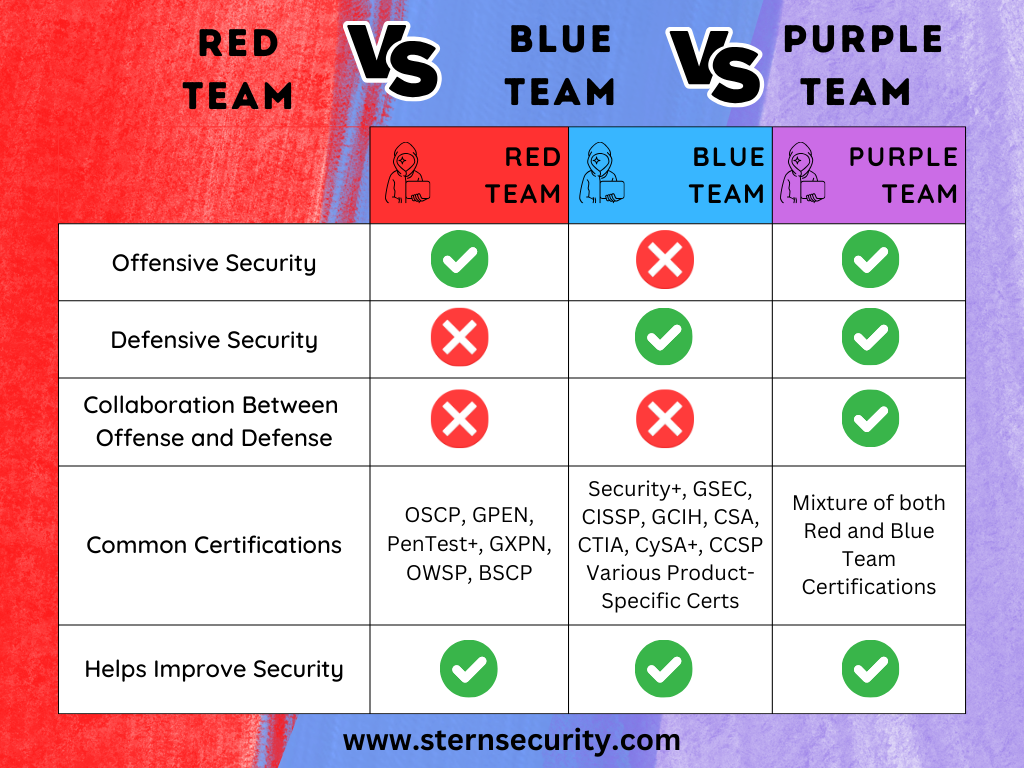
Red Team vs Blue Team: The War for Cybersecurity Supremacy

1. Introduction: The Cybersecurity Battlefield
In the ever-evolving world of cybersecurity, the battle between attackers and defenders never stops. With each technological advancement, cyber threats become more sophisticated, challenging the security of businesses, governments, and individuals alike. In this digital battleground, two critical forces emerge: the Red Team and the Blue Team.
