools and updates
-
Log keystrokes and steal credentials
In short: they become ghosts inside your machine, doing the attacker's bidding without you ever knowing.
Rootkits don't act alone. They're often bundled with other malware, such as trojans or ransomware, to give attackers the persistence and stealth they need for long-term operations—especially in Advanced Persistent Threats (APTs).
🎯 If you can't see it, you can't fight it. That's why understanding rootkits is step one in becoming a smarter ethical hacker.
💣 What Is a Bootkit? Malware That Strikes Before the OS
If rootkits are stealthy, bootkits take stealth to another level—they infect a system before the operating system even starts. A bootkit is a type of malware that targets the boot process of a computer, typically by modifying the Master Boot Record (MBR), Volume Boot Record (VBR), or even the UEFI firmware itself.
🎯 The goal? To gain control of the system as early as possible, allowing the attacker to load malicious code before any security defenses are active.
🧬 How Bootkits Work
Bootkits operate during the bootstrapping phase—that critical moment when a computer powers on and the operating system is about to load. By infecting the bootloader or firmware, a bootkit can:
-
Inject malicious code directly into memory
-
Decrypt and load a custom payload silently
-
Hijack the OS loading sequence
-
Establish persistence before the OS defenses can react
Because they execute before the OS kernel, they have near-total control of the system, making detection extremely difficult.
⚠️ Where Do Bootkits Hide?
Some common hiding places for bootkits include:
-
Master Boot Record (MBR): The first sector of the disk that contains boot code
-
UEFI Firmware: The modern replacement for BIOS, stored on the motherboard chip
-
Bootloaders (like GRUB): Modified to inject malicious instructions
-
VBR (Volume Boot Record): A sector that loads the OS from a specific partition
Bootkits in UEFI are particularly dangerous—they can persist across OS reinstallations, bypass secure boot, and even reinfect clean systems unless the firmware itself is rewritten or reflashed.
🔐 A Real-World Example
One of the most infamous bootkits is "LoJax", part of a 2018 APT campaign. It infected the UEFI firmware of targeted systems, giving attackers persistence at the firmware level—virtually impossible to remove without specialized tools or hardware reflashing.
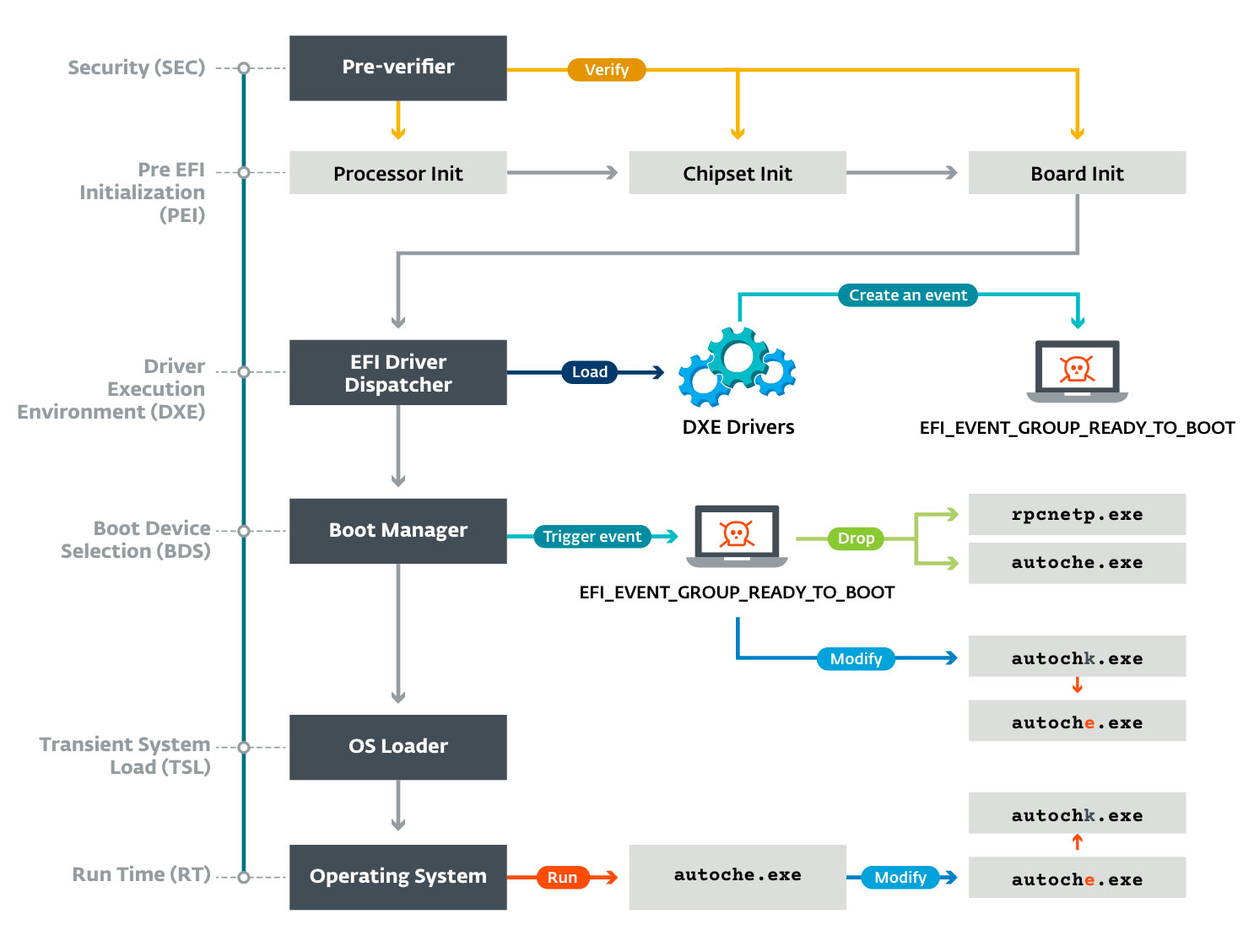
🧨 Bootkits don't just hide in your system—they hide beneath it.
