Ethical Hacking in the IoT (Internet of Things) Era
The Internet of Things (IoT) has transformed the way we interact with technology, embedding connectivity into everyday objects from household appliances to industrial machinery. While IoT devices offer unparalleled convenience and efficiency, they also bring significant security challenges. With the proliferation of connected devices, the potential attack surface for malicious actors has expanded exponentially. In this article, we delve into the realm of ethical hacking within the IoT landscape, exploring methodologies, tools, legal considerations, and best practices essential for safeguarding IoT devices and networks.
Common Vulnerabilities in IoT Devices:
The widespread adoption of IoT devices has brought forth a myriad of security vulnerabilities, posing significant risks to both individuals and organizations. These vulnerabilities manifest in various forms, ranging from weak authentication mechanisms to insecure communication protocols and inadequate software patching processes.
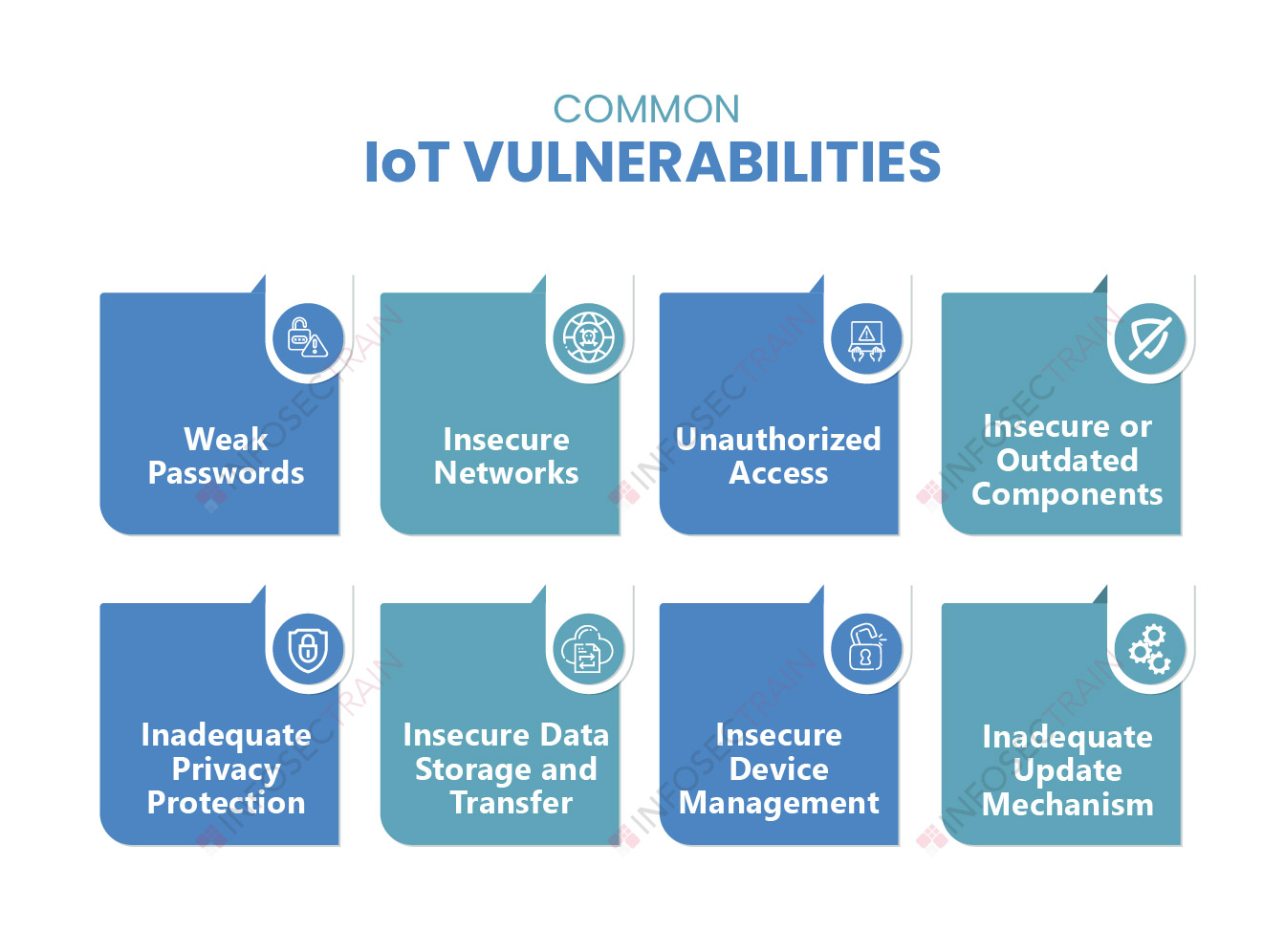
One common vulnerability in IoT devices is the lack of robust authentication mechanisms. Many devices utilize default or easily guessable credentials, making them susceptible to brute-force attacks. Additionally, insecure communication protocols, such as HTTP or MQTT without proper encryption, expose sensitive data to eavesdropping and manipulation by malicious actors.