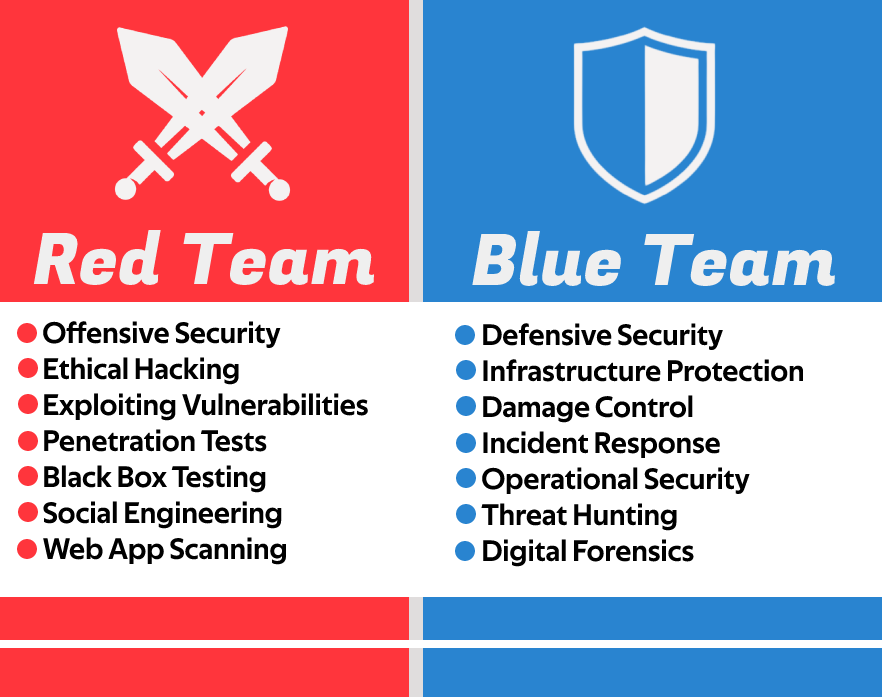
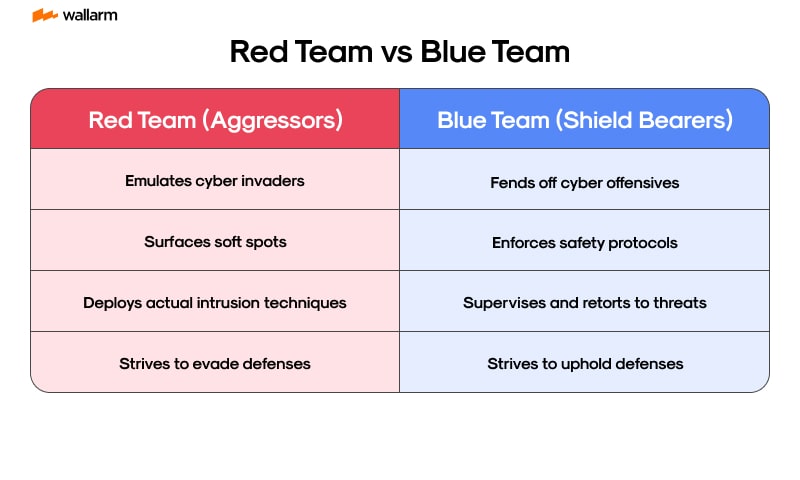
The Red Team consists of ethical hackers who simulate real-world cyberattacks to identify vulnerabilities before malicious hackers do. Their goal is to think and act like attackers, exposing weaknesses in an organization's security.
On the other hand, the Blue Team is responsible for defense. They focus on threat detection, incident response, and proactive security measures to safeguard systems, networks, and data from attacks.
This article will dive deep into the roles, techniques, and strategies of both teams, exploring their clash in cybersecurity exercises and how they ultimately work together to strengthen security.
2. Red Team: The Attackers
The Red Team plays the role of ethical hackers, simulating real-world cyberattacks to expose weaknesses in an organization's security infrastructure. Their mission is simple: think like a hacker, act like a hacker, and find vulnerabilities before real attackers do.
Key Objectives of the Red Team
- Identify security flaws in systems, applications, and networks.
- Exploit vulnerabilities to test how far an attacker could go.
- Challenge an organization's security policies and response mechanisms.
- Provide a detailed report with recommendations to strengthen defenses.
Common Red Team Techniques
To effectively simulate cyberattacks, Red Team professionals use a variety of offensive techniques, including:
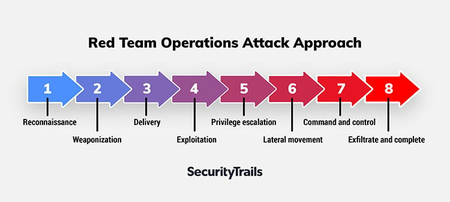
🔴 Phishing Attacks – Crafting deceptive emails or messages to trick employees into revealing sensitive information or downloading malware.
🔴 Exploiting Vulnerabilities – Finding and leveraging software bugs or misconfigurations to gain unauthorized access to systems.
