Ransomware-as-a-Service (RaaS): Fighting the Industry

Introduction
Ransomware has become one of the most pressing challenges in the cybersecurity landscape. Over the past decade, the evolution of ransomware has reached new heights with the emergence of Ransomware-as-a-Service (RaaS). This business model has lowered the barrier to entry for cybercriminals, enabling even those with minimal technical expertise to launch devastating ransomware campaigns.
The accessibility and profitability of RaaS have created a booming underground economy, making it one of the fastest-growing threats to individuals, businesses, and governments alike. Unlike traditional ransomware attacks, which were often isolated and limited in scope, RaaS operates on a global scale, affecting critical infrastructure, financial institutions, and even healthcare systems.
In this article, we explore the world of RaaS, its mechanics, and the innovative strategies being developed to combat it. By understanding the structure and impact of RaaS, organizations can better prepare to defend against this modern-day menace.
What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service refers to a business model within the cybercrime ecosystem where ransomware developers lease their malicious software to affiliates. These affiliates then use the ransomware to execute attacks, often targeting organizations, governments, and individuals. The proceeds from ransom payments are typically shared between the developer and the affiliate, making RaaS a highly profitable venture for both parties.
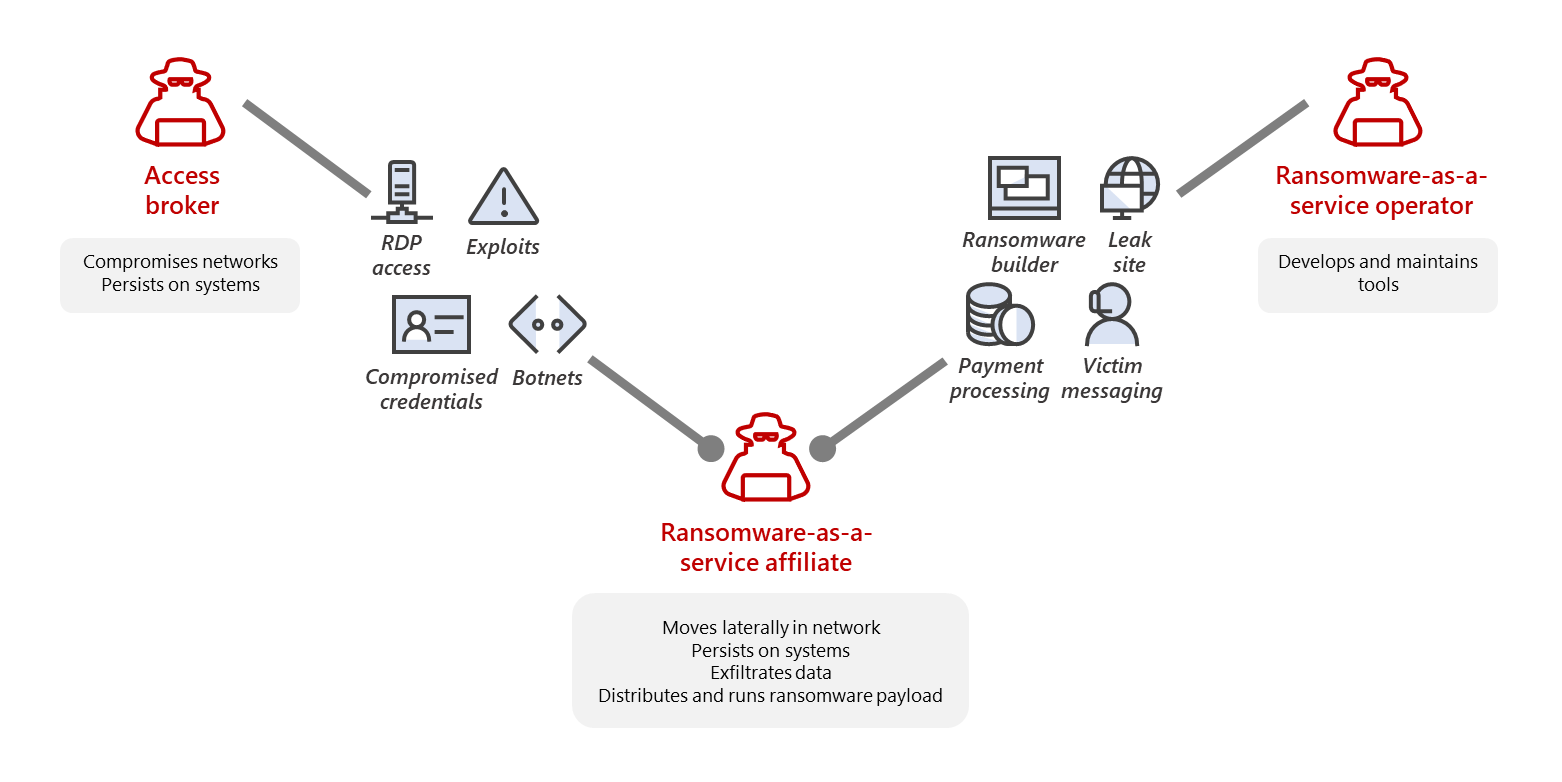
Key Features of RaaS
Ease of Access: RaaS platforms often operate like legitimate SaaS (Software-as-a-Service) platforms, complete with user-friendly dashboards, customer support, and even "how-to" guides.
Revenue Sharing Models: Developers typically take 20-30% of the ransom payments, while affiliates pocket the rest.
Customization: Affiliates can tailor ransomware payloads to target specific systems or industries.
Low Barrier to Entry: With no need for coding expertise, even novice cybercriminals can launch devastating attacks.
Popular RaaS Platforms
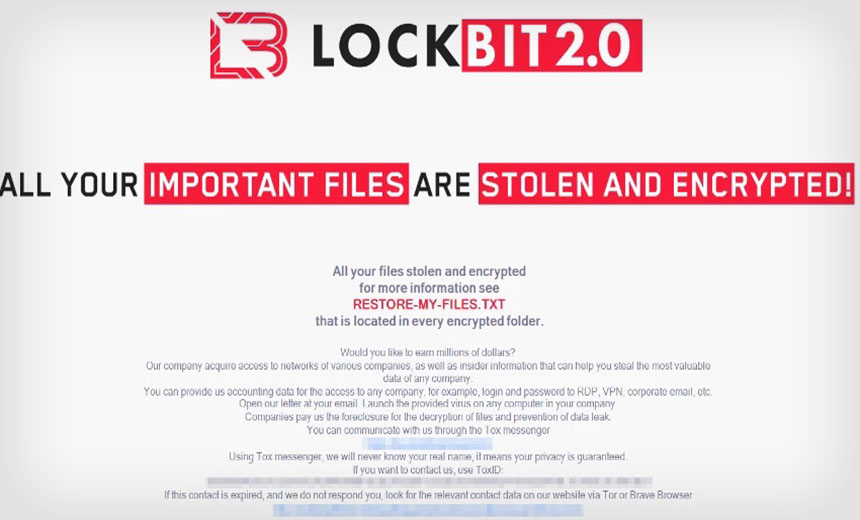
REvil: A notorious RaaS group known for high-profile attacks on global corporations.
DarkSide: Infamous for targeting Colonial Pipeline in 2021, showcasing the real-world impact of RaaS.
LockBit: A leading RaaS platform offering advanced encryption and exfiltration capabilities.
The Impact of RaaS on Cybersecurity
Increased Frequency and Sophistication of Attacks
RaaS has significantly lowered the technical barriers to entry for cybercrime. As a result, there has been an exponential increase in ransomware attacks globally. These attacks are also becoming more sophisticated, leveraging zero-day vulnerabilities and advanced evasion techniques.
