One of the First Steps in Hacking: Port Scanning

Pentesting is regimented with rules to follow, steps, and the first of them is Port Scanning, to detect open services and understand where to go. Because if we don't know where to attack, we won't get anywhere.
So, in this tutorial, we will show you how to perform port scanning and discover which ones are open (and filtered).
Let's dive in!
What is port scanning?
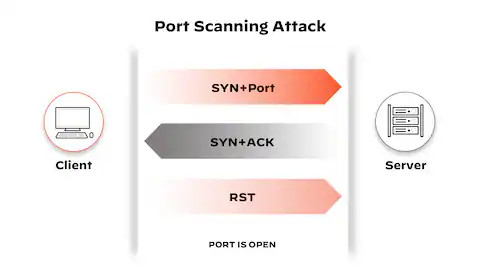
Port scanning is a fundamental technique in cybersecurity used to identify open ports in a computer system. Each port serves as a specific connection point, facilitating communication between different services or applications within a network. Associated with a unique number and designated for specific purposes, each port plays a crucial role in network architecture.
The port scanning process involves sending requests across the network to determine which ports are active and responsive. This practice provides cybersecurity professionals with a deeper understanding of network topology, enabling them to identify running services and assess potential vulnerabilities. Execution of this process becomes essential in the realm of pentesting (penetration testing) and cybersecurity, offering valuable insights into system security and empowering the implementation of preventive measures to strengthen it against potential threats.
Which protocols can be scanned?
Several protocols can be scanned during the port scanning process. But the most common protocols are:
TCP (Transmission Control Protocol): This is the most widely used protocol and the primary focus in port scanning. It is responsible for establishing reliable connections between devices.
UDP (User Datagram Protocol): In contrast to TCP, UDP is a connectionless protocol used for data transmission where speed is more crucial than data integrity. Some applications and services utilize UDP, making it important to scan UDP ports as well.
- SCTP (Stream Control Transmission Protocol): Similar to TCP, SCTP is another transport protocol that can be used in specific applications.
During a port scanning procedure, scanners can explore both TCP and UDP ports to identify running services and assess the security of a system or network. It's important to note that port scanning should be conducted ethically and in compliance with local laws and regulations to avoid legal consequences.
How to scan ports?
There are many ways to scan ports, but in this article, we will focus only on the essential and most important aspects. We will specifically scan the TCP and UDP protocols.
Why only TCP and UDP?
Because they are the most commonly used, crucial, and in most cases, we will only use these two protocols in pentesting tasks.
Method #1: Using NMap
NMap, which stands for 'Network Mapper', is a widely used open-source tool for network discovery and auditing. Developed by Gordon Lyon, also known as Fyodor Vaskovich, Nmap is renowned for its effectiveness in port scanning and network mapping, enabling security professionals to assess the security of computer systems and networks.
This tool provides various functionalities, such as detecting hosts on a network, identifying services and software versions running on those hosts, and evaluating potential vulnerabilities. NMap is highly configurable and can be used in various ways, from simple scans to complex network explorations.
The versatility and robustness of Nmap make it a preferred choice for both security professionals and technology enthusiasts looking to understand network topology and enhance computer security.

Installation of NMap
To install NMap in Linux, we can use APT:
- sudo apt-get update && sudo apt install -y nmap
Using NMap for TCP Port Scanning
Now, using NMap is quite easy, but it requires attention because there are many parameters that we can utilize.