🔴 Privilege Escalation – Moving from a low-level user account to an administrator or root-level access.
🔴 Lateral Movement – Navigating through an internal network after gaining initial access to reach high-value targets.
🔴 Social Engineering – Manipulating individuals into giving away credentials, access, or sensitive data.
Red Team Tools of the Trade
To conduct their attacks, Red Teams rely on advanced tools, including:

- Metasploit – A powerful penetration testing framework for exploiting vulnerabilities.
- Cobalt Strike – A tool for simulating advanced persistent threats (APT) and post-exploitation activities.
- Burp Suite – Used for web application security testing.
- Nmap – A network scanning tool to identify open ports and services.
- Mimikatz – A tool for extracting credentials from Windows systems.
The Red Team Mindset
Red Teamers must adopt the mindset of a real attacker. They analyze an organization's security posture from an adversarial perspective, always looking for the weakest link. However, unlike malicious hackers, their goal is not to harm but to improve security by exposing vulnerabilities before they can be exploited by real threats.
3. Blue Team: The Defenders
While the Red Team focuses on attacking, the Blue Team is responsible for defending. Their primary goal is to detect, prevent, and respond to cyber threats, ensuring that an organization's security remains strong even against sophisticated attacks. They act as the last line of defense, working tirelessly to stop breaches before they happen—or minimize damage when they do.
Key Objectives of the Blue Team
- Continuously monitor networks and systems for suspicious activity.
- Detect and analyze security threats in real time.
- Implement defensive measures to block attacks.
- Respond to security incidents quickly and effectively.
- Strengthen an organization's overall security posture through risk assessments and training.
Common Blue Team Defensive Strategies
🔵 Threat Detection & Monitoring – Using tools like SIEM (Security Information and Event Management) to analyze logs and detect anomalies.
🔵 Network Defense – Implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and endpoint security solutions.
🔵 Incident Response & Forensics – Investigating cyber incidents, containing threats, and recovering from attacks.
🔵 Vulnerability Management – Regularly scanning and patching systems to eliminate security gaps before attackers exploit them.
🔵 User Awareness & Training – Educating employees on cybersecurity best practices to prevent human error-based attacks like phishing.
Blue Team Tools of the Trade
To effectively protect an organization, Blue Teams use a variety of security tools, including:
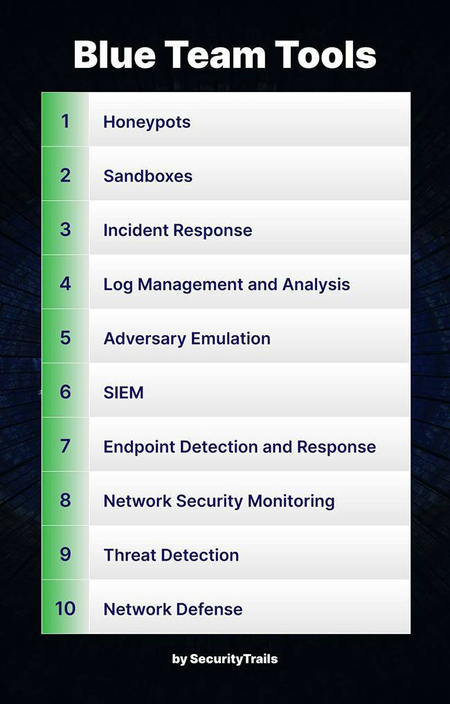
- Splunk / ELK Stack – For log analysis and real-time security monitoring.
- Wireshark – A packet analyzer for network traffic inspection.
- Snort / Suricata – Intrusion detection and prevention systems (IDS/IPS).
- OSSEC – A host-based intrusion detection system (HIDS).
- Cyber Kill Chain Framework – A methodology for tracking and mitigating attacks step by step.
The Blue Team Mindset
Blue Team members must think like defenders, constantly anticipating attacks and staying ahead of threats. Their work is never done—cybersecurity is a continuous battle, and new vulnerabilities emerge every day. Unlike the Red Team, which simulates attacks in controlled environments, Blue Teams deal with real threats in real time, making their role critical in cybersecurity.
