Hacking APIs at Scale: Modern Techniques for Finding Vulnerabilities in Cloud Services

Welcome! In this article, we'll explore the fascinating world of API hacking at scale. As APIs power the backbone of modern cloud services, they've become a prime target for attackers. We'll dive into advanced techniques for finding and exploiting vulnerabilities, leveraging cutting-edge tools for large-scale testing, and exploring real-world examples. Whether you're an ethical hacker looking to sharpen your skills or a developer aiming to secure your applications, this guide will provide actionable insights to stay ahead in 2025's rapidly evolving cybersecurity landscape. Let's get started!
1. Introduction
APIs (Application Programming Interfaces) are the backbone of modern cloud services, enabling seamless communication between diverse systems, applications, and devices. As organizations increasingly depend on APIs to power their digital ecosystems, these interfaces have become a prime target for attackers. Exploiting vulnerabilities in APIs can lead to severe consequences, including data breaches, unauthorized access, and even complete system takeovers.
For ethical hackers, understanding how to identify and exploit API vulnerabilities is not just valuable—it's essential. This article highlights the importance of API security, the risks APIs pose, and why hacking APIs at scale has become a vital skill in today's rapidly evolving cybersecurity landscape.
2. Understanding API Vulnerabilities
APIs are a double-edged sword—they facilitate communication and functionality, but they also introduce unique attack surfaces. To secure them effectively, ethical hackers must understand the common vulnerabilities that can be exploited. Here are some of the most significant API weaknesses:
2.1 Common Types of API Vulnerabilities
- Authentication and Authorization Flaws: Weak or improperly implemented authentication mechanisms, such as missing OAuth configurations or insecure API keys, can allow unauthorized access.
- Rate-Limiting Issues: APIs without proper rate limiting can be abused for brute-force attacks or denial-of-service (DoS) attacks.
- Injection Attacks: APIs are often susceptible to SQL injection, NoSQL injection, and command injection, especially when user input is not sanitized.
- Broken Object Level Authorization (BOLA): A common issue where APIs do not properly validate user permissions, leading to unauthorized data access.
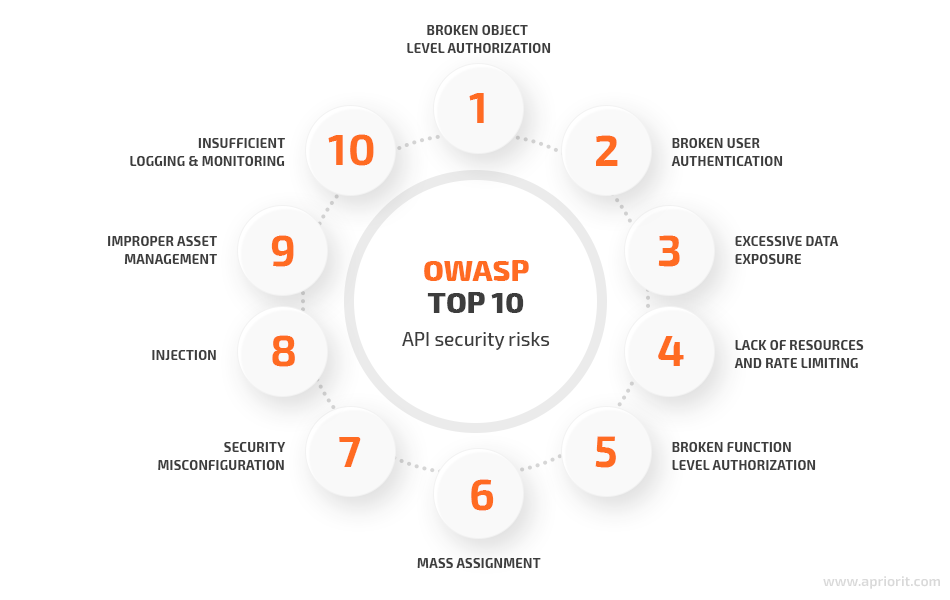
2.2 OWASP API Security Top 10 for 2025
The OWASP API Security Top 10 provides a framework for understanding and mitigating API vulnerabilities. Key issues include:
- Broken user authentication.
- Excessive data exposure.
- Security misconfigurations.
These evolving risks make it crucial to stay updated and implement secure API design principles.
2.3 Real-World Examples
- In recent years, API breaches in major platforms like Facebook and Twitter exposed millions of user records.

- Tesla's API vulnerability once allowed attackers to take control of vehicles remotely by exploiting weak endpoints.

Understanding these vulnerabilities not only helps in identifying potential weaknesses but also emphasizes the critical role of ethical hackers in safeguarding APIs.
3. Tools and Techniques for API Hacking
Ethical hackers leverage a variety of tools and techniques to identify vulnerabilities in APIs. A strong understanding of the tools available and how to use them effectively is crucial for both manual testing and automated scanning. Below, we explore some of the most powerful tools and methods for API security assessments.