Furthermore, IoT devices often lag behind in terms of software updates and patches, leaving them vulnerable to known exploits and vulnerabilities. Manufacturers may not prioritize security updates, leaving devices unprotected against emerging threats.
Recent incidents have highlighted the severity of these vulnerabilities, with hackers exploiting flaws in smart cameras, thermostats, and even medical devices. These breaches not only compromise user privacy but also pose risks to public safety and critical infrastructure.
Addressing these vulnerabilities requires a concerted effort from manufacturers, developers, and end-users to prioritize security in IoT deployments. By identifying and mitigating common vulnerabilities, ethical hackers play a crucial role in fortifying the security posture of IoT devices and networks.
Ethical Hacking Methodologies in IoT Devices:
Ethical hackers employ a variety of methodologies to uncover vulnerabilities in IoT devices, aiming to preemptively identify weaknesses before malicious actors exploit them. These methodologies encompass a range of techniques, including network sniffing, protocol analysis, reverse engineering, and firmware analysis.
Network sniffing: Ethical hackers utilize network sniffing tools to intercept and analyze data packets transmitted between IoT devices and their associated networks. By monitoring network traffic, they can identify potential vulnerabilities such as unencrypted communication or suspicious data patterns.
Protocol analysis: Ethical hackers scrutinize the communication protocols used by IoT devices to understand how data is transmitted and processed. This analysis may involve dissecting proprietary protocols or reverse engineering standardized protocols to identify weaknesses or deviations from best practices.
Reverse engineering: Ethical hackers employ reverse engineering techniques to deconstruct and analyze the firmware and software running on IoT devices. By examining executable binaries, firmware images, and configuration files, they can uncover hidden vulnerabilities or backdoors inadvertently left by developers.
Firmware analysis: Ethical hackers delve deep into the firmware of IoT devices to identify vulnerabilities and security flaws. This may involve extracting firmware images, analyzing file systems, and auditing code for common vulnerabilities such as buffer overflows, injection attacks, or insecure cryptographic implementations.
Through these methodologies, ethical hackers simulate real-world attack scenarios to assess the security posture of IoT devices comprehensively. By identifying vulnerabilities and providing actionable recommendations for remediation, ethical hacking plays a crucial role in enhancing the resilience of IoT deployments against cyber threats.
Essential Tools for Security Assessment in IoT:
A plethora of specialized tools are available to ethical hackers for assessing the security of IoT devices, facilitating comprehensive security assessments across various layers of the IoT stack. These tools encompass a wide range of functionalities, including network scanning, packet analysis, firmware extraction, and vulnerability scanning.
Network scanners: Tools like Nmap and ZMap enable ethical hackers to discover and enumerate IoT devices within a network, identifying open ports, services, and potential attack vectors. By conducting network scans, ethical hackers gain insights into the topology and security posture of IoT deployments.
Packet analyzers: Wireshark and tcpdump are popular packet analysis tools that allow ethical hackers to capture and analyze network traffic in real-time. By inspecting packet payloads and headers, ethical hackers can identify anomalies, detect malicious activities, and uncover vulnerabilities such as unencrypted communication or injection attacks.
Firmware extraction utilities: Binwalk and Firmware Analysis Toolkit (FAT) facilitate the extraction and analysis of firmware images from IoT devices. These tools enable ethical hackers to dissect firmware files, extract file systems, and identify embedded binaries or configuration files containing potential vulnerabilities or backdoors.
Vulnerability scanners: Tools like Nessus and OpenVAS automate the process of identifying known vulnerabilities in IoT devices and their associated software components. By scanning devices for common vulnerabilities such as outdated software versions, misconfigurations, or weak authentication mechanisms, ethical hackers can prioritize remediation efforts effectively.
These tools empower ethical hackers to conduct thorough security assessments of IoT devices and networks, enabling them to identify vulnerabilities, assess the overall security posture, and provide actionable recommendations for improving security. However, it's crucial to use these tools responsibly and ethically, ensuring compliance with legal and regulatory requirements throughout the security assessment process.
Legal and Ethical Considerations in Ethical Hacking of IoT Devices:
Ethical hacking activities must adhere to strict legal and ethical guidelines to ensure compliance and protect stakeholders' interests. Researchers must obtain explicit permission from device owners before conducting security assessments. Moreover, ethical hackers must exercise caution to avoid causing disruption or damage to IoT devices and networks during testing. Adhering to these principles fosters trust and collaboration between ethical hackers and IoT stakeholders.
Conducting ethical hacking activities without proper authorization can have serious legal ramifications, potentially leading to civil liabilities or criminal charges. Therefore, it's essential for ethical hackers to establish clear rules of engagement with device owners and obtain written consent before commencing security assessments. Additionally, ethical hackers should maintain detailed documentation of their activities, including methodologies used, vulnerabilities discovered, and remediation recommendations provided.