4. The Battle Tactics: How Red and Blue Teams Interact
The true power of cybersecurity lies in the dynamic clash between the Red Team and the Blue Team. This confrontation isn't just a competition—it's a strategic exercise designed to strengthen an organization's security posture.
How a Red Team vs Blue Team Exercise Works
A typical cybersecurity exercise follows a structured format where both teams operate in a controlled yet realistic environment. The process usually unfolds in the following stages:
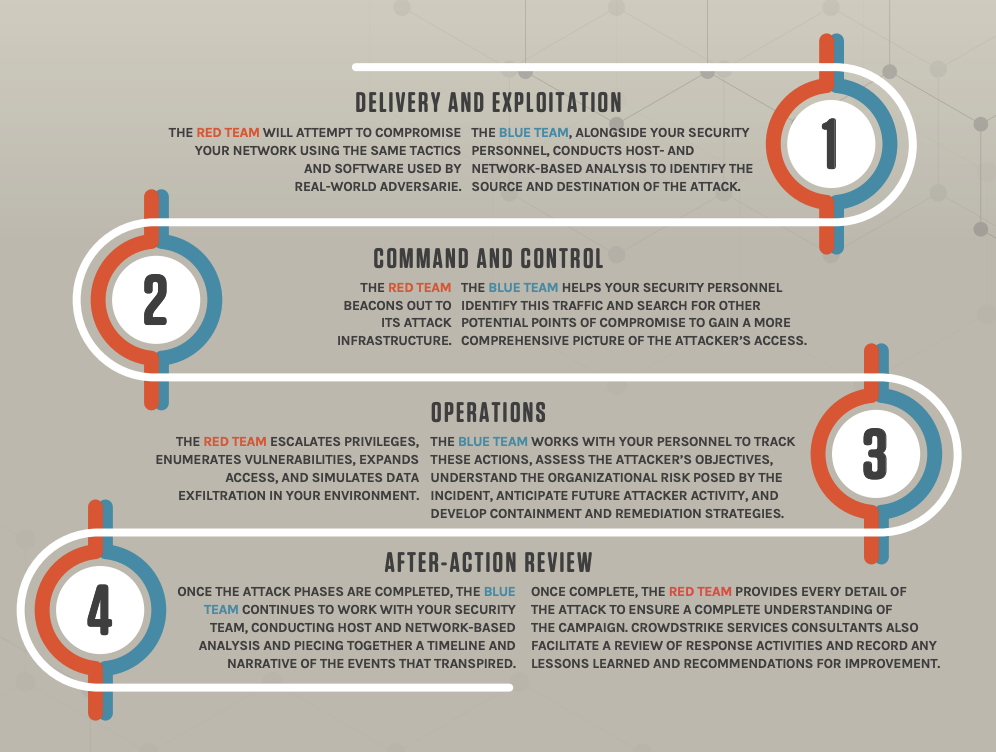
1️⃣ Reconnaissance & Attack (Red Team Initiates)
- The Red Team gathers intelligence on the target organization, identifying potential entry points and weaknesses.
- They launch an attack using techniques such as phishing, vulnerability exploitation, and privilege escalation.
- Their goal is to infiltrate the system, gain persistence, and simulate a real-world cyberattack without causing actual harm.