3.1 Essential Tools for Ethical API Hacking
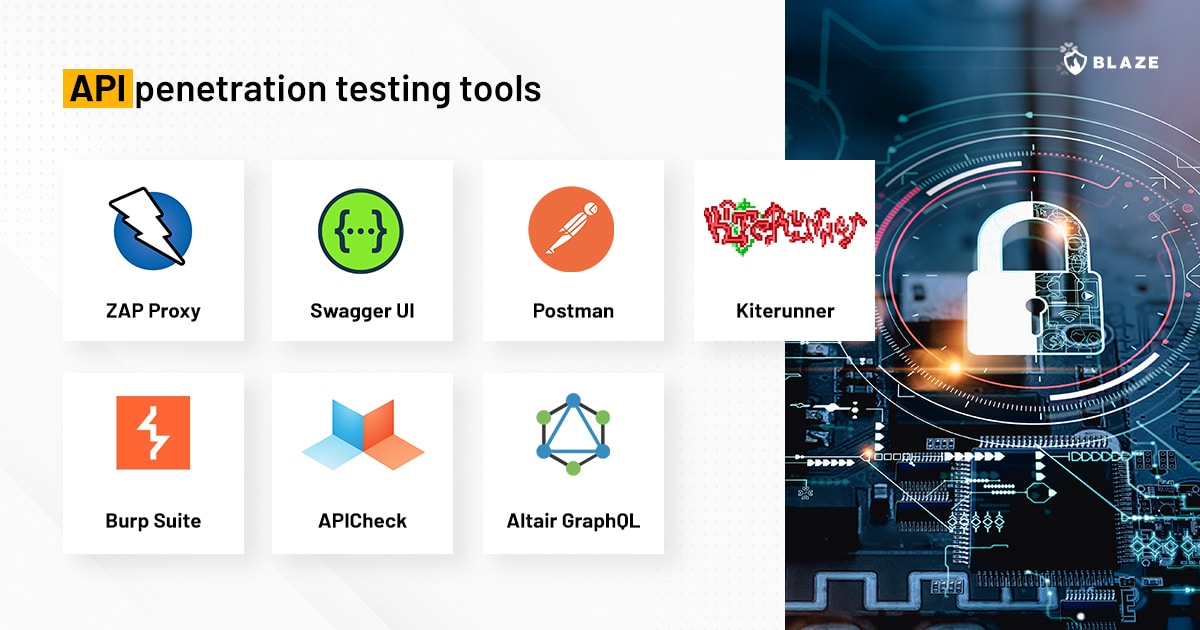
- Postman: A widely used tool for sending API requests, testing endpoints, and exploring API functionality. (Download here)
- BurpSuite: A robust framework for intercepting, modifying, and analyzing HTTP traffic, making it indispensable for testing API security. (Download here)
- OWASP ZAP (Zed Attack Proxy): A free, open-source tool ideal for scanning APIs for vulnerabilities. (Download here)
- Kiterunner: Specifically designed for fuzzing APIs at scale, Kiterunner can brute-force API endpoints efficiently. (Download here)
- Fuzzapi: Automates fuzzing for APIs and helps uncover hidden or misconfigured endpoints. (Download here)
3.2 Manual Testing Techniques
- Analyzing API Documentation: Often, vulnerabilities can be inferred from poorly written or overly permissive API documentation.
- Endpoint Discovery: Use tools like Kiterunner or directory brute-forcing to uncover hidden or undocumented endpoints.
- Reverse Engineering: Analyze mobile apps or JavaScript code to extract hardcoded API keys, tokens, or endpoint details.
3.3 Automating API Security Assessments
Automation is key to testing APIs at scale. Ethical hackers often write custom scripts using:
- Python with libraries like Requests: For crafting and sending API requests programmatically.
- Fuzzing frameworks: To simulate a variety of unexpected inputs and identify edge-case vulnerabilities.
- CI/CD Integration: Automated security scans using tools like OWASP ZAP can be integrated directly into CI/CD pipelines to ensure continuous testing.
3.4 The Importance of Context
Even with powerful tools, understanding the business logic of APIs is crucial. Vulnerabilities often arise from logic flaws that tools can't detect. Combining technical expertise with critical thinking allows ethical hackers to uncover deeper, less obvious issues.