For ethical hackers, understanding bootkits means learning to think below the OS, analyzing firmware integrity, and using forensic tools that operate outside the traditional system boundaries.
⚔️ Rootkits vs Bootkits: Similar Tactics, Different Layers
At first glance, rootkits and bootkits might seem like two sides of the same coin. Both are designed to provide stealth, persistence, and privileged access—while remaining undetected. But in practice, they operate at very different layers of the system, and that changes everything.
Let's break down the key differences—and why they matter from a hacker's point of view.
🧠 Level of Operation
-
Rootkits:
Typically operate within the OS, either at the user level (modifying system files or processes) or kernel level (manipulating core system calls).
➤ They're active after the system is running. -
Bootkits:
Infect the pre-boot environment, such as the MBR, VBR, or UEFI firmware, allowing them to execute before the operating system loads.
➤ They act before the system even wakes up.
🔍 Stealth Capabilities
-
Rootkits are stealthy inside the OS. They often hook or patch system functions to hide their presence from users and security tools.
-
Bootkits are stealthy beneath the OS. Since they execute first, they can load malicious components that appear "legitimate" to the system once it starts.
💾 Persistence
-
Rootkits:
Can persist through reboots, but not always through full reinstalls or disk wipes (unless paired with a deeper infection). -
Bootkits:
Can survive OS reinstalls and hard drive formatting—especially if the firmware itself is infected. That makes them extremely resilient.
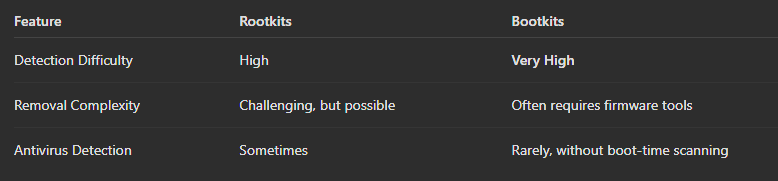
⚔️ Detection & Removal
🎯 Use in Attacks
-
Rootkits are common in post-exploitation, used to maintain control or hide lateral movement.
-
Bootkits are rarer but used in targeted, high-value attacks, like espionage, supply chain compromise, or APT campaigns.
🧩 In short: rootkits dig in deep—but bootkits go deeper.
For ethical hackers and defenders, knowing the distinction isn't just academic—it shapes how you investigate, detect, and respond to stealth malware at every layer.
🛠️ How Attackers Install and Use Rootkits & Bootkits
Understanding how attackers get these stealthy tools inside your system is just as important as knowing what they do. Rootkits and bootkits aren't handed over on a silver platter—they require careful planning, targeted delivery, and exploitation of vulnerabilities.

🎯 Common Infection Vectors
-
Phishing and Social Engineering
Attackers often trick users into running malicious files or clicking on infected links, which install trojans that drop rootkits or bootkits behind the scenes. -
Exploiting Vulnerabilities
Zero-day exploits or unpatched system flaws can give attackers privileged access needed to install rootkits or modify the boot process for bootkits. -
Malicious Software Bundles
Sometimes rootkits are hidden inside pirated software, fake updates, or seemingly legitimate apps downloaded from untrusted sources. -
Supply Chain Attacks
Attackers compromise hardware or software providers to inject bootkits or rootkits before the system even reaches the end user.
🕵️♂️ Installation Techniques
-
Direct Kernel Hooking (Rootkits)
By hooking kernel functions or modifying kernel data structures, attackers make their malware invisible and gain control over system calls. -
MBR/VBR Manipulation (Bootkits)
Modifying the first sectors of the disk to load malicious boot code that starts before the OS. -
UEFI Firmware Modification
Injecting malicious code into firmware to gain persistence that survives OS reinstallations. -
Process Injection and DLL Hijacking
Injecting malicious code into trusted processes to hide payloads and avoid detection.