You can use the command 'nmap IP', for example:
- nmap 192.168.1.1
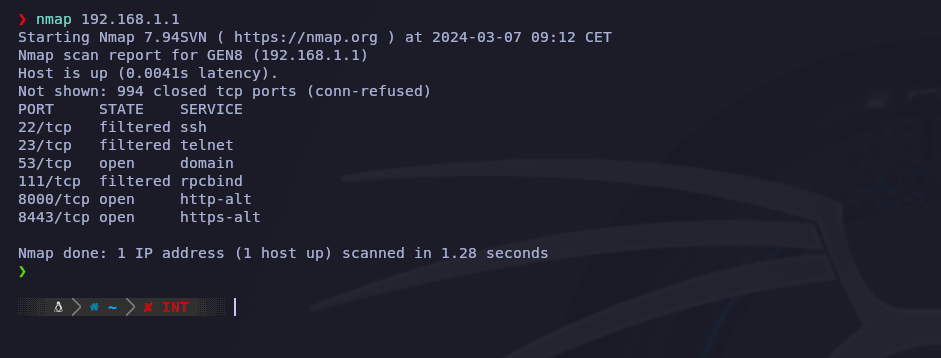
However, I personally don't recommend this, as it doesn't constitute a comprehensive port scan!
Instead, we can combine the following parameters to perform a powerful and comprehensive scan, as it scans all ports and accurately detects whether they are truly open or if it's a false positive (not displaying the latter). Sending 5000 packets per second to expedite the process and deactivating host discovery via ARP protocol to further enhance performance, along with disabling DNS resolution, will allow us to conduct the scan thoroughly and swiftly!
Follow these steps:
- sudo nmap -sS -p- --open --min-rate 5000 -vvv -n -Pn 192.168.1.1
The parameters used in the previous command are explained as follows:
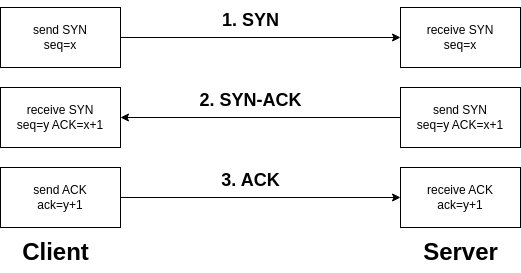
- "-sS": This option enables the TCP SYN scan. It exclusively scans TCP ports using the SYN-ACK process. Here's how it works: the scanner sends a SYN packet to the target port, and if the port is open, it responds with a SYN-ACK. If the attacker receives this response, it indicates that the port is indeed open.
- "-p-": Scans all 65535 existing ports.
- "--open": Displays only open ports and conceals ports with states such as "Filtered" or "Closed".
- "--min-rate 5000": Sends a minimum of 5000 packets per second. Please refrain from increasing it beyond 5000 as it could lead to a DoS attack, which is not considered cool!
"-vvv": Displays verbose output, providing more detailed information. Press Enter during the scanning process to reveal additional details such as the percentage of completion.
"-n": Disables DNS resolution. This is not necessary for port scanning and can significantly increase the scanning time, potentially taking 2 to 3 minutes or more.
- "-Pn": Disables Host Discovery because it's not necessary. Similar to the "-n" parameter for disabling DNS resolution, this can expedite the scanning process, preventing unnecessary delays.
With all these parameters, you will perform a comprehensive TCP Port Scan quickly and safely.