4. Advanced Exploitation Techniques
When it comes to API hacking, advanced techniques allow ethical hackers to uncover deeper vulnerabilities that go beyond basic misconfigurations. These methods target the intricate workings of APIs, exploiting flaws in their logic, design, and implementation. Below are some of the most impactful advanced techniques in API exploitation:
4.1 API Chaining
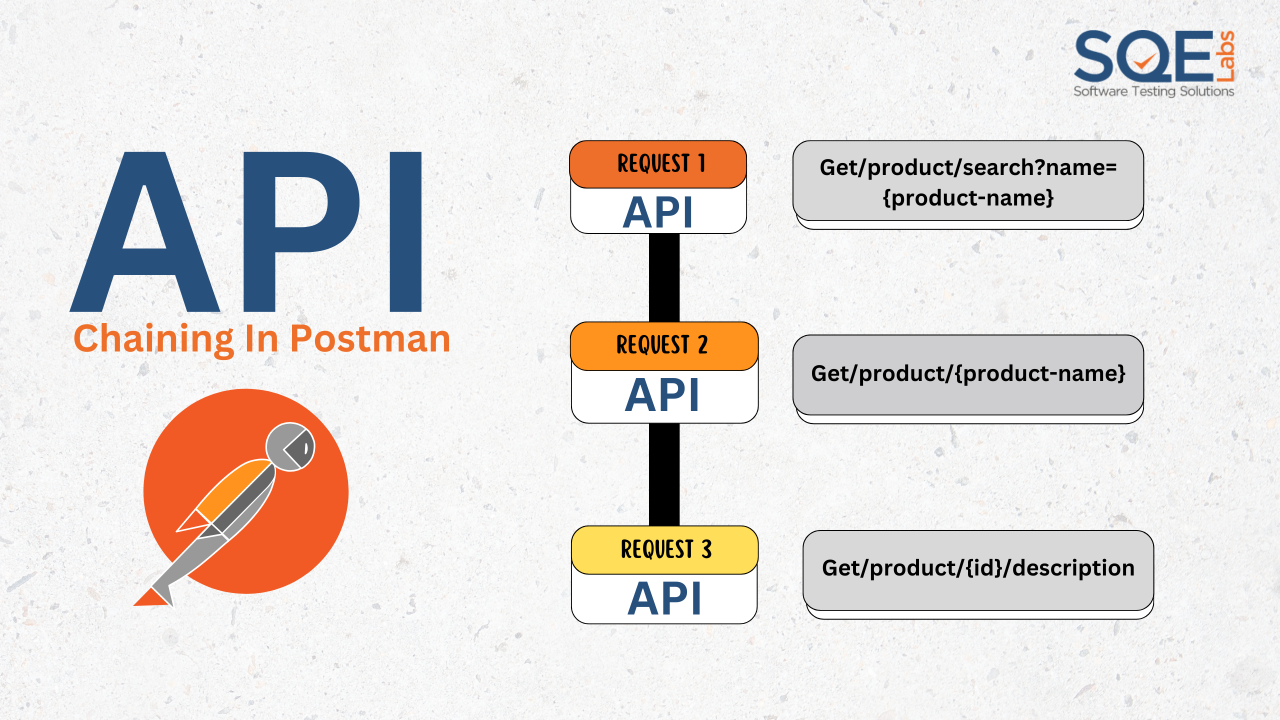
- What It Is: Exploiting multiple endpoints in a sequence to achieve higher-level access or functionality.
- Example: Using one endpoint to retrieve a user ID and another to escalate privileges, bypassing access controls.
- Why It Works: APIs often expose interconnected endpoints without properly validating user permissions across the chain.
4.2 Exploiting GraphQL APIs
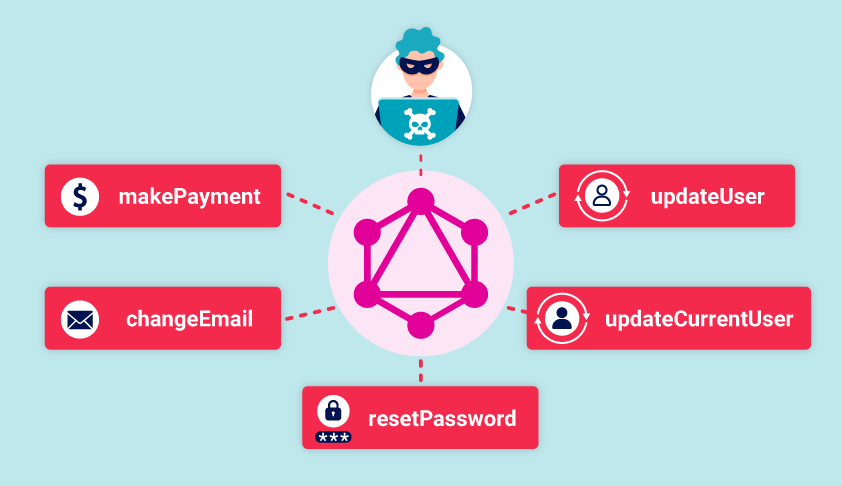
- Overfetching and Underfetching: GraphQL APIs allow users to specify exactly what data they want, which can inadvertently expose sensitive information.
- Overfetching Example: Requesting fields that should be restricted but are exposed due to overly permissive schema configurations.
- Underfetching Exploits: Leveraging insufficient checks to request specific data fragments that can be reassembled into sensitive information.
- Introspection Abuse: Using the GraphQL introspection query to map the API structure and identify weak points.
- Link on how to pentest GraphQL APIs: GraphQL API Vulnerabilities (PortSwigger)
4.3 Bypassing Rate Limits and Throttling
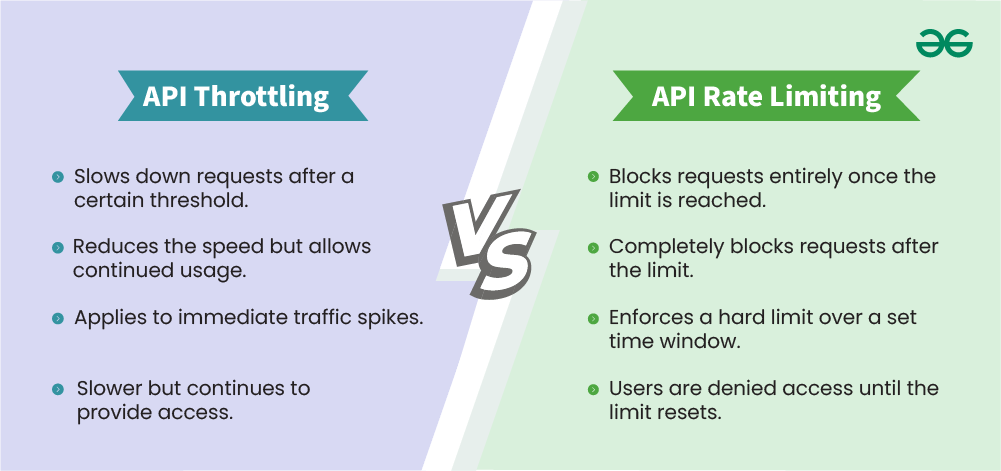
- How It Works:
- Rotate through a pool of IP addresses to evade rate-limiting mechanisms.