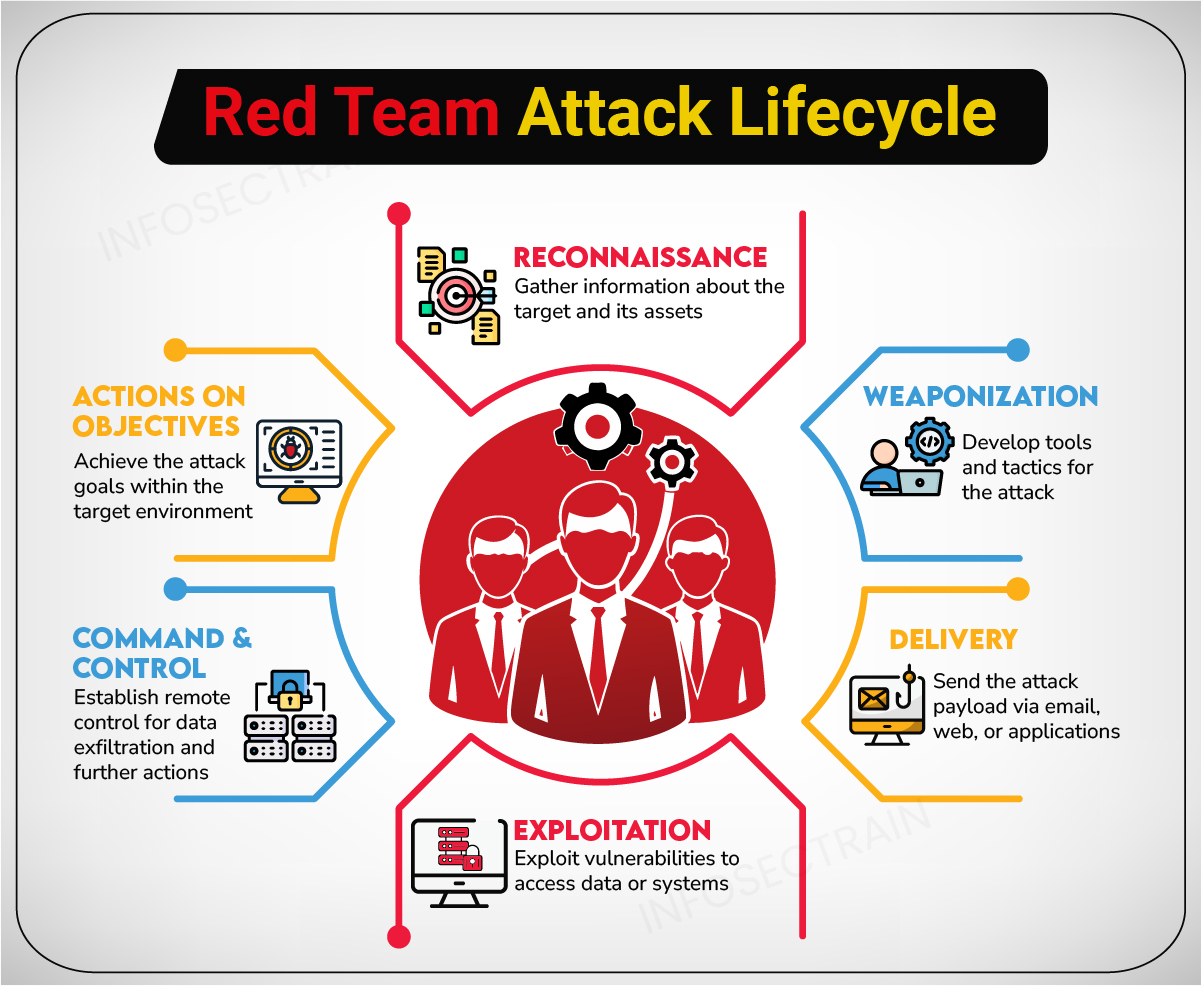
2️⃣ Detection & Response (Blue Team Reacts)
- The Blue Team continuously monitors systems, searching for anomalies or indicators of compromise (IoCs).
- If an intrusion is detected, they investigate, contain, and neutralize the threat.
- They analyze logs, alert security personnel, and deploy countermeasures such as blocking IPs or isolating compromised machines.
3️⃣ Escalation & Countermeasures
- If the Red Team successfully bypasses defenses, they attempt to move laterally within the network.
- The Blue Team adapts, implementing stronger security measures and reinforcing weak points.
- Both teams engage in a constant back-and-forth, testing the effectiveness of the organization's cybersecurity protocols.
4️⃣ Post-Exercise Review (Lessons Learned)
- After the simulation, both teams meet to discuss the attack path, the defensive response, and what could be improved.
- The Red Team explains how they bypassed security controls, exposing critical vulnerabilities.
- The Blue Team shares insights on detection gaps and areas that need stronger protection.