Using NMap for UDP Port Scanning
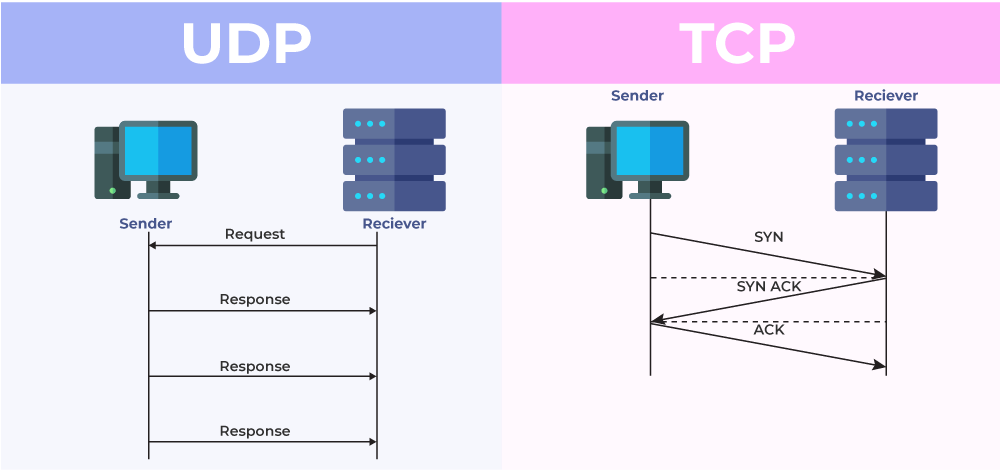
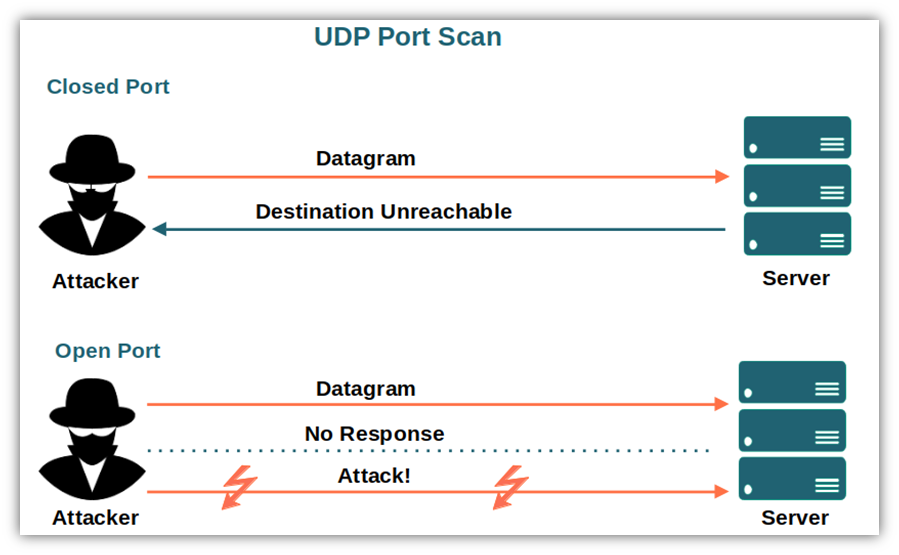
The UDP scanning process differs from TCP scanning in how the connection is established. While a TCP scan uses a three-way approach (SYN, SYN-ACK, ACK) to determine port openness, UDP scanning relies on sending datagrams.
During a UDP scan, NMap sends a UDP datagram to the destination port. If the port is open, the service may respond. However, if the port is closed, the system might respond with a "Destination Unreachable" message. The absence of a response could also indicate an open port or network filtering blocking the reply.
It's essential to note that UDP scanning can be less reliable than TCP scanning. This is because some systems and firewalls may not consistently respond to UDP datagrams, leading to potential false positives or negatives. Due to this, UDP scanning often involves more uncertainty and may require additional techniques to interpret results accurately.