- Use multiple tokens or API keys to distribute requests.
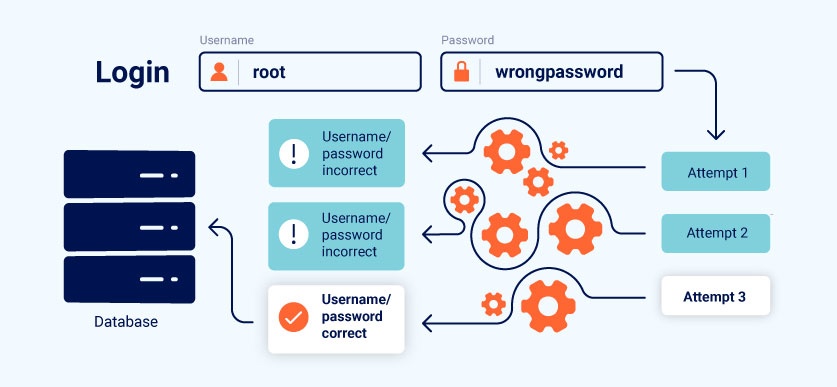
- Example: Conducting brute-force attacks on login endpoints without triggering alarms.
- Tool Highlight: Tools like Turbo Intruder (a Burp Suite extension) can automate high-speed requests.
4.4 Injection Attacks
APIs are prone to injection vulnerabilities, especially when user input isn't properly sanitized.
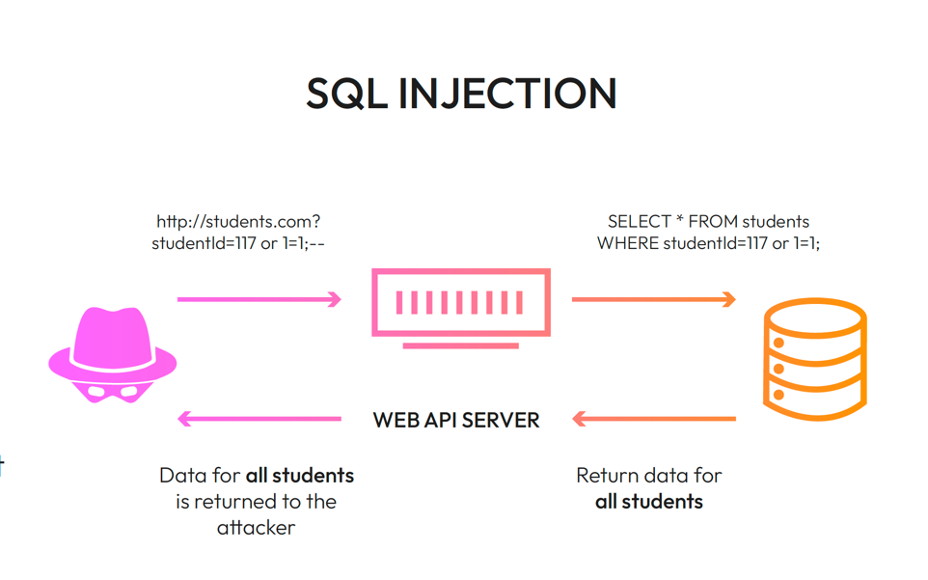
- SQL Injection: Exploit API endpoints that interact with databases by injecting malicious SQL queries.
- Command Injection: Leverage vulnerable endpoints to execute commands on the server.
- NoSQL Injection: Manipulate NoSQL queries in systems like MongoDB to gain unauthorized access.
4.5 Leveraging Flawed Business Logic
- What It Is: Exploiting APIs that fail to validate critical operations.
- Example: An e-commerce API allowing price modification during checkout could lead to unauthorized discounts.
- Why It Matters: These logic-based vulnerabilities often bypass automated tools and require deep understanding of the system.
4.6 Exploiting API Misconfigurations
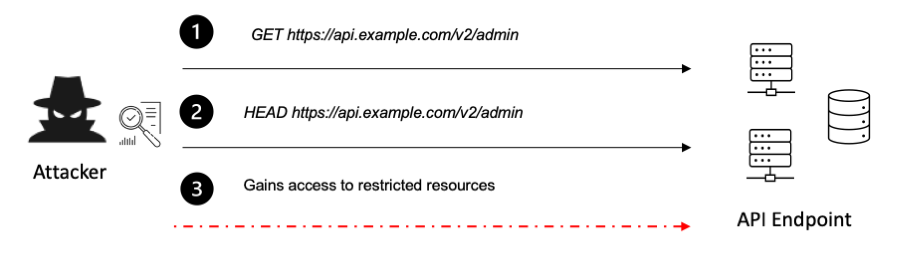
- Open Endpoints: Unauthenticated endpoints that expose sensitive data.
- Improper CORS Configurations: APIs with overly permissive Cross-Origin Resource Sharing (CORS) policies allow attackers to steal data from trusted domains.
5. API Hacking at Scale

In today's interconnected world, APIs are ubiquitous, and testing them individually isn't always practical. Ethical hackers must adopt strategies for large-scale API testing, leveraging automation and efficient data analysis techniques to uncover vulnerabilities across multiple endpoints simultaneously. Here's how API hacking can be scaled effectively:
5.1 Automation for Large-Scale Testing
Manual testing has its limitations, especially when dealing with hundreds or thousands of endpoints. Automation enables ethical hackers to test APIs at scale using:
- Custom Scripts: Languages like Python with libraries such as Requests and Asyncio allow rapid, parallelized testing of multiple endpoints.