- A final report is generated, detailing the findings and offering recommendations for future security enhancements.
The Real-World Impact of These Exercises
💥 Stronger Defense Mechanisms – Organizations can refine their security policies based on real attack scenarios.
💥 Faster Incident Response – Blue Teams improve their reaction time and ability to contain threats.
💥 Proactive Security Mindset – Instead of waiting for an attack, companies can simulate threats and fix vulnerabilities before they are exploited by real hackers.
The battle between Red and Blue Teams isn't about winning or losing—it's about growth, learning, and continuous improvement. This constant cycle of attack, defense, and analysis is what keeps organizations one step ahead in the ever-evolving world of cybersecurity.
5. The Importance of Collaboration: Red and Blue Team Synergy
While Red and Blue Teams are often seen as rivals, the true power of cybersecurity lies in their collaboration. The ultimate goal isn't for one side to "win"—it's to create a security strategy that continuously evolves and improves. This is where the Purple Team concept comes into play.
What is the Purple Team?
The Purple Team is not a separate entity but rather a collaborative approach where the Red and Blue Teams share insights to enhance overall security. Instead of working in isolation, they exchange knowledge in real time, improving both attack and defense strategies.
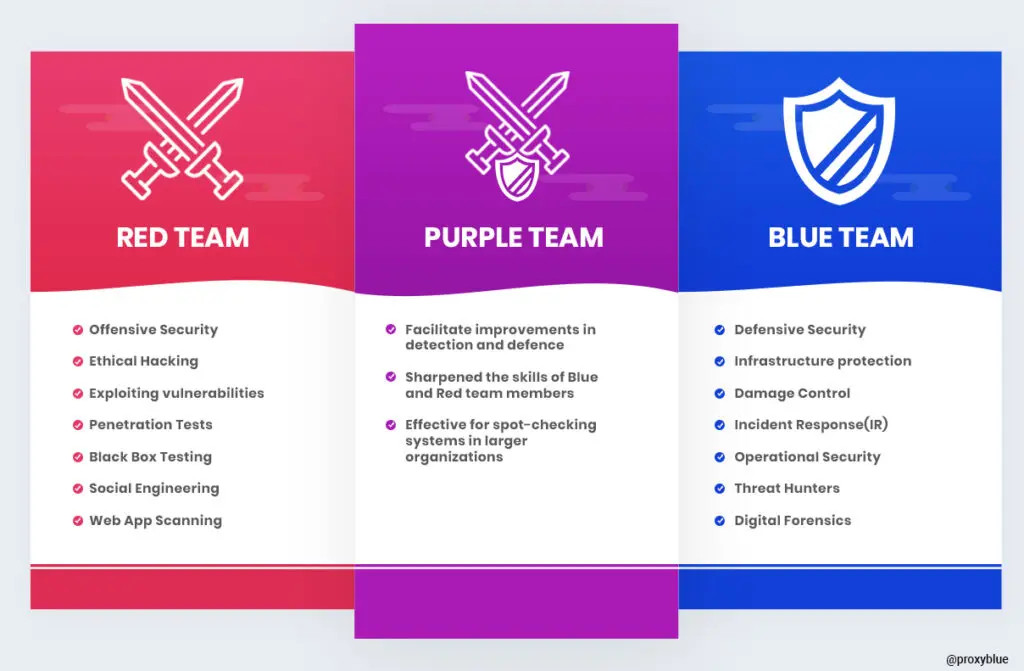
How Red and Blue Teams Benefit from Collaboration
🔴 How the Red Team Helps the Blue Team:
- Exposes blind spots in security systems.
- Demonstrates real-world attack techniques.
- Helps Blue Teams build stronger detection and response mechanisms.
🔵 How the Blue Team Helps the Red Team:
- Provides intelligence on existing security measures.
- Helps Red Team refine attack simulations to be more realistic.
- Enhances post-attack analysis by sharing logs and incident reports.
Key Elements of a Strong Red-Blue Collaboration

✅ Threat Intelligence Sharing – Red and Blue Teams should exchange data on emerging threats, attack techniques, and detection methods.
