Ensuring Security in Consumer Bluetooth Devices: Tips to Protect Your Data

Bluetooth is useful and beneficial, and it has been revolutionary in recent generations. From the ability to send files from one device to another to controlling appliances like washing machines or electric scooters using Bluetooth technology, it is one of the most useful features of this current era. However, as always, there are risks that we must take precautions against.
What are Consumer Bluetooth Devices?
Bluetooth technology has revolutionized the way we interact with electronic devices, enabling seamless wireless communication over short distances. Consumer Bluetooth devices encompass a wide range of gadgets that leverage this technology to enhance convenience and connectivity. From wireless headphones and speakers to fitness trackers and smart home devices, Bluetooth has become integral to the functionality of numerous consumer electronics.
The versatility and ubiquity of Bluetooth devices make them indispensable in modern life. They offer users the freedom to stream audio, share files, track fitness metrics, and control smart home appliances without the constraints of wired connections. As such, Bluetooth technology has permeated various aspects of our daily routines, facilitating a more streamlined and efficient user experience.
Over the years, Bluetooth technology has undergone significant evolution and innovation to meet the ever-changing demands of consumers. Advancements in hardware and software have led to improvements in range, speed, and energy efficiency, enabling a broader array of applications and functionalities. Additionally, the integration of Bluetooth Low Energy (BLE) technology has paved the way for the proliferation of connected devices in the Internet of Things (IoT) ecosystem.
Associated Security Risks