- API Fuzzing Tools: Tools like Kiterunner and Fuzzapi can identify vulnerabilities in undocumented or rarely used endpoints by sending a wide range of inputs.
5.2 Endpoint discovery at Scale
- DNS Recon and Subdomain Enumeration: Use tools like Amass or Subfinder to discover new API endpoints across a target's infrastructure.
- Brute Forcing: Employ wordlists to uncover hidden or undocumented endpoints using tools like FFuF (Fuzz Faster U Fool) or DirBuster.
- Reverse Engineering: Analyze web apps, mobile apps, or API SDKs to extract endpoint details for further testing.
5.3 Managing Data from Large-Scale Tests
Testing APIs at scale generates a significant amount of data. Ethical hackers can manage this effectively by:
- Organizing Test Results: Using tools like Burp Suite's Collaborator or integrating results into platforms like Elasticsearch for centralized analysis.
- Prioritizing Issues: Sorting vulnerabilities by severity, focusing on high-impact issues such as authentication flaws or sensitive data exposure.
- Visualization Tools: Employing dashboards like Kibana to analyze trends and patterns across multiple endpoints.
5.4 Ethical Considerations and Avoiding DoS Attacks
Testing APIs at scale introduces the risk of unintentional Denial-of-Service (DoS) attacks, especially on production systems. To mitigate this:
- Limit Requests: Avoid overwhelming endpoints by spacing requests or testing in controlled environments.
- Respect Rate Limits: Abide by the target system's rate-limiting policies unless explicitly permitted to test for bypasses.
- Use Staging Environments: Whenever possible, request access to staging environments to perform large-scale testing safely.
5.5 The Importance of Documentation
After testing, documenting findings clearly is critical. Include:
- A detailed description of vulnerabilities discovered.
- Steps to reproduce the issues.
- Recommendations for remediation.
By scaling their efforts, ethical hackers can effectively assess the security of expansive API infrastructures, uncovering vulnerabilities that would otherwise remain hidden.
6. Securing APIs: Recommendations and Best Practices
Securing APIs is essential for preventing data breaches, unauthorized access, and other cyberattacks. Ethical hackers not only identify vulnerabilities but also provide actionable recommendations to strengthen API defenses. In this section, we'll explore best practices and security measures that can mitigate risks and protect APIs from exploitation.
6.1 Implement Strong Authentication and Authorization
- OAuth 2.0 and OpenID Connect: These protocols help ensure that only authorized users can access sensitive API endpoints. OAuth 2.0, in particular, allows for secure token-based authentication, reducing the reliance on credentials.
- JWT (JSON Web Tokens): Implementing JWTs ensures that the information contained in tokens is securely verified, preventing unauthorized access.
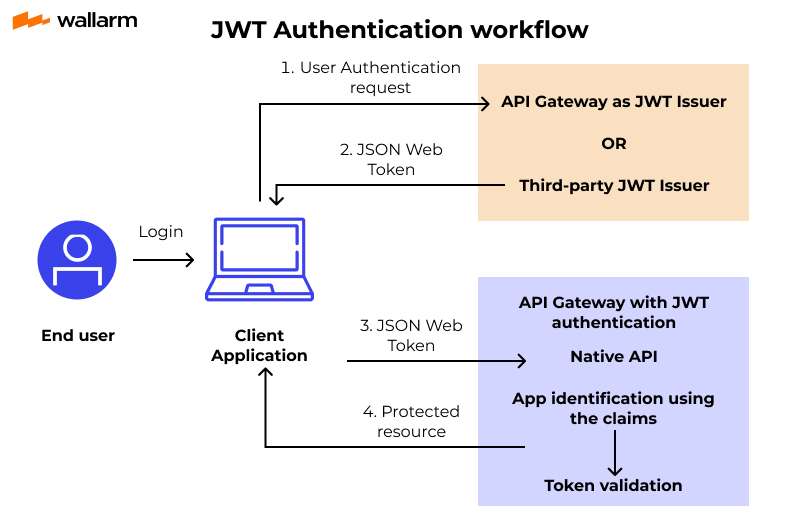
- Multi-Factor Authentication (MFA): Adding an extra layer of protection, MFA can significantly reduce the risk of unauthorized API access by requiring users to provide additional verification.
6.2 Protect APIs with Rate Limiting and Throttling
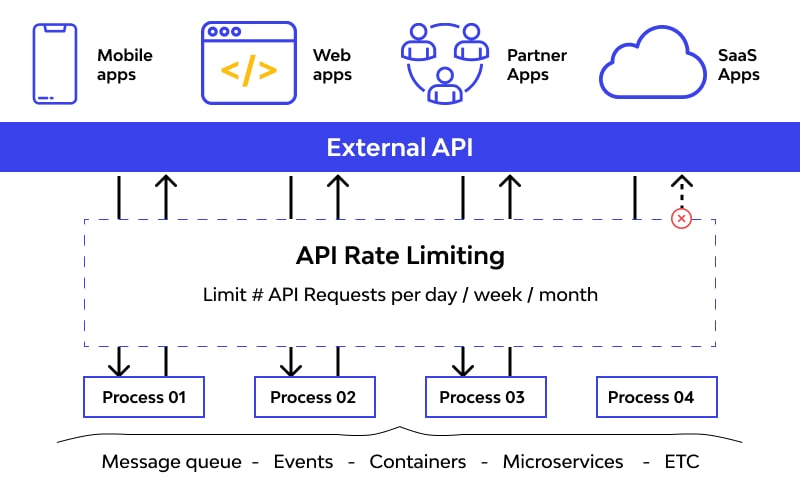
- Rate Limiting: Set limits on the number of requests an IP or user can make in a specific time frame (e.g., 100 requests per minute). This prevents DoS attacks and brute-force attempts.