✅ Real-Time Feedback Loops – Instead of waiting for the post-exercise review, teams should provide feedback immediately to adjust tactics and defenses on the fly.
✅ Continuous Learning & Adaptation – Cyber threats evolve daily. Red and Blue Teams must stay updated on new vulnerabilities, attack trends, and defense mechanisms.
✅ Automated Security Testing – Leveraging AI-driven security tools can help both teams simulate attacks and analyze defensive responses faster.
The Shift from Adversarial to Collaborative Security
Organizations that embrace the Purple Team mindset move beyond the traditional "attack vs. defense" dynamic. Instead, they create a proactive security culture where offensive and defensive experts work together to build resilient cybersecurity frameworks.
By fostering collaboration between Red and Blue Teams, companies can significantly enhance their ability to detect, prevent, and respond to cyber threats—before real attackers strike.
6. Real-World Applications: The Impact of Red vs. Blue Team Exercises
The battle between Red and Blue Teams isn't just theoretical—it has real-world applications that directly impact an organization's cybersecurity posture. Companies, government agencies, and even military organizations regularly conduct Red vs. Blue Team exercises to test and improve their defenses against actual cyber threats.

How Organizations Use Red vs. Blue Team Exercises
🏢 Corporate Cybersecurity Drills
- Companies simulate cyberattacks to test their ability to detect and respond to breaches.
- These exercises help businesses train employees and refine incident response procedures.
🏛️ Government & Military Cyber Warfare Simulations
- National security agencies run large-scale cyber warfare scenarios to prepare for nation-state attacks.
- Cybersecurity units practice defending critical infrastructure like power grids, financial systems, and communication networks.
🏥 Healthcare Cyber Resilience Testing
- Hospitals and medical organizations conduct Red vs. Blue Team drills to protect sensitive patient data from ransomware and cyberattacks.
- These simulations help ensure compliance with HIPAA and other data security regulations.
💰 Financial Sector Cyber Defense
- Banks and financial institutions simulate attacks on online banking systems and payment gateways.
- They use Red Team exercises to uncover weaknesses in fraud detection and secure transaction systems.
Notable Case Studies & Lessons Learned
🔹 The 2016 SWIFT Banking Attack
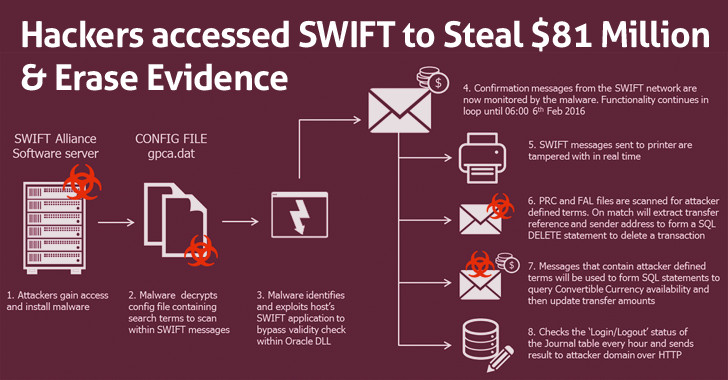
- Hackers stole $81 million from Bangladesh's central bank by exploiting vulnerabilities in the SWIFT banking network.
- Financial institutions worldwide have since adopted Red Teaming strategies to prevent similar incidents.
🔹 U.S. Department of Defense "Hack the Pentagon" Program

- The U.S. government launched a Red Teaming initiative inviting ethical hackers to test Pentagon systems.
- The program uncovered critical vulnerabilities that were patched before they could be exploited by real adversaries.
🔹 2017 WannaCry Ransomware Attack

- The WannaCry worm exploited outdated Windows systems, causing global disruptions in hospitals, businesses, and transportation networks.
- Organizations worldwide increased Blue Team efforts by improving patch management and endpoint security after the attack.
The Long-Term Impact of Red vs. Blue Team Exercises
✅ Stronger Cyber Resilience – Companies and governments can simulate, test, and improve their security defenses before real-world attacks happen.