Bluetooth technology offers numerous benefits in terms of convenience and connectivity, but it also introduces certain security risks that users should be aware of. Understanding these risks is crucial for ensuring the protection of sensitive data and maintaining the integrity of Bluetooth-enabled devices.
Several potential threat scenarios pose risks to the security of consumer Bluetooth devices. These include unauthorized access, data interception, and device manipulation by malicious actors. By exploiting vulnerabilities in Bluetooth protocols or leveraging social engineering tactics, attackers can compromise the confidentiality, integrity, and availability of information transmitted via Bluetooth connections.
The consequences of security breaches involving Bluetooth devices can be significant. In addition to the loss or theft of sensitive data, compromised devices may be used as entry points to launch further attacks on other devices or networks. Moreover, the reputational damage inflicted on manufacturers and brands can have long-lasting effects on consumer trust and confidence in Bluetooth technology.
Tips to Protect Your Bluetooth Devices
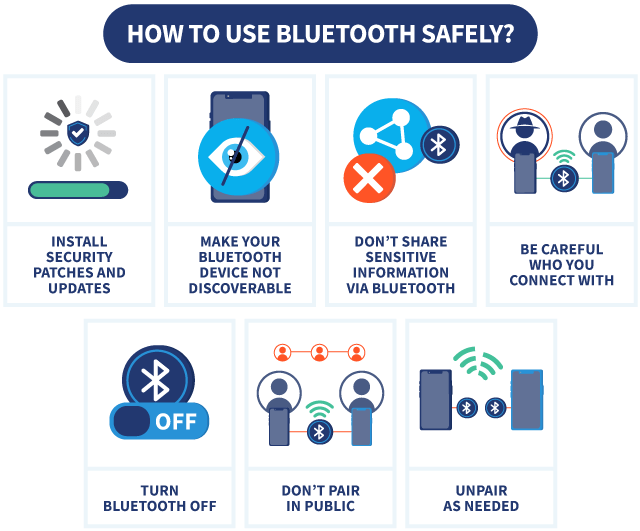
Keeping Firmware Updated
It is crucial to regularly update the firmware of your Bluetooth devices to ensure that they are equipped with the latest security patches and bug fixes. Manufacturers often release updates to address known vulnerabilities and enhance the security of their products. By staying up-to-date with firmware updates, you can reduce the risk of exploitation by malicious actors seeking to exploit outdated software.
Using Strong Passwords
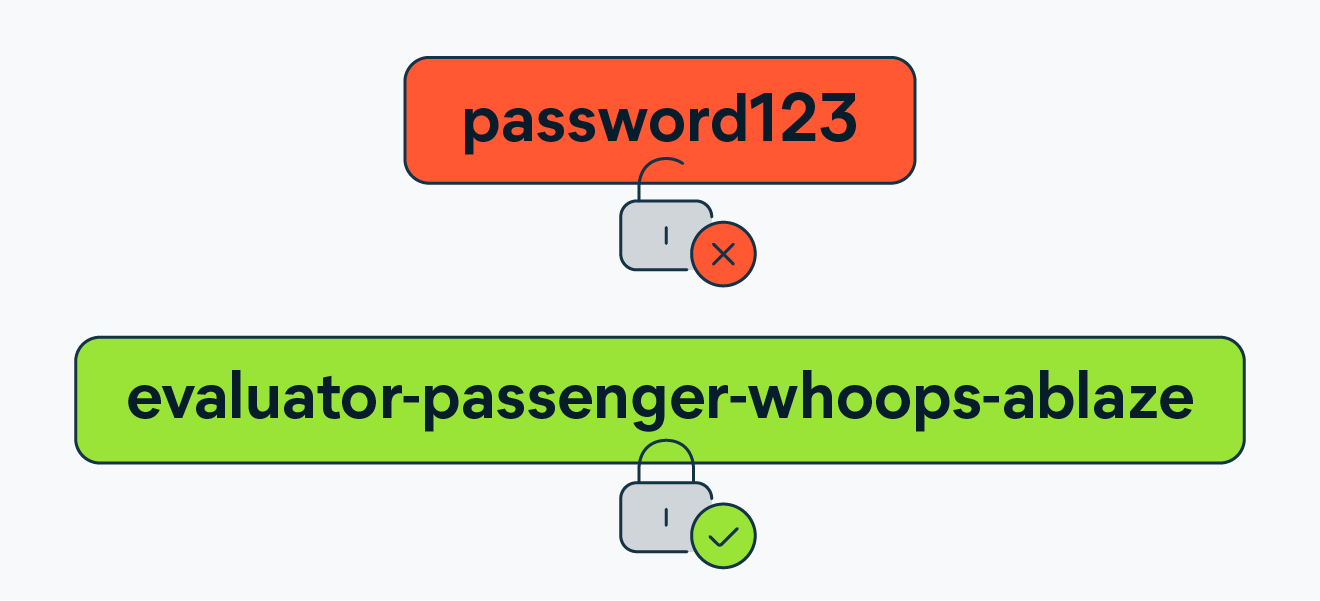
When setting up your Bluetooth devices, be sure to use strong and unique passwords to protect them from unauthorized access. Avoid using default or easily guessable passwords, as these can make your devices vulnerable to brute-force attacks. Choose complex passwords that include a combination of letters, numbers, and special characters, and consider using a password manager to securely store and manage your credentials.
Limiting Device Visibility
To minimize the risk of unauthorized connections, consider limiting the visibility of your Bluetooth devices by disabling their discoverability settings when not in use. This prevents them from being detected by nearby devices that may attempt to establish a connection without your permission. By keeping your devices hidden from view, you can reduce the likelihood of potential security breaches.
Implementing Secure Pairing Methods
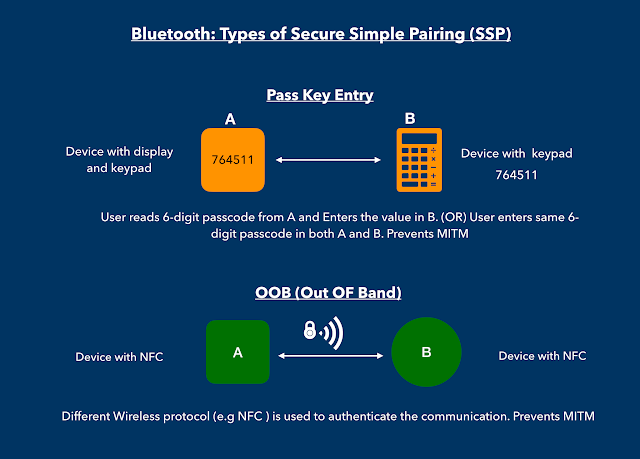
When pairing your Bluetooth devices with other devices, use secure pairing methods such as passkey authentication or numeric comparison to ensure the legitimacy of the connection. These methods require users to confirm the pairing process by entering a PIN code or verifying a numeric code displayed on both devices. By implementing secure pairing, you can prevent unauthorized devices from gaining access to your Bluetooth-enabled devices.
Disabling Unused Features