- API Gateway Configuration: Use API gateways to enforce rate limits and provide extra security layers, such as input validation and traffic monitoring.
- Dynamic Throttling: Implement adaptive throttling based on traffic patterns and endpoint criticality, ensuring that high-traffic periods do not overwhelm the system.
6.3 Employ Input Validation and Output Encoding
- Input Validation: Validate all incoming data to ensure it meets predefined formats, rejecting any requests with invalid or malformed data. This prevents injection attacks, like SQL injection and NoSQL injection.
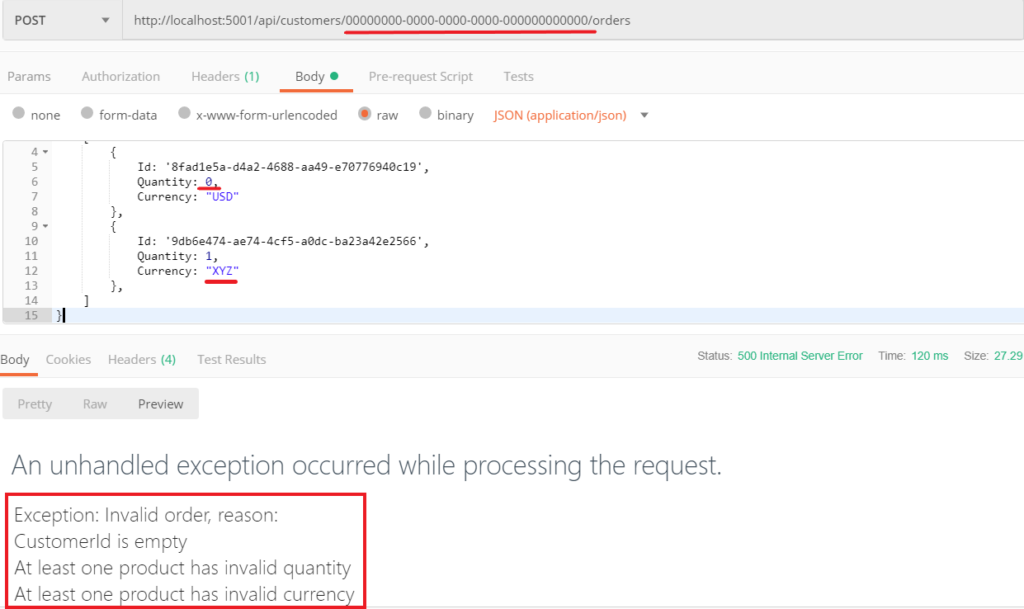
- Output Encoding: Encode outputs before sending them to clients to prevent data manipulation or malicious code execution (e.g., XSS attacks).
6.4 Use API Gateways for Centralized Security Management
API gateways can serve as a centralized point of control, enforcing security measures across multiple services.
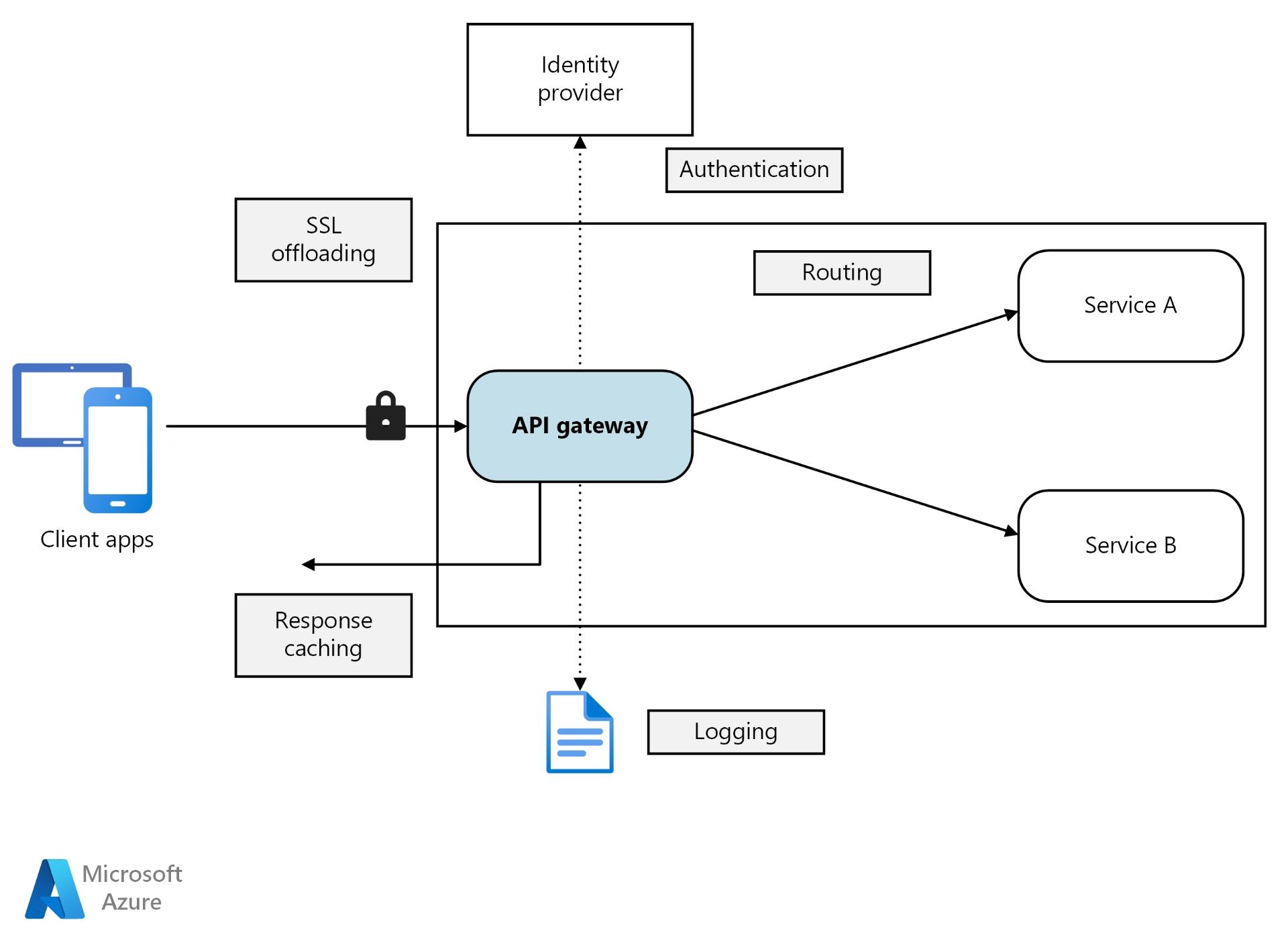
- Access Control: Use gateways to enforce authentication and authorization for all incoming API requests.
- Traffic Inspection: Gateways can inspect and filter traffic, blocking malicious requests before they reach your API endpoints.