🎮 Objectives After Installation
-
Maintain persistent access without raising suspicion
-
Hide other malware (ransomware, keyloggers, spyware)
-
Steal sensitive data like credentials or financial info
-
Create backdoors for future remote control
-
Disrupt system integrity for sabotage or espionage
🔥 In the hands of skilled attackers, rootkits and bootkits become powerful weapons for long-term system compromise.
For ethical hackers, knowing these infection paths helps in building better defenses and simulating real-world attacks in pentests or red team operations.
🕵️♂️ Detection and Removal: Why It's So Damn Hard
Rootkits and bootkits are infamous for their ability to stay hidden—and this stealth makes them some of the toughest threats to detect and remove.
🔍 Why Are They So Hard to Detect?
-
Deep System Integration
Rootkits, especially kernel-mode ones, hook into core OS functions and modify system behavior at the lowest levels. Bootkits even run before the OS loads, making detection tools unaware of their presence. -
Bypassing Traditional Security
Standard antivirus software relies on scanning files and monitoring running processes. Rootkits can hide their files, processes, and even system logs, while bootkits load early, before these tools start. -
Firmware-Level Infection
Bootkits that infect firmware persist beyond OS reinstallations and disk wipes, requiring specialized hardware tools or firmware reflashing to remove.
🛠️ Tools and Techniques for Detection
-
Behavioral Analysis
Monitoring unusual system behavior, network traffic, or anomalies in system calls. -
Memory and Kernel Scanning
Tools like GMER, RootkitRevealer, or OSForensics try to detect hidden hooks or modified kernel structures. -
Firmware Integrity Checks
Utilities that verify UEFI or BIOS integrity, like Chipsec, can detect unauthorized firmware changes. -
Boot-Time Scanning
Scanning the system before the OS fully boots, using rescue disks or specialized environments.
⚔️ Challenges in Removal
-
Rootkits can disable security tools or reinstall themselves after removal attempts.
-
Bootkits may require firmware reflashing or complete hardware replacement.
-
In many cases, a full system wipe without firmware cleaning leaves systems vulnerable to reinfection.
🧠 Detecting and removing rootkits and bootkits isn't just about tools—it's about deep understanding and layered defense.
For ethical hackers, mastering detection techniques is crucial not only for defense but also for red teaming—testing real-world attack and persistence scenarios.
🕶️ Ethical Hacking Perspective: What You Need to Know
For ethical hackers, understanding rootkits and bootkits goes beyond theory—it's about applying that knowledge to find, analyze, and mitigate these threats in real-world environments.

🛡️ Why Ethical Hackers Must Know Rootkits & Bootkits
-
Detection Skills
Knowing how these malware operate helps ethical hackers spot subtle signs of infection that others might miss. -
Improved Penetration Testing
Simulating rootkit or bootkit infections during red team engagements can reveal weaknesses in an organization's defenses. -
Incident Response
If a rootkit or bootkit is suspected, ethical hackers assist in forensic analysis and containment strategies.
🧰 Tools for Ethical Hackers
-
Rootkit Detectors: Chkrootkit, rkhunter, GMER
-
Firmware Analyzers: Chipsec, UEFI Scanner
-
Memory Forensics: Volatility Framework, Rekall
-
Boot-Time Scanners: Rescue disks from Kaspersky, Bitdefender, or ESET
🔎 Best Practices
-
Always test malware detection in controlled lab environments—never on production systems.
-
Use virtual machines and snapshots to analyze rootkits or bootkits safely.
-
Stay updated on the latest rootkit/bootkit techniques and detection methods.
-
Understand the system architecture deeply—knowledge of OS internals, boot processes, and firmware is crucial.
💡 Ethical hacking is about staying one step ahead—knowing the invisible threats and how to expose them is part of that game.
🎯 Conclusion: Know Your Enemy to Defend Better
Rootkits and bootkits represent some of the most insidious and difficult-to-detect threats in modern cybersecurity. Their ability to hide deep within a system's core—or even beneath it—makes them formidable adversaries for any defender.
But as ethical hackers, knowledge is our greatest weapon. By understanding how these stealthy malware operate, where they hide, and the tactics they use to avoid detection, we can build stronger defenses and better protect the systems we care about.
Remember:
-
Rootkits live inside the operating system, manipulating it from within.
-
Bootkits infect the boot process or firmware, giving attackers control before the OS even loads.
-
Both require advanced skills and tools to detect and remove.
-
Ethical hackers must continuously learn and practice to stay ahead of these hidden dangers.
🛡️ Stay curious, stay vigilant, and never underestimate the power of what's hidden beneath the surface.
Thanks for reading—now go out there and root out those rootkits!