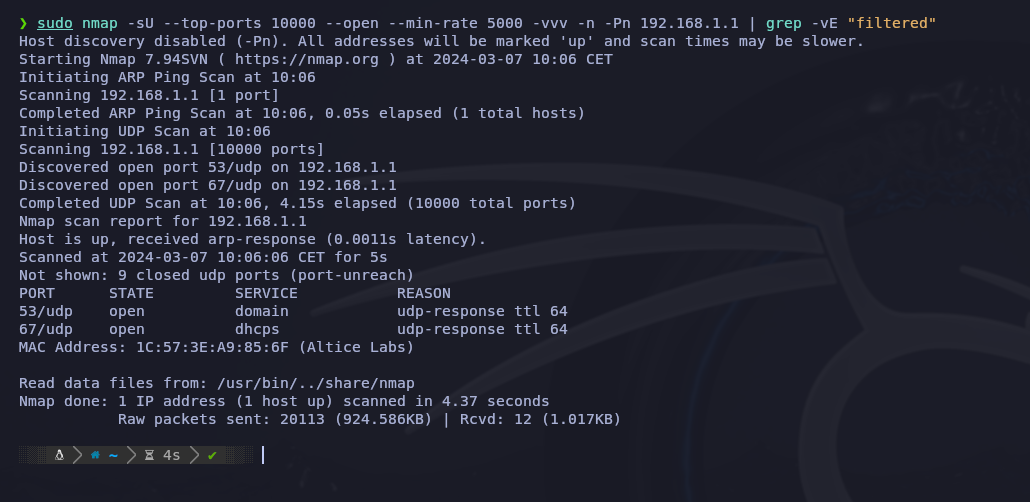
- sudo nmap -sU --top-ports 10000 --open --min-rate 5000 -vvv -n -Pn 192.168.1.1 | grep -vE "filtered"
Method #2: Using an Alternative Script
You can utilize a script that I've created to scan all TCP and UDP protocol ports swiftly, easily, and effectively!
It doesn't display false positives or negatives. It scans even faster than NMap and is more efficient, as it encompasses an all-in-one approach.
Link of Script: https://github.com/OusCyb3rH4ck/PortScan
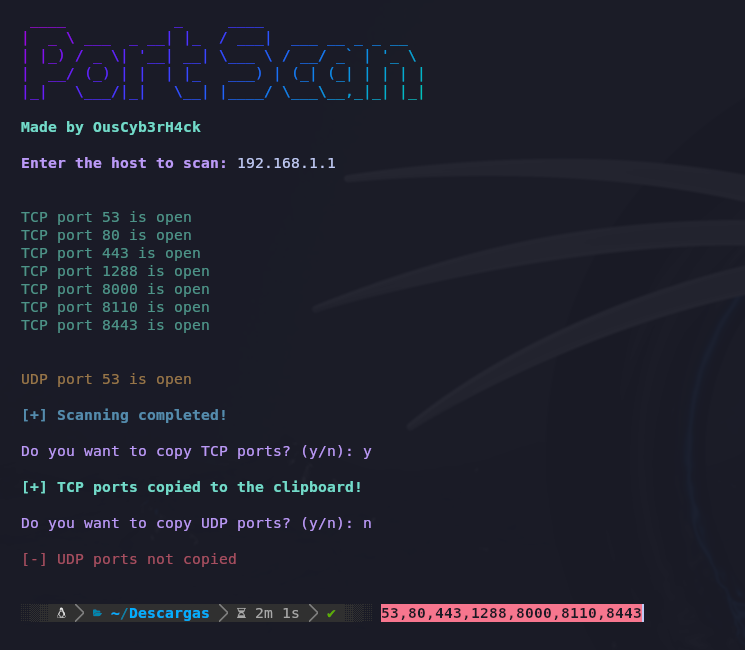
For installation, use the following commands:
- sudo apt-get update && sudo apt-get install -y python3-pip figlet lolcat && sudo apt update
- python3 -m pip install --upgrade colorama
- git clone https://github.com/OusCyb3rH4ck/PortScan
For using it:
- cd PortScan
- python3 PortScan.py
Conclusion
In conclusion, port scanning is an essential practice in the realm of cybersecurity and penetration testing. With established tools like NMap, we can explore and assess network security, identify running services, and detect potential vulnerabilities. While these tools are foundational, it's also exciting to explore new alternatives. In this context, I introduced a script that I've created for conducting fast, easy, and effective scans of all TCP and UDP ports—free from false positives or negatives. This script stands out for its speed and efficiency, providing a comprehensive solution for scanning and security evaluation activities. Always remember to conduct these actions ethically and in compliance with local regulations, acknowledging that knowledge and understanding are crucial for building safer digital environments.
Well, I hope it has been helpful for you, and see you in the next article. GOODBYE!