- Centralized Logging and Monitoring: Gateways often provide centralized logging, allowing for better visibility into traffic patterns and helping to detect unusual or suspicious activity.
6.5 Secure Data Transmission with Encryption
- TLS/SSL: Ensure that all API communication is encrypted using TLS (Transport Layer Security) to protect data in transit from interception or tampering.
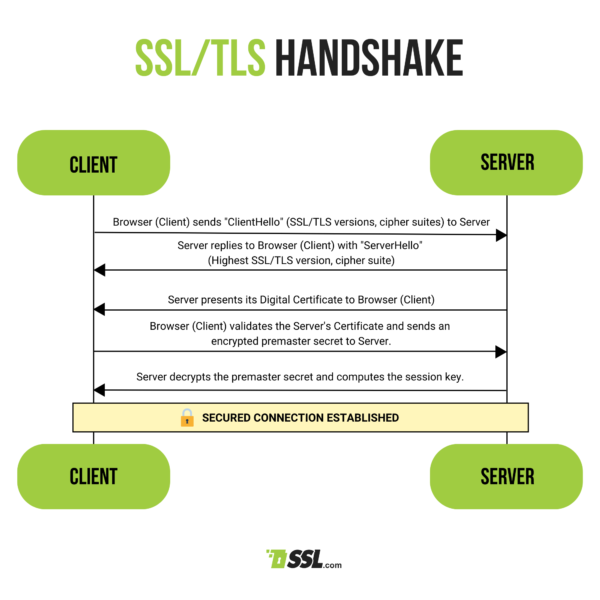
- End-to-End Encryption: For sensitive APIs, consider implementing end-to-end encryption to ensure that even if the data is intercepted, it cannot be read or altered.
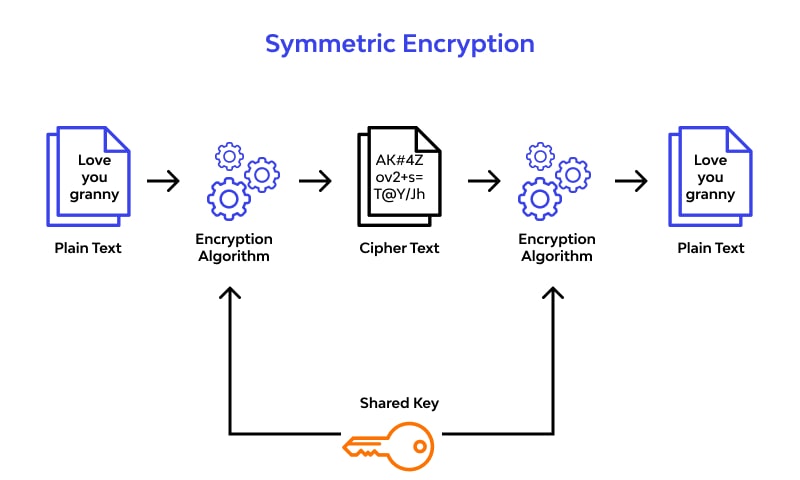
6.6 Apply Least Privilege Access
- Granular Permissions: Limit access to API resources based on the principle of least privilege. Only allow users and services to access the data or functions necessary for their role.
- Role-Based Access Control (RBAC): Implement RBAC to manage user permissions, ensuring that users only have access to the specific APIs and data they need.
6.7 Perform Regular Security Audits and Penetration Testing
- Automated Scanning: Integrate automated security tools such as OWASP ZAP or Burp Suite into your CI/CD pipeline to detect vulnerabilities early.