Disable any Bluetooth features or functionalities that are not essential to your needs to reduce the attack surface of your devices. For example, if you rarely use file transfer or audio streaming capabilities, consider disabling them to minimize the risk of potential security vulnerabilities. By deactivating unused features, you can limit the potential avenues for exploitation by malicious actors.
Monitoring Active Connections

Regularly monitor the active Bluetooth connections on your devices to detect any unauthorized or suspicious activity. Check the list of connected devices and ensure that they are all legitimate and authorized to access your Bluetooth-enabled devices. If you notice any unfamiliar connections or unexpected behavior, take immediate action to investigate and mitigate the potential security threat.
Using Security Solutions
Consider using specialized security solutions such as Bluetooth firewalls or mobile antivirus software to protect your devices from Bluetooth-based attacks. These solutions can help detect and block malicious activities, such as unauthorized access attempts or data interception, and provide additional layers of defense against potential security threats. Be sure to research and choose reputable security solutions that are compatible with your devices and meet your specific security needs.
User Education
Educating users about the importance of security practices when using Bluetooth devices is essential for mitigating potential risks and vulnerabilities. By raising awareness about common threats and providing guidance on best practices, users can take proactive measures to protect their devices and personal information.

Recognizing Security Threats
Users should be able to recognize common security threats associated with Bluetooth technology, such as unauthorized access, data interception, and device manipulation. By understanding the potential risks, users can be more vigilant in identifying suspicious activity and taking appropriate action to address potential security breaches.
Practicing Secure Behavior
Encouraging users to practice secure behavior when using Bluetooth devices is key to minimizing the risk of security incidents. This includes avoiding public Wi-Fi networks when transferring sensitive data via Bluetooth, being cautious when accepting pairing requests from unknown devices, and regularly reviewing and updating device settings to ensure optimal security.
Staying Informed
Keeping users informed about the latest security updates, vulnerabilities, and best practices is essential for maintaining a proactive approach to Bluetooth security. Providing regular updates and resources, such as security bulletins, user guides, and online tutorials, can empower users to stay informed and take appropriate action to protect their devices and data.
Promoting Responsible Usage
Promoting responsible usage of Bluetooth devices involves emphasizing the importance of using them in a secure and ethical manner. This includes respecting the privacy and security of others by obtaining consent before attempting to connect to their devices, avoiding unauthorized access to sensitive information, and adhering to applicable laws and regulations governing Bluetooth usage.
Encouraging Reporting of Security Incidents
Encouraging users to report any security incidents or suspicious activity involving Bluetooth devices is essential for identifying and addressing potential threats in a timely manner. Establishing clear reporting procedures and providing channels for users to report security incidents can facilitate prompt investigation and remediation of security breaches.
Conclusion
In this era of wireless connectivity, consumer Bluetooth devices have enhanced our daily lives by providing convenience and versatility. However, along with these advantages come significant security risks that cannot be ignored. It is crucial for users to understand these risks and take proactive measures to protect their devices and data.
By following security best practices such as keeping firmware updated, using strong passwords, and limiting device visibility, users can reduce the likelihood of experiencing a security incident. Furthermore, user education and awareness about the risks associated with using Bluetooth devices are essential for mitigating potential threats.
Ultimately, security in consumer Bluetooth devices is a shared responsibility among manufacturers, software developers, and users themselves. By working together to address security challenges and promote a safer Bluetooth ecosystem, we can enjoy the benefits of technology without compromising privacy and security.
As we wrap up our discussion on Bluetooth security, remember to stay vigilant and proactive in safeguarding your devices and data. By implementing the tips and best practices outlined in this article, you can enhance the security of your Bluetooth devices and minimize the risk of security breaches.
Thank you for joining us on this journey. We'll see you in the next installment as we continue to explore the ever-evolving landscape of cybersecurity and technology.