Furthermore, ethical hackers must ensure that their actions align with established ethical standards and professional codes of conduct. This includes respecting user privacy, avoiding the exploitation of vulnerabilities for personal gain, and prioritizing the public interest in disclosing security findings responsibly.
By upholding these legal and ethical principles, ethical hackers can contribute to the advancement of IoT security while safeguarding the rights and interests of all parties involved. Effective collaboration between ethical hackers, device manufacturers, and regulatory authorities is essential for fostering a culture of transparency, accountability, and trust in the realm of IoT security.
Best Practices for Securing IoT Devices:
Securing IoT devices requires a multifaceted approach encompassing device manufacturers, software developers, and end-users. Manufacturers should prioritize security by implementing robust authentication mechanisms, encrypting communication channels, and providing timely firmware updates. Developers must adhere to secure coding practices and conduct thorough security assessments throughout the software development lifecycle. End-users play a crucial role in securing IoT devices by regularly updating firmware, changing default passwords, and segmenting IoT networks from critical systems.

Manufacturers: Implement robust authentication mechanisms to prevent unauthorized access to devices. Encrypt communication channels using strong encryption algorithms to protect data in transit. Provide timely firmware updates to patch known vulnerabilities and address emerging threats. Incorporate security-by-design principles into the development process to minimize the attack surface of IoT devices.
Developers: Adhere to secure coding practices such as input validation, output encoding, and parameterized queries to mitigate common vulnerabilities like injection attacks and buffer overflows. Conduct thorough security assessments throughout the software development lifecycle, including code reviews, static analysis, and dynamic testing. Implement secure update mechanisms to ensure the integrity and authenticity of firmware updates.
End-users: Regularly update firmware to patch known vulnerabilities and protect against emerging threats. Change default passwords to unique, complex passwords to prevent unauthorized access. Segment IoT networks from critical systems to limit the impact of potential breaches. Educate users about the importance of IoT security and provide guidance on best practices for securing devices.
By following these best practices, stakeholders can enhance the security of IoT devices and mitigate the risks associated with IoT deployments. Collaboration between manufacturers, developers, and end-users is essential for creating a robust and resilient IoT ecosystem that prioritizes security and privacy.
The Future of IoT Security and Pending Challenges:
As the IoT ecosystem continues to evolve, so too do the security challenges it presents. The proliferation of interconnected devices introduces complex attack vectors and amplifies the potential impact of security breaches. Addressing these challenges requires ongoing collaboration between security researchers, industry stakeholders, and regulatory bodies.
Emerging technologies such as artificial intelligence (AI) and blockchain offer promising avenues for enhancing IoT security. AI-powered threat detection systems can analyze vast amounts of data to identify anomalous behavior and detect potential security threats in real-time. Blockchain technology, with its immutable ledger and decentralized architecture, holds the potential to enhance the integrity and transparency of IoT data transactions, reducing the risk of tampering and unauthorized access.
However, mitigating future threats necessitates a proactive approach grounded in robust security practices and continuous innovation. Ethical hackers will play a crucial role in this endeavor, leveraging their expertise to uncover vulnerabilities, develop countermeasures, and enhance the overall security posture of IoT deployments.
Moreover, regulatory initiatives such as IoT security standards and certification programs can help establish baseline security requirements and incentivize compliance among manufacturers and developers. By setting clear guidelines and promoting accountability, regulatory bodies can create a more secure and trustworthy IoT ecosystem for consumers and businesses alike.
In conclusion, the future of IoT security holds both promise and challenges. By embracing emerging technologies, fostering collaboration, and prioritizing security at every stage of the IoT lifecycle, we can build a safer and more resilient IoT ecosystem that empowers innovation while safeguarding privacy and security.
Conclusion:
In conclusion, ethical hacking plays a pivotal role in safeguarding IoT devices and networks against evolving cyber threats. By adopting ethical hacking methodologies, stakeholders can proactively identify and address vulnerabilities, thereby fortifying the resilience of IoT deployments.
The interconnected nature of IoT devices introduces unique security challenges, including weak authentication mechanisms, insecure communication protocols, and inadequate software patching processes. However, by leveraging ethical hacking techniques such as network sniffing, protocol analysis, and firmware analysis, security professionals can identify and mitigate these vulnerabilities before they are exploited by malicious actors.
Furthermore, adherence to legal and ethical considerations is paramount in conducting ethical hacking activities. Obtaining explicit permission from device owners, avoiding disruption or damage to IoT devices and networks, and respecting user privacy are essential principles that ethical hackers must uphold.
Looking ahead, collaboration between ethical hackers, device manufacturers, regulatory bodies, and end-users will be crucial in addressing the future challenges of IoT security. Emerging technologies like artificial intelligence and blockchain offer promising solutions, but proactive security measures and regulatory initiatives are equally important in creating a safer and more trustworthy IoT ecosystem.
In summary, ethical hacking in the IoT era is not just about identifying vulnerabilities; it's about proactively securing the devices and networks that power our connected world. By embracing ethical hacking practices and working together, we can build a future where IoT devices empower innovation while prioritizing security and privacy for all.