- Manual Penetration Testing: Even with automated tools, conducting regular manual penetration tests allows you to uncover complex business logic flaws and deep-seated vulnerabilities.
6.8 Implement Logging, Monitoring, and Incident Response
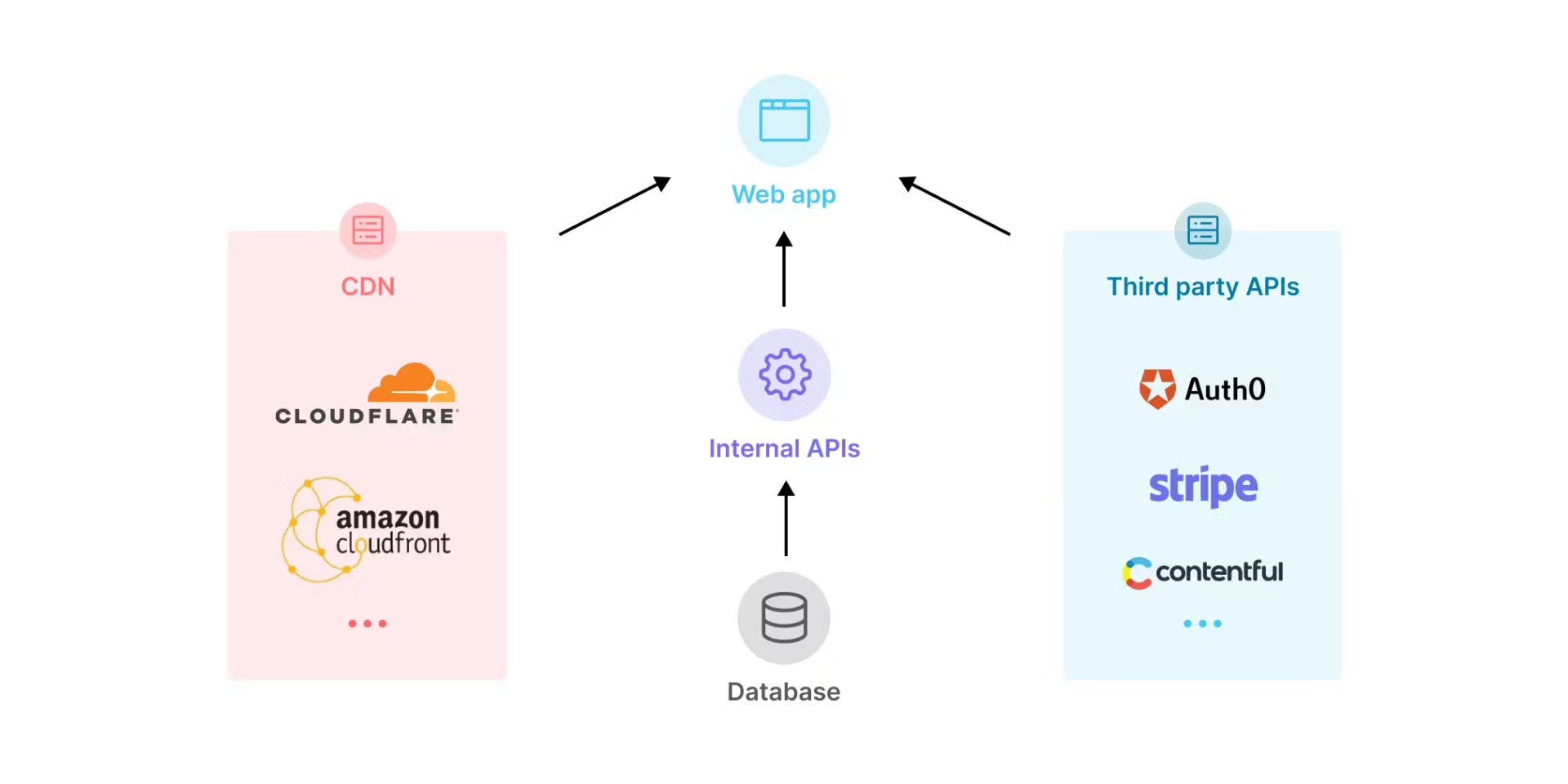
- Centralized Logging: Collect logs from all API endpoints in a centralized location, allowing for easier analysis and quicker detection of suspicious activities.
- Monitoring: Set up real-time monitoring to detect abnormal traffic patterns, failed authentication attempts, and other indicators of compromise.
- Incident Response Plan: Have a well-defined incident response plan to quickly address any security breaches or vulnerabilities detected.
7. Conclusion
As we've explored throughout this article, APIs have become the cornerstone of modern digital infrastructures, but they also present a growing attack surface. Ethical hackers play a pivotal role in identifying and mitigating vulnerabilities, from basic authentication flaws to advanced logic-based exploits. By understanding the tools, techniques, and best practices for API security, professionals can help organizations better protect their systems and data.
To secure APIs effectively, it's essential to implement a combination of strong authentication, rate-limiting, input validation, and encryption. Coupled with regular penetration testing, automated scanning, and incident response plans, these strategies form a robust defense against the ever-evolving threat landscape.
As the security world continues to evolve with new challenges and technologies, ethical hackers must remain vigilant and proactive, always refining their skills and knowledge. By staying up to date with best practices and emerging threats, we can continue to strengthen the security of APIs and the broader digital ecosystem.
Thank you for reading! We hope this guide has provided valuable insights into the world of API hacking and security. Stay safe, stay aware, and we'll see you in the next article!