✅ Faster Threat Response – Security teams refine their incident response plans, reducing downtime and financial losses during cyber incidents.
✅ Improved Security Awareness – Employees, IT teams, and executives become more cyber-aware, reducing the risk of human-error-based breaches.
Red vs. Blue Team exercises are no longer optional—they are essential in today's threat landscape. Organizations that fail to test their security measures risk becoming the next big cybersecurity breach headline.
7. Future of Red Team vs. Blue Team: What's Next?
The cybersecurity battlefield is constantly evolving. As cyber threats become more sophisticated, both Red and Blue Teams must adapt to new challenges, technologies, and attack methods. But what does the future hold for Red vs. Blue Team exercises?
Emerging Trends in Cybersecurity Warfare
🚀 AI-Powered Attacks & Defenses
- Hackers are using AI-driven malware that adapts in real-time, making Red Team simulations more complex.
- Blue Teams are countering this with AI-based threat detection systems, capable of identifying and mitigating attacks instantly.
🌐 Cybersecurity in the Age of Quantum Computing
- Quantum computing could potentially break current encryption standards, forcing Blue Teams to develop post-quantum cryptography solutions.
- Red Teams are already researching how quantum-powered attacks could bypass traditional security measures.
🛡️ Zero Trust Architecture (ZTA) Becomes Standard
- Organizations are shifting toward a Zero Trust security model, where no user or system is trusted by default.
- Red Teams test whether Zero Trust implementations have gaps, while Blue Teams refine their identity-based access controls and behavioral monitoring.
🎭 Cyber Deception Strategies
- Blue Teams are leveraging honeypots and deception networks to trick attackers and study their tactics.
- Red Teams must now evolve their reconnaissance techniques to avoid these security traps.
Will the Red vs. Blue Model Change?
The traditional Red vs. Blue Team model is evolving into something more collaborative and continuous. Instead of periodic security exercises, organizations are adopting real-time attack simulations with automated testing tools.
🔮 The Rise of Continuous Purple Teaming
- Purple Teaming will shift from an occasional exercise to a permanent cybersecurity function.
- AI-driven simulations will allow for constant attack and defense adjustments, making security a 24/7 battle.
💡 Proactive Security Over Reactive Defense
- Instead of waiting for Red Team exercises, companies will integrate offensive security into everyday risk management.
- The focus will move from responding to attacks to preventing breaches before they happen.
Final Thoughts on the Future of Cybersecurity Battles
Red vs. Blue Teaming will never disappear—but the way organizations conduct cybersecurity exercises must evolve. The future is not about competition between attackers and defenders, but about collaboration, automation, and proactive security strategies.
Organizations that fail to adapt to these new cybersecurity trends risk falling behind in the digital arms race. Those who embrace innovation will stay ahead of attackers and build cyber defenses that are truly unbreakable.
8. Conclusion: The Never-Ending Cyber War
The battle between Red Teams and Blue Teams is not just an exercise—it's a critical component of modern cybersecurity. As cyber threats become more advanced, organizations must continuously test, adapt, and improve their security strategies.
Key Takeaways from the Red vs. Blue Team Battle
✔️ Red Teams are essential for exposing vulnerabilities before real hackers can exploit them.
✔️ Blue Teams serve as the last line of defense, detecting, mitigating, and responding to cyberattacks.
✔️ Collaboration is the key to success—when Red and Blue Teams work together, security improves exponentially.
✔️ Cyber threats evolve daily, making continuous testing and adaptation a necessity.
✔️ The future of cybersecurity is proactive, leveraging AI, automation, and real-time attack simulations.
Final Thought: There Is No Finish Line in Cybersecurity
In this never-ending cyber war, there's no such thing as being 100% secure. The only way to stay ahead of cybercriminals is through constant learning, testing, and improvement.
Organizations that embrace the Red vs. Blue Team approach—and evolve it into a continuous, collaborative security strategy—will stand the best chance of surviving and thriving in the digital battlefield.
So, the question isn't if your security will be tested. The question is: Are you ready for the next attack?