Targeting Critical Infrastructure
RaaS operators are increasingly focusing on critical infrastructure, including healthcare, energy, and transportation sectors. Such attacks can disrupt essential services, endanger lives, and cause widespread panic.
Economic and Reputational Damage
The financial impact of RaaS-fueled ransomware attacks is staggering. Victims face costs related to ransom payments, downtime, recovery, and lost revenue. Additionally, the reputational damage can be irreparable, leading to a loss of customer trust and future business opportunities.
Combating RaaS: The Role of Ethical Hackers
Ethical hackers play a crucial role in countering the RaaS industry. By simulating attacks, identifying vulnerabilities, and developing countermeasures, they help organizations strengthen their defenses against ransomware threats.

Techniques Used by Ethical Hackers
Threat Hunting: Ethical hackers proactively search for indicators of compromise (IOCs) to detect and mitigate ransomware campaigns before they cause harm.
Reverse Engineering: By dissecting ransomware samples, ethical hackers can uncover their inner workings, including encryption methods and command-and-control (C2) server communication.
Penetration Testing: Simulating ransomware attacks helps organizations identify weaknesses in their networks and patch them before malicious actors can exploit them.
Decryption Tools: Ethical hackers collaborate with cybersecurity firms and law enforcement to develop decryption tools that help victims recover their data without paying ransoms.
Key Strategies for Organizations to Defend Against RaaS
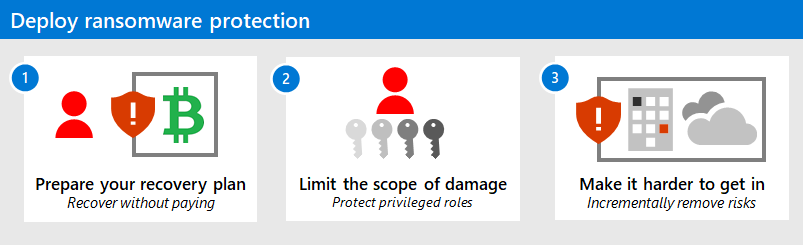
Regular Backups
Maintain offline, encrypted backups of critical data to ensure recovery in case of an attack.
Endpoint Detection and Response (EDR)
Deploy advanced EDR solutions to monitor and respond to suspicious activity in real-time.
Employee Training
Educate employees on phishing tactics and other common vectors used in ransomware attacks.
Zero Trust Architecture
Implement Zero Trust principles to minimize access to sensitive resources and prevent lateral movement within the network.
Patch Management
Regularly update software and systems to address known vulnerabilities.
Global Efforts to Dismantle RaaS Operations
Law Enforcement Collaboration
Agencies like Europol, Interpol, and the FBI are working with cybersecurity firms to track and shut down RaaS operators. For example, the takedown of the REvil operation in 2022 demonstrated the effectiveness of coordinated international efforts.

Public-Private Partnerships
Collaboration between governments and private cybersecurity firms has led to the development of threat intelligence-sharing platforms, enabling faster detection and response to ransomware threats.
Legislation and Sanctions
Governments are introducing stricter regulations and imposing sanctions on nations and entities harboring ransomware operators. These measures aim to disrupt the financial networks supporting RaaS activities.
The Future of RaaS: What to Expect
As cybersecurity defenses improve, RaaS operators are likely to adopt more advanced tactics, including the integration of AI for automated attacks and the use of cryptocurrency mixers to evade financial tracking. Ethical hackers and cybersecurity professionals must remain vigilant, continuously adapting their strategies to stay ahead of these evolving threats.
Conclusion
Ransomware-as-a-Service represents a significant challenge for the global cybersecurity community. By democratizing access to sophisticated ransomware tools, RaaS has lowered the barrier to entry for cybercrime, resulting in a surge of attacks. However, through proactive measures, ethical hacking, and international collaboration, the tide can be turned against this pervasive threat. Organizations must act decisively, implementing robust defenses and fostering a culture of cybersecurity awareness to protect themselves in an increasingly hostile digital landscape.
